The Complete Guide to the Yelp API
Part of the Spectral API Security Series Yelp.com is one of the most influential crowdsourcing sites for businesses. The company is worth just over one billion
With over 200% YoY Growth and used by 100,000+ Organizations globally, Slack has become an indispensable internal communication tool for teams to coordinate their activities. But when it comes to exchanging information and external sources, certain risks are at play that requires more insight and attention.
Slack links to various vital systems within many organizations, making it an easy, central access point hackers can use to reach multiple systems. Slack needs to be managed with security to prevent one of your most valuable tools from becoming the source of a data breach and putting your organization’s sensitive data at risk. This requires auditing the tool to ensure it’s correctly configured and monitoring it throughout usage.
This article explores how to configure Slack and which configurations are best to maintain security and prevent breaches.

You can use Slack’s very own Audit Logs API to monitor what goes on in your enterprise grid. The Audit Logs API can monitor audit events to protect the system from unwanted access and ensure compliance with security and privacy regulations. Auditing also allows users to identify any suspicious activity originating from their organization, preventing insider attacks and internal data breaches.
The API allows users to automatically feed Slack access data into SIEM or similar auditing tools, allowing users to monitor for potential security issues or malicious access attempts proactively. Additionally, the tool enables users to write custom apps that offer insights into how your organization uses Slack. These methods give users a closer view of each user’s actions in the organization, but it’s important to note that the API doesn’t include message monitoring software.
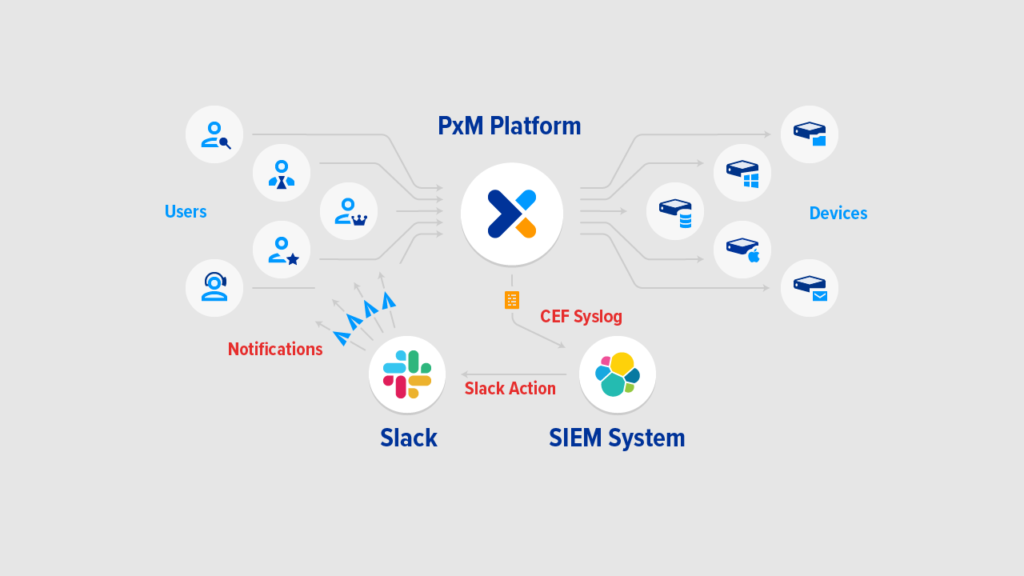
Slack’s Audit Logs API gives insights into events happening across the organization’s Slack environment. For this reason, it is read-only and doesn’t include any writing methods for Audit Log events. In addition, the API is limited in that it doesn’t perform any automated intrusion detection actions. Instead, it simply returns data that can be used to detect threats or intrusions, but it can’t automatically determine which activities are suspicious.
This API is an internal platform built by Slack to process Slack logs in real-time. It can identify statistically relevant characteristics and anomalies and delineate them in the admin audit logs. It supports a wide range of Slack audit events, and Slack is committed to developing the API and expanding its capabilities to support more audit events in the future.
Many configurations can enhance security and prevent Slack from becoming a source of unwanted data leaks. These include implementing security practices such as:
Two-factor authentication offers users an extra layer of security that requires members to enter a verification code in addition to their Slack password when signing in. This ensures that even if a malicious actor accesses a user’s password, access to Slack will only be granted if the person signing in can access their device to verify their identity.
Users can turn on app approvals to control which third-party apps are used in their organization’s Slack environment, and the data exchanged when these apps are installed. Slack’s default settings mean that every member of an organization’s Slack environment can install apps in their workspace. Workspace owners can choose to configure settings and restrict app installation permissions.
Configuring app restrictions can be done by going into app management settings on Slack and restricting which members can add apps and how members install and use these apps.
Slack is designed to foster transparency across your organization. This requires the sharing of sensitive and often classified information.
To prevent this information from reaching the wrong hands, users should strictly limit who has access to their workspace. Users can easily cull the amount of personnel with access to their workspace by following these guidelines:
Relying on policies alone is rarely enough when it comes to cyber security. Making employees part of your security protocol can help ensure your Slack workspace doesn’t become the source of devastating data breaches.

You can empower employees by incorporating Slack security training into your employee onboarding programs and running regular refresher courses for existing staff. Employees should also learn the fundamental security practices, like sharing information they wouldn’t share over email via Slack, and other potentially harmful behaviors, such as creating public links when sharing assets.
Training employees to recognize and monitor threats and making regular screening part of your regular security routine can help identify potential vulnerabilities early, preventing them from becoming full-blown data breaches.
Keeping up to date with community news and the latest developments in the Slack security research community will help you stay ahead of the curve and aware of the latest innovations in the security community.
Employing the services of external monitoring software or automated security scanning tools can help ensure that your Slack workspace remains secure.
Although your Slack workspace can be one of your most valuable tools, it can also be exploited as your organization’s greatest vulnerability. To prevent an asset from becoming a liability, it’s essential to implement best practices and configurations to keep your Slack workspace secure.
Unfortunately, despite their effectiveness, implementing the right configurations isn’t always enough. Even the smallest risk can have catastrophic effects and result in harmful data breaches. Luckily, you can still ensure your database remains secure with constant monitoring and vigilance.
Automated security tools like Spectral can add an essential layer of security without utilizing your limited resources, both human and otherwise. Spectral uses an AI scanning engine and hundreds of detectors to monitor your assets and infrastructure. The solution can identify the exposure of sensitive information such as API keys, credentials, and tokens and alert you to safety misconfigurations, allowing you to secure your Slack workspace before information leaks. To learn more, what better way than trying it out for free? Request a demo here.

Part of the Spectral API Security Series Yelp.com is one of the most influential crowdsourcing sites for businesses. The company is worth just over one billion

Part of the Spectral API Security Series Collaboration is key. Not only in software development. But when it comes to collaboration on Git repositories, the word

Part of the Spectral API Security Series The COVID-19 crisis brought many new buzzwords into our lives. One of the brand names that will forever be