Circle.ci vs Jenkins: Battle of the CI/CDs
Continuous integration and delivery are necessary in any production level software development process. CI/CD are more than just buzzwords. Rather, it is a fully-fledged methodology of
In 2022, the adoption of infrastructure as code (IaC) soared, with IaC domain specific languages like HCL, Shell and GoLang gaining popularity and momentum across the open source tools ecosystem. In fact, the rise of Policy as Code is the result of a new paradigm blurring the lines between IT, legal and R&D departments – everything as code.
But what do developers have to do with compliance and infrastructure provisioning? What does PaC entail, and what types of PaC are there? Where does a developer start their policy coding journey, and what tools and skills will they need to bring along? Let’s explore the answers in this blog.
Policies are rules, guardrails, and instructions that define and enforce particular user and application behaviors. Policies in software development can be applied in various areas, including:
When you think about it, policies are everywhere. An organization, its software development lifecycle, and the product have multiple policies that must be maintained and enforced without impacting operations.
Traditionally, policy management entails defining policies in natural (human) language or other non-machine-readable formats (such as spreadsheets, documents, or verbal instructions). These policies are typically enforced manually by personnel responsible for monitoring and enforcing compliance with said policies.
While this approach may work for things like corporate dress codes, it becomes much more challenging to manage when it comes to more risky and costly compliance regulation violations, such as access to critical systems and sensitive data.
Unlike manual policy management, PaC configures policies in machine-readable code, such as YAML, JSON, vendor-specific DSL, or Python, and enforces them through automated tools and processes.
This approach enables policies to be defined and enforced more consistently and efficiently while reducing the risk of human error and improving the auditability of policy enforcement.
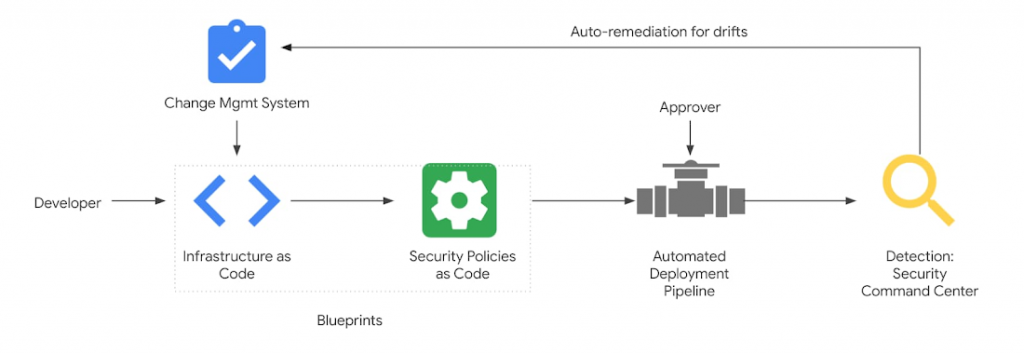
Compared to traditional policy enforcement, PaC offers several benefits, including:
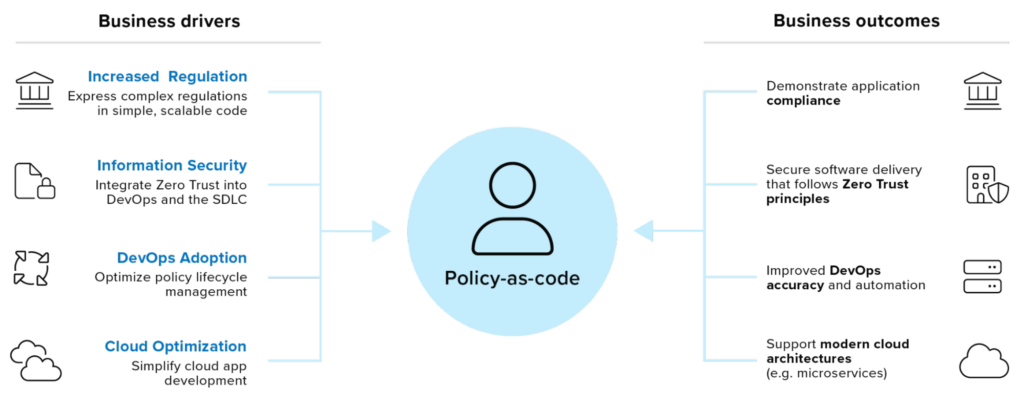
You may be thinking: okay, this is all nice, but shouldn’t this be left for IT, infosec, and compliance teams to handle? Isn’t PaC just additional work for developers? The good news is that PaC can significantly contribute to developers’ productivity.
Here are just a few examples of policies developers can employ in their work:
Ultimately, codified policies in your SDLC aim to enable developers to write higher-quality code more efficiently and confidently while improving the system’s security, maintainability, and compliance. All by doing what developers do best: code.
We can divide the types of policies you can apply as code into static and dynamic categories.
Static policies as code are defined and enforced at the time of deployment. Once the policy code is deployed, it usually remains unchanged until the next deployment cycle. Static policies are usually defined in configuration files or scripts and enforced by IaC tools.
Dynamic policies as code are policies you can update and enforce dynamically during runtime. Dynamic policies are often defined in code within the application or service and can be updated through APIs. Dynamic policies can be more flexible and responsive than static policies, allowing organizations to adapt to changing requirements and threats.

Start by identifying the policies you want to enforce before you define them in a machine-readable format. At this point, it’s worth sharing the responsibility of setting and enforcing policies between teams in your organization. Unless you’re part of a small startup, there’s no reason for a developer to be charged with creating and enforcing policies for things like network security.
Based on the policies you want to enforce, you’ll need to choose how you define them. For example, policies that interact with your development environment might be defined in your SCM. Policies in your pipeline may be implemented with whatever tool you use for CI/CD. Data protection should be configured to your Cloud, and so on.
Various tools on the market could help you set up and enforce PaC. Common ones to consider include:
When selecting a PaC tool, it’s important to consider factors like ease of use, compatibility with your existing stack, support for the policies and compliance frameworks relevant to you and your organization, and the level of automation and integration you require.
Once you have defined your policies and selected a tool, you must integrate PaC into your development process. This could involve configuring your CI/CD pipeline to validate policies at build time, integrating policy checks into your testing process, or using PaC tools to monitor and enforce policies at run-time in production.
PaC is an iterative process, and you should continuously monitor and update your policies to adapt to changing requirements (such as regulations) and threats.
PaC can help you work more efficiently and confidently while improving the security, compliance, and reliability of the code base, the environment it’s built on, and the applications built with it. By incorporating PaC into your daily work, you can help ensure that your code is of the highest quality and meets the needs of the organization and its end users.
With Spectral, developers can define and enforce regulations and best practices (including GDPR, PCI, and others) throughout the SDLC. Spectral enables developers to integrate their own playbooks, build their own detectors, and implement mitigation policies to automate code scanning, including codified policy.
Schedule a demo to learn more about how Spectral can streamline your code security policy implementation and enforcement.

Continuous integration and delivery are necessary in any production level software development process. CI/CD are more than just buzzwords. Rather, it is a fully-fledged methodology of

Jenkins is the most used open-source CI/CD solution out there. Being a FOSS project usually means that there’s an ever-growing number of extensions and capabilities for
Code fast and break things may be a healthy approach when you’re rushing to present investors with a POC. However, when it comes to developing real-world