Top 9 Vendor Risk Management Software for Infosec Pros in 2023
No single organization can master all trades, which is why their success hinges heavily on their vendors. And if vendors are crucial for your business operations,
Infrastructure as code (IaC) has become the de-facto method for dealing with infrastructure at scale. This codification of infrastructure configurations lets software development teams create version-controlled, reusable configurations. Moreover, it enables integrating infrastructure management as a part of the delivery pipeline.
Terraform and Ansible are two leading IaC tools with somewhat overlapping functionality. However, both of them aim to cater to specific infrastructure management requirements. It can be confusing to distinguish between these two tools and select the exact tool that matches your needs due to the similarity of their functionality. So in this blog, we’ll clarify the differences between these two tools and how to apply them in a DevOps environment.
Terraform is an open-source declarative infrastructure-as-code tool that aims to provision and manage infrastructure across different environments. Unlike other IaC tools, Terraform is vendor-neutral. You can use it to manage infrastructure in any supported platform or tool, such as Microsoft Azure, Google Cloud, AWS, Linode, and Oracle Cloud.
First released in 2014 by HashiCorp as an open source tool, Terraform attracted almost 1,300 contributors within its first five years and has nearly 30,000 commits in its repository today. According to data gathered by StackShare, more than 1,600 companies report using Terraform in their tech stacks, including Uber, Slack, and Udemy, and the software’s popularity is widely credited to the fact that it excels at infrastructure management – including creating, updating, and deleting any infrastructure resources, from simple computational and database instances to entire Kubernetes clusters.

Ansible is an open-source configuration management tool targeted at provisioning and configuring applications. Now part of IBM/RedHat, the automation software was originally developed by Michael DeHaan to “provide a new way to think about managing systems and applications to better fit the digital world”. Ansible’s design goal was to provide an easy, quick solution for companies who employ full-time teams to spend hours or days managing cloud installations and configurations. The tool is agentless and connects to the desired environments using either PowerShell or ssh and carries out the necessary configuration changes. Ansible is more of a procedural tool with some declarative configurations.
As a configuration management tool, the functionality of Ansible gears more towards configuring existing infrastructure or platforms. It is the ideal tool if you have a fleet of servers and need to install and configure each server.
At a glance, both these tools seem to offer similar functionality. Both are infrastructure as code tools that provide you with the necessary toolset to provision, configure, and manage their infrastructure.
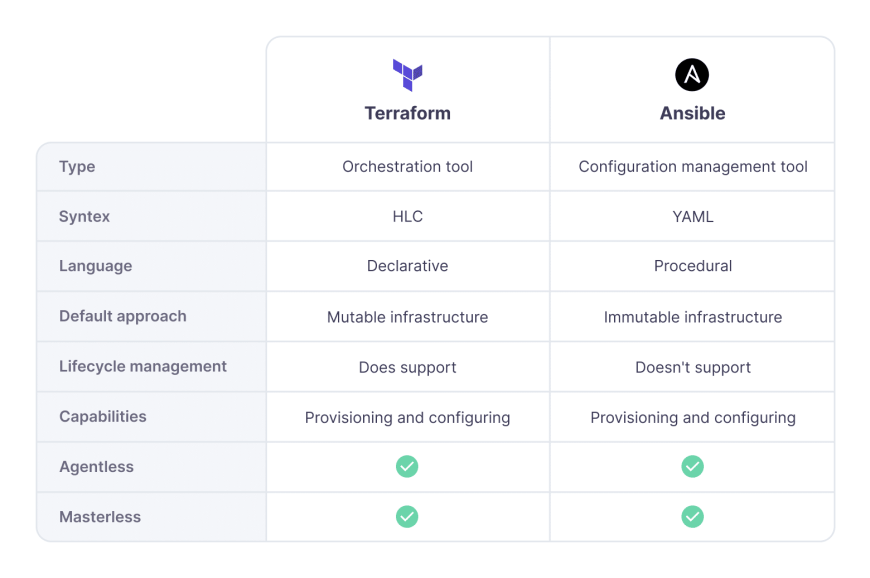
Both Terraform and Ansible are agentless and masterless tools, which means they don’t need dedicated agents to be installed and configured in the infrastructure they manage. They also don’t require dedicated hardware to run. These tools directly connect with the respective platform APIs to provision resources and use standardized methods such as SSH or scripts to carry out the necessary configurations.
Terraform can provision infrastructure as well as deploy applications in supported platforms. Ansible can also provision infrastructure, deploy applications and configure resources. The difference lies in the purpose of each tool.
Terraform is mainly an infrastructure provisioning tool meaning it excels at creating, modifying, and managing infrastructure resources. Ansible, on the other hand, is primarily a configuration management tool that excels at configuring provisioned infrastructure like installing/updating software, configuring runtime environments, changing configuration files, etc.
Terraform is the better tool for managing and provisioning infrastructure such as servers, networks, firewalls, storage buckets, and database instances. It is facilitated by the relatively user-friendly configurations of Terraform powered by either domain-specific Hashicorp Configuration Language (HCL) or Cloud Development Kit. They allow users to integrate Terraform with any supported common programming languages like Python, JavaScript, etc., and facilitate infrastructure creation.
On the flip side, Ansible will provide you with all the necessary capabilities to provision any type of infrastructure configuration, such as installing and updating software, setting up security configurations, and implementing policies. Ansible uses Playbooks which uses simple YAML syntax to facilitate infrastructure configurations.
Terraform is designed to be declarative at an architectural level. It greatly simplifies the codification experience as developers only need to specify the desired configuration and not all the steps required to achieve the desired configuration. On the backend, Terraform manages all that and creates the infrastructure according to the specified configuration.
Ansible is a hybrid of procedural and declarative, leaning more toward procedural. Thus developers need to specify the exact steps needed to achieve the required configuration for most Ansible configurations. While it would be a cumbersome task compared to Terraform, it provides users far more control when managing configurations. The infrastructure provisioning capabilities of Ansible can be considered the declarative part of it.
With a better understanding of Terraform and Ansible, let’s now see what exactly they’re used for.

Selecting the right tool comes down to your exact requirements. As mentioned previously, go with Terraform if you want a tool to provision and manage infrastructure. On the other hand, choose Ansible if you want a tool for configuration management. And remember: they are not mutually exclusive tools.
You are free to use both Terraform and Ansible in their environments as they excel at different tasks in the overall infrastructure management process. Using both allows you to combine their strengths and create the best possible automated infrastructure management experience. It all comes down to evaluating your exact needs and selecting the best tool with the features to cover them.
Terraform and Ansible are two leading IaC tools for managing infrastructure. While both are capable tools with some overlapping functionally, each offers specific functionality aimed at different use cases in the infrastructure management process. Terraform is better at infrastructure provisioning and management, while Ansible excels at configuration management.
Considering just how powerful both Terraform and Ansible are in managing infrastructure resources at a click, it’s no wonder hackers and malefactors are quick to exploit misconfigurations and exposed code secrets in configuration files and containers. To prevent a Terraform or Ansible misconfiguration from turning into a security breach, Spectral lets you incorporate security directly into your CI/CD pipeline, to empower developers to build and ship software without worry.

No single organization can master all trades, which is why their success hinges heavily on their vendors. And if vendors are crucial for your business operations,

Integration is an indispensable aspect of modern software development. As software applications become more complex and interconnected, every component must work seamlessly together like a game

Modern companies are rapidly adopting cloud applications and services due to scalability, cost savings, and faster time to market. DevOps teams and developers must deliver fast,