Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
AWS (Amazon Web Services) allows businesses to quickly and securely build and scale applications. Hence, there is exponential growth in AWS usage among businesses and organizations. For example, As of 2020, AWS held 76% of enterprise cloud usage, reflecting the power and importance AWS holds.
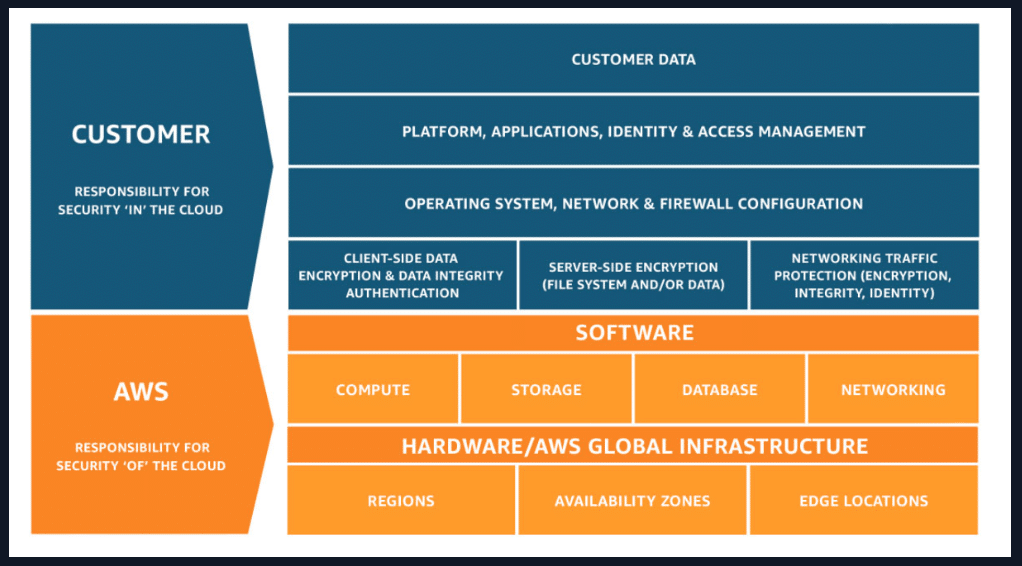
This increased use of AWS tools and services opens new doors for cyber attackers. However, AWS is a very reliable cloud service provider that works hard to ensure protection over its infrastructure. Still, it is important to note that when you use an AWS service, you and AWS share the security responsibility since AWS follows a Shared Responsibility Model.
It is important to ensure that you have secured your AWS Services from your end of the Shared Responsibility Model. To do so, AWS offers various services to ensure your applications are compliant. This blog focuses on 7 AWS security tools and services every AWS user should know to ensure the high security of their applications.
Before discussing the AWS security tools, it is essential to understand how security, identity, and compliance on AWS works.
Following a shared responsibility model means AWS is responsible for securing the infrastructure that services run on, while the customer is responsible for configuring the security of the services they choose. For example, suppose you select DynamoDB as the service. AWS will take care and secure the hardware, network, and storage that the DynamoDB service runs. However, you have to take care of the security of your DynamoDB tables (data) using the security tools provided by AWS.
Furthermore, AWS security tools help you comply with government regulations like GDRP and PCI easily. Complying with these regulations will increase your company’s reputation and attract more customers since you ensure protection for their data.
AWS provides a wide range of security tools and services to help you ensure high security for your applications. These services comprise six main categories:
You can select a tool from these six categories based on your requirement. You can find a detailed list of tools in each category here.
Most AWS services are accessible through public APIs. Hence, it is important to follow necessary security measurements at the required levels to prevent any data leaks.

For example, suppose you are uploading images to an S3 bucket through your application. Enabling public access to the bucket will allow anyone with a link to access the images and create a possible security breach. So, you should take proper security measures like AWS policies, IAM access, and pre-signed URLs to increase the security of the images.
Cross-site scripting (XSS), SQL injection, brute-force attacks, and distributed denial-of-service (DDoS) are some common attacks performed on AWS-hosted applications and services. AWS security tools in detection, network protection, and data protection are great solutions to increase application and service security.
On the other hand, your AWS account itself can be under attack. In such cases, you have to use identity and access management tools like AWS IAM to increase the security of your AWS account.
AWS Artifact is an on-demand service that allows you to access and download security/ compliance-related information and digital agreements from AWS and ISVs.
For example, you can download Service Organization Control (SOC) reports, Payment Card Industry (PCI) reports, and ISO certifications with AWS Artifact. These documents can be used as proof for auditors or regulators in showing how secure and legally compliant your AWS infrastructure and services are.

You can access the AWS Artifact portal directly from the AWS management console, and AWS will not charge you for using AWS Artifact.
There are many options for protecting sensitive data on the AWS platform. But, still, some applications may require legal or contractual requirements for handling cryptographic keys.
AWS CloudHSM (Hardware Security Module) is a cryptographic service specialized for such situations. It allows you to create dedicated HSM instances based on government standards within the AWS cloud and protect encryption keys using them.
Overall, AWS CloudHSM is useful for cryptographic tasks like:
AWS organizes HSMs as clusters, and you can add more clusters and distribute them across multiple AZs to ensure high availability. Regarding pricing, AWS CloudHSM does not have any upfront costs. However, it will charge an hourly rate of 1.45 USD until you terminate the instance.
AWS Secrets Manager allows you to easily manage, rotate, and retrieve secrets through their life cycle. It is widely used to manage database credentials and API keys.
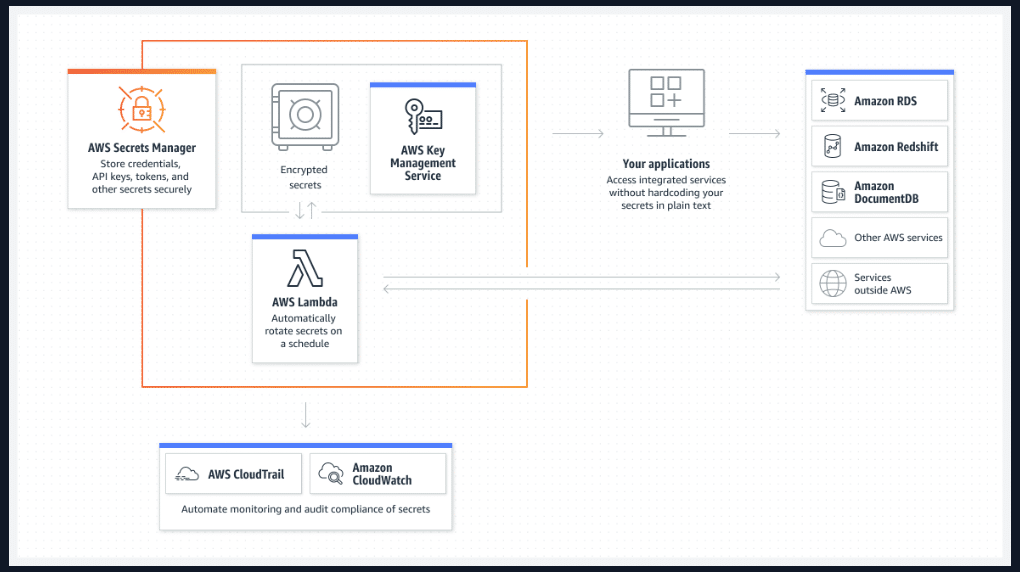
In addition, AWS Secrets Manager can be used in many other situations:
AWS Secrets Manager provides a free trial of 30 days. After that, it will cost 0.40 USD per secret/month, including all the replicas. In addition, you will be charged 0.05 USD per 10,000 API calls.
AWS GuardDuty is an intelligent threat detection service capable of continuously monitoring and identifying security threats in your AWS accounts and workloads. This service is really useful in performing continuous security checks on critical AWS Services such as EC2 instances, EKS clusters, and S3 buckets.
In addition, GuardDuty provides detailed security findings that can be used for security visibility and to help with remediation if there is any potential malicious activity, such as anomalous behavior, credential exfiltration, or communication between command and control infrastructure (C2) components. Additionally, detecting harmful files on Amazon EBS volumes attached to the EC2 instance and container workloads is made easier with the help of Amazon GuardDuty.
AWS GuardDuty charges are based on the analysis type you perform. You can find a details description of different pricing options here.
AWS Inspector works pretty similarly to AWS GuardDuty. It continuously scans your AWS resources and identifies the vulnerabilities in them.
When Amazon Inspector finds a software vulnerability or a network configuration problem, it creates a finding. A finding explains the vulnerability, specifies the resource it affects, grades its severity, and offers remediation guidance. With these results, you can prioritize the vulnerabilities and fix them based on their severity.
Furthermore, Amazon Inspector is useful in meeting compliance requirements for NIST CSF and PCI DSS regulations and identifying zero-day vulnerabilities.
The pricing model for Amazon Inspector is a bit complex compared to other services. You can find a details pricing plan here.
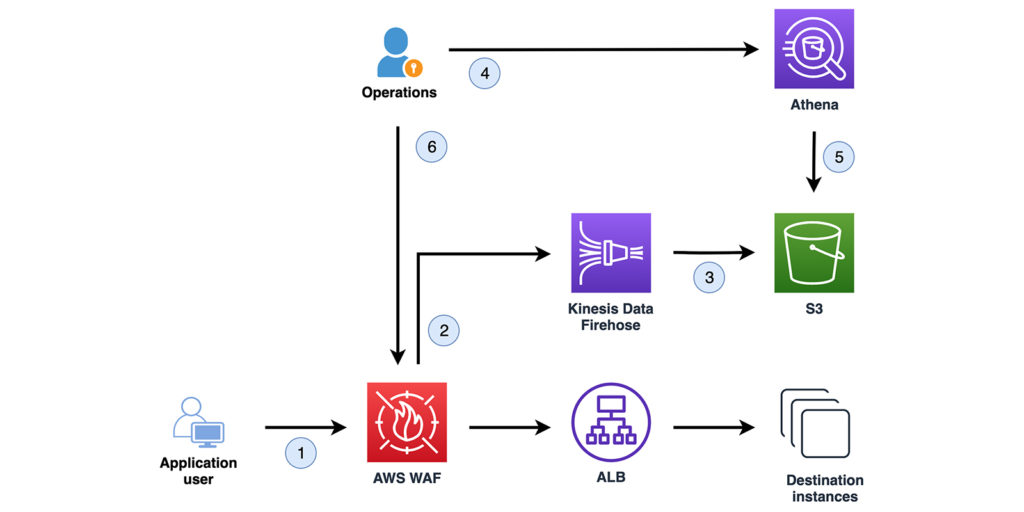
AWS Web Application Firewall (WAF) is a cloud firewall that monitors incoming HTTP and HTTPS requests to your protected AWS services. AWS WAF allows you to define a set of conditions like origin IP addresses and query strings. When your protected resource receives an HTTP/HTTPS request, AWS WAF will check the conditions and respond accordingly. If the conditions match, it will send the requested content. If not, it will respond with an HTTP 403 status code. In a nutshell, it helps protect an application from layer 7 attacks in the OSI Model.
AWS WAF can be used to protect the following resource types:
Using AWS WAF is pretty easy because it is a fully-managed service that takes care of all your responsibilities. You don’t need to install software or worry about updating the firewall. Furthermore, you can use AWS WAF to prevent brute-force HTTP flood attacks.
AWS WAF charges based on the resource type. You can find more details on AWS WAF pricing plans here.
AWS Shield is a fully managed Distributed Denial of Service (DDoS) defense tool. It is a great service at your disposal since DDoS attacks are among the most common types of attacks.
There are two tiers in AWS Shield:
All incoming traffic is analyzed by AWS Shield, which also mitigates attacks when malicious activity is found. The sole drawback of the service is that even though you are protected, you cannot view an attack history and do not receive any alerts or reports outlining the attack.
You can find more details on AWS Shield pricing plans here.
This article discussed 7 AWS security tools that every AWS user should use in 2023. In addition to these tools, AWS provides many others, as well as services, that can help increase the security of your cloud applications and data.
Although these tools provide a significant level of security, they have some gaps that don’t meet the most pressing security concerns today. For example, native AWS security tools do not provide protection measurements related to CI/CD pipelines.
In such situations, you have to go with third-party security solutions like Spectral for CodeBuild Security to increase the security of your delivery process. Spectral for CodeBuild Security allows you to enforce policies and detect security issues in your CI/CD pipelines in real time.
It takes only 3 minutes to integrate Spectral for CodeBuild Security with your existing AWS CI/CD pipelines. By using a combination of these AWS Security Tools along with Spectral for CodeBuild Security, you can detect and mitigate security threats early on in the development workflow to ensure that your application is ready to scale and remain protected from attacks that may arise in 2023.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Part of the Spectral API Security Series Yelp.com is one of the most influential crowdsourcing sites for businesses. The company is worth just over one billion