5 Bad Coding Habits That Leave Your Source Code Exposed
In 2020 the average cost of a data breach was $3.86 Million. There are many ways that you can be proactive about your security to prevent
Containers have quietly become indispensable in the modern application deployment stack, revolutionizing how we build, ship, and run applications. However, with their widespread adoption comes a pressing concern.
According to the 2024 State of Kubernetes Security Report, 45% of respondents experienced a runtime security incident in the last 12 months. This raises a few questions: What exactly is container runtime security? And how can you protect your workloads while they are running and not after the fact?
We’ll take a practical approach to understanding container runtime security and provide actionable steps to implement it in your containerized environment.
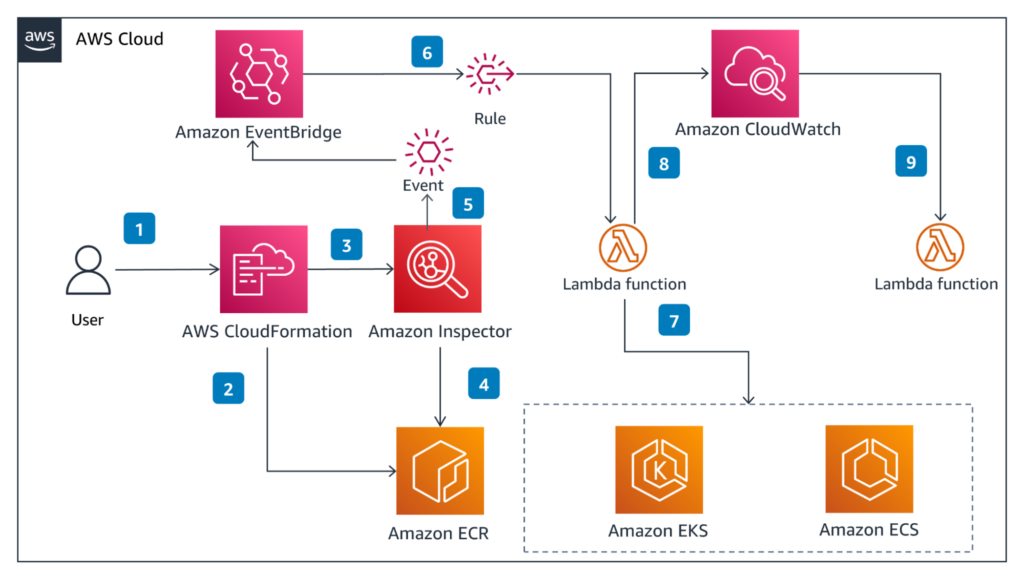
Source: AWS Guidance for Container Runtime Security with Amazon Inspector
Before diving into runtime security, let’s refresh our understanding of container runtimes. A container runtime is the software responsible for running containers. Popular examples include runc (the industry-standard low-level runtime) and containerd (a higher-level runtime used by many container platforms).
Container runtime security focuses on protecting your applications while they are actively running. Unlike other security measures that work before or after deployment, runtime security operates in real-time, continuously monitoring and defending your containers against threats as they execute.
Containers, by design, share the host system’s kernel and resources. This shared environment creates unique security challenges, such as container escapes—where a compromised container might try to access the host system—and vulnerabilities within the application runtime that could be exploited.
Whether you’re running containerized applications as a small startup or a large enterprise, DevOps teams, security professionals, and developers all play a role in ensuring runtime security. Runtime security solutions use various techniques to detect and prevent threats, such as:
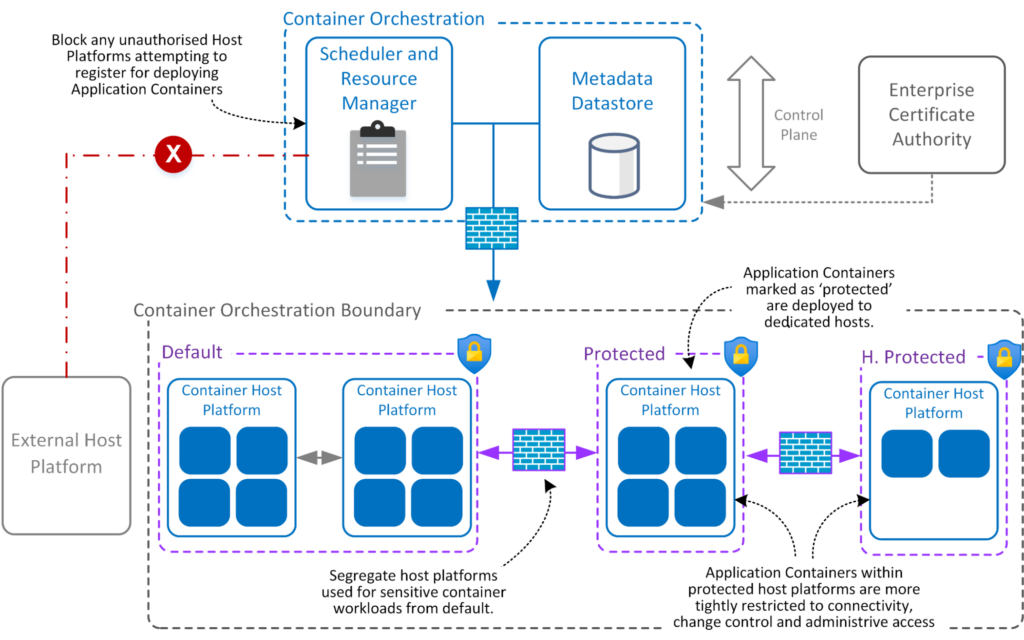
Source: Security Pattern – Container Orchestration
Runtime security is a multi-faceted approach that combines several efforts to protect your workloads during execution. When securing your container runtime environment, consider the following essential components.
The first step in securing your container runtime environment is to ensure the integrity of your container images. Begin by consistently using trusted repositories when pulling images. This practice minimizes the risk of introducing malicious or vulnerable content into your environment. Strategies like IT process automation can support maintaining security and efficiency across your IT environment.
Next, ensure continuous scanning of your images, even after deployment. This proactive approach helps you identify and address newly discovered vulnerabilities quickly. Verifying images with Software Bills of Materials (SBOMs) is also essential. SBOMs give you a detailed inventory of all components within your software, aiding in vulnerability management. Tools that assist with scanning vulnerabilities in your dependencies, like npm audit for dependency scanning, are particularly effective in preventing weak links from making it into your runtime environment.
For an extra layer of security, consider using distroless or scratch images. These minimal images contain only what’s necessary to run your application, significantly reducing the attack surface.
Effective runtime protection begins with identifying your application’s most vulnerable aspects. Understanding these vulnerabilities allows you to focus your security efforts where they are most needed. For example, you might identify scenarios where unauthorized processes could access sensitive files or certain behaviors deviate from the norm.
After identifying these vulnerabilities, set up targeted monitoring tools to watch for these specific behaviors. Tools like Falco and Tetragon are particularly useful, as they allow real-time enforcement of security policies tailored to your application’s unique threats. This targeted approach ensures that the most critical aspects of your application are continuously monitored and protected. This is just as crucial during runtime as it is during the development phase, as highlighted in practices like Angular security measures.
Access controls are fundamental to securing your container environment. In Kubernetes environments, Role-Based Access Control (RBAC) maintains security by assigning appropriate permissions to users and processes. RBAC allows you to define fine-grained permissions, ensuring that each role within your system has only the necessary access rights.
To maintain a secure environment, it’s essential to regularly review and update these permissions, adhering to the principle of least privilege. Implementing stringent access control methods, such as Mandatory Access Control (MAC), can further enhance your security posture by providing tighter control over who and what can access your containerized workloads.
Network security is a crucial aspect of protecting your container runtime environment. Start by implementing network policies that control traffic flow between containers and external sources. These policies ensure that only authorized communication occurs, thus reducing the risk of unauthorized access.
Consider using network segmentation to isolate containers from each other and external networks. This isolation helps contain potential security breaches, limiting the attacker’s ability to move laterally within the network. For those seeking more advanced network security, deploying a service mesh can provide features like mutual TLS encryption and fine-grained access controls at the network level, further enhancing your security posture.
Maintaining compliance and enforcing security policies is essential. Define clear security policies aligning with regulatory requirements and your organization’s internal standards.
Use tools that enable real-time monitoring and enforcement of these policies. Regularly review and adjust your policies to ensure they remain effective in an evolving security landscape. Tailoring your policies to specific compliance needs, such as HIPAA or PCI-DSS, helps ensure your security posture is compliant and robust.
Continuous monitoring and regular auditing are crucial to sustaining adequate runtime security. Set up real-time monitoring tools that catch issues, allowing you to address potential threats immediately. Having a well-prepared incident response plan supported by the right tools, such as those found in top incident response tools, is critical when incidents arise.
Advanced code scanning tools, like Spectral, can identify security issues before they impact your runtime environment. Regular audits complement this by assessing the effectiveness of your security measures and identifying areas for improvement. Streamlining this process with no-code security automation can help you avoid potential threats.
You can refine your security policies and practices based on audit findings, ensuring ongoing protection against emerging threats.
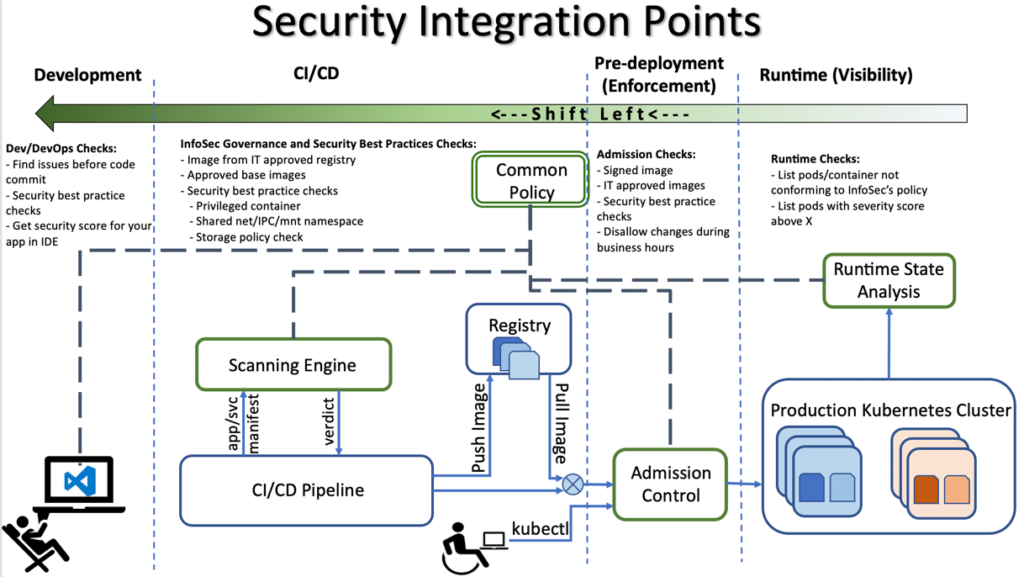
Source: Enhancing Container Security: A Deep Dive into the GitHub Repository I recently published
As container security evolves, new tools are emerging to address runtime security challenges. One powerful tool to consider is Tetragon from Cilium. Tetragon leverages eBPF(extended Berkeley Packet Filter) technology to provide deep visibility into container behavior at the kernel level.
Another notable tool is Falco, which Sysdig developed. Falco offers real-time threat detection for containers and Kubernetes, using a rules engine to identify suspicious activity. For those interested in diving deeper into runtime security mechanisms, Tracee from Aqua Security is worth exploring. This open-source runtime security tool also utilizes eBPF to trace system calls and provide detailed security events.
The future of runtime security is closely tied to eBPF technology. eBPF (extended Berkeley Packet Filter) is uniquely suited for container runtime security due to its kernel-level operation and programmability. It allows for:
Container security is much like a sprint—threats continuously adapt, and so should your defense mechanisms. While we cannot boil the ocean, we can secure our environments in short sprints. Runtime security is an excellent way to detect and remediate threats during execution rather than after the fact, potentially saving hours of recovery time and mitigating reputational damage.What’s even better than runtime security is preventing vulnerabilities from making it into production in the first place. Let Spectral help you today by automating your run time security and helping you hunt down vulnerabilities faster than you can say, “I found a container runtime vulnerability.”

In 2020 the average cost of a data breach was $3.86 Million. There are many ways that you can be proactive about your security to prevent

For a long time, the best approach to network and data security was network segregation. If you protect your intranet from the Internet, there are significantly

Did you know that Kubernetes is one of the leading open-source projects globally, boasting contributors from Google, Microsoft, and many other tech giants? Kubernetes enjoys the