Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Despite growing awareness and prioritization of cybersecurity, close to 22,000 vulnerabilities were published in 2021 alone. This concerning number proves that awareness and a willingness to invest in cybersecurity aren’t always enough to protect your organization’s network, and that network vulnerability is far from a problem of the past. To protect your networks, you need to continually monitor and assess their potential vulnerabilities to guarantee security. This starts with a vulnerability assessment.
Unlike penetration tests, which target specific vulnerabilities and can be performed manually, network vulnerability assessments are run by automated systems managed by either an in-house security team or a trusted MSSP (managed security services provider). They are used to identify and quantify the vulnerabilities in your network.
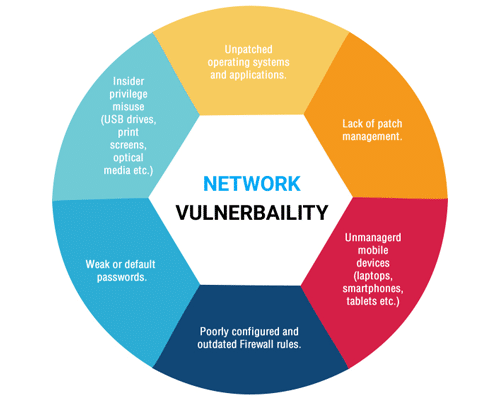
The process includes reviewing and analyzing your organization’s VPN (virtual private network) and its computing and communications devices and applications. This should result in a detailed report that goes through each vulnerability and shows your organization where in its network a security upgrade might be in order.
Unlike retroactive security measures, which seek to fix vulnerabilities after they’ve been exploited, this process gives organizations a proactive attitude against cybercriminals. It can prevent attacks before they have the opportunity to disrupt customer services, ensuring a seamless user experience.
The two main types of vulnerability assessments are:
Organizations should perform vulnerability assessments at least once a month as well as any time significant changes are made to the network, such as when changing access points or adding equipment to the network. This allows your security team to stay on top of system flaws and prevent them from becoming major issues. In addition, network assessments give your team a chance to gauge your system’s overall security accurately and provide them with the opportunity to understand the overall network environment and locate specific flaws.
Performing this process frequently ensures your team’s image of the network’s security remains up-to-date and that all flaws are nipped in the bud as soon as they appear before they have a chance to affect operations. In addition to heightened security and seamless service, network vulnerability standards ensure your organization complies with cybersecurity standards demanded by the regulatory boards of your industry, such as PCI DSS (Payment Card Industry Data Security Standard) or HIPAA (Health Insurance Portability and Accountability Act).

Now that we’ve analyzed the importance of performing regular network analyses, let’s look at the steps that ensure every analysis is thorough and productive:
Network vulnerability assessments begin with the complex process of identifying the potential risks and threats facing each of the organization’s assets. Your team can streamline this process by carefully structuring a list of those threats and ensuring that nothing slips through the cracks. Make sure none of the information you gather is wasted and that you don’t overlook any assets by creating one centralized document with all of the necessary information pertaining to threats and vulnerabilities.
Once your team has cataloged all this information on your organization’s assets, you can begin analyzing and assigning risks to assets. Risks are assigned to assets based on their potential impact and likelihood of the threat becoming a reality. When you have completed this process, your security team can prioritize assets that are most at risk or which would be most critically affected by having their vulnerabilities exploited.
Then it’s time to ensure your scanning methodology is thoroughly structured. This involves laying out a predetermined series of policies and procedures, delineating a straightforward course of action, and appointing an official owner responsible for what goes into each policy or procedure. Additionally, upper management will need to approve policies before their application.
Part of determining clear scanning policies includes clarifying the frequency of scanning. This is a significant step for adhering to many external compliance and security regulations. In addition to laying out the scanning frequency policy, you’ll need to document vulnerability scan configuration and functionality and the steps that your team must take once the scan is completed.
The most important information to document is the types of scans that the team will perform, how to implement the scans, the software solutions used, which vulnerabilities should be prioritized, and the actions taken after the scan is completed.
Configuring scans can be as simple as defining the objectives of the scan and identifying the type of system you want to scan. You can breakdown the process of configuring a network vulnerability scan into four simple steps:
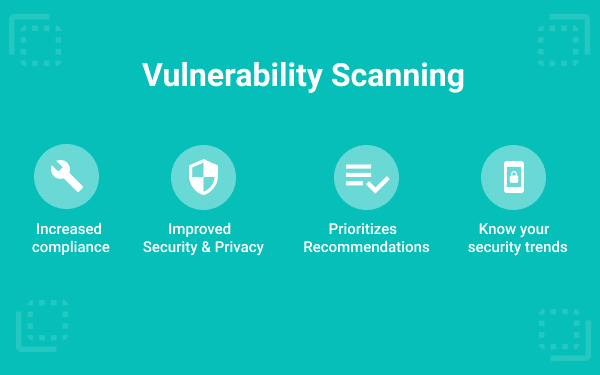
Once you have identified the type of scan you want to conduct and set its configurations, you can save the configured settings for future use to save time when running the scan whenever needed. Keep in mind that scans can range from minutes to hours, depending on the target size and thoroughness of the scan.
Vulnerability scans can be divided into three phases:
During the scanning phase, the software you use will fingerprint the targets specified and gather preliminary information on them. The software will then use this information to enumerate the targets and gain more detailed information, such as which ports and services are in use and running. After determining these specifications, the software will search and identify any existing vulnerabilities in the target IP.
At this point, your team will need to perform most of the analysis process manually. Prior knowledge of the scanned system is especially beneficial as your team will know which vulnerabilities will have the most critical impact and are a high priority. Although scanning tools will often prioritize vulnerabilities automatically, inside knowledge may mean that your security team will perform this task more effectively.
This stage also involves manual analysis of the automated system’s results, including filtering out false positives and ensuring that the identified vulnerabilities are valid. Once your team has validated the vulnerabilities, they can start investigating the potential root causes and future impact of each vulnerability to repair existing ones and prevent similar vulnerabilities from appearing in future scans.
After you have interpreted and validated the results, your team can work on mitigating each vulnerability. This requires that the security team work with IT staff to ensure all mitigation procedures are carried out. Clear communication and cooperation will streamline and simplify the process while ensuring that successful mitigation procedures are carried out.
At this point, both teams will likely conduct numerous follow-up scans to ensure that they have neutralized the previously discovered vulnerabilities. These scans will continue until the discovered vulnerabilities no longer appear in reports.
Assessing your network for vulnerabilities prevents cyberattacks from occurring and disrupting your productivity. Unfortunately, while network vulnerability analysis is a critical aspect of cybersecurity, it only makes up a fraction of a robust cybersecurity strategy. Maintaining a high standard of security that complies with regulatory requirements and covers your organization’s entire attack surface is far from simple, but by performing routine assessments you will be well on your way towards ensuring that your network is protected, and that no significant vulnerabilities slip into your blindspot.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions