Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
It can feel like so many stars must align to effectively implement and measure security metrics. For example, you need to understand how to adapt frameworks to your company’s specific situation in an industry that’s not too open about its metric strategies. Then, despite talent shortages, you need enough team members with authority and drive to ensure your company prioritizes security, despite the common desire to move forward as fast as possible. Of course, you also need the right tools to gain visibility into what’s going on, so you can measure and tweak your metrics as you go.
But it’s all worth the effort. 89% of businesses in 2023 said they suffered at least one negative impact in the past year due to a lack of cybersecurity and business alignment. In this blog, we will review why security metrics are important for protecting your business against cyberattacks, and the top seven metrics you should start with.
Security metrics are objectives you can measure. They can be demonstrated by uptime, performance, SLAs, detection rate, change failure rate, etc. They help gather data on different cybersecurity management aspects and identify improvement areas. Metrics are usually decided based on business goals. For example, if you aim to reduce the number of successful cyber attacks, you can measure the percentage of prevented attacks.
Here are the essential reasons to measure security metrics.

Here are some considerations we recommend you consider when deciding what to measure.
Every company has different needs. It’s important not to measure for the sake of measuring – choose metrics that actually matter to your business. To give you a few examples…
Therefore, choose your cybersecurity goals first. Then, break them down into different aspects and areas you could measure before deciding on exact metrics.
It’s helpful to break down your metrics into smaller chunks. The idea is to give your team quick wins and motivate them to stay on track, achieving ambitious and higher goals in time. After all, a recent report in Fortune magazine found a link between goal unattainability and increased anxiety.
The best metrics get measured on a schedule to reach certain improvements by the next deadline. In this instance, deadlines also need to be attainable and gradually scaled up as your tech gets smarter and your team gains skills and practice. Stay accountable with scheduled reports and reviews. Let everyone know the schedule and what needs to be achieved by then, so they can break it down into actionable steps.
Let’s review some security metrics you need to know, why they matter, and how you can measure them.
User access controls help you verify that only authenticated, necessary identities gain access to your company’s resources.
Why it’s critical: 82% of companies provide third-party vendors highly privileged role without good reason. In fact, in 2022, misconfigured access created a small security gap that exposed 1.5 million files of sensitive data to the public. When these privileges go unused and unsupervised, it’s easy for hackers to break in undetected. User access controls keep unwanted, and often dangerous, identities from gaining access to sensitive parts of the organization. If you employ the highly recommended zero trust or least privilege frameworks, you ensure every team member and machine has exactly the access they need to perform well – but nothing more.
How engineers can measure it: Start by tracking how many privileges you provide and the percentage of logins you see. If you discover a high percentage of access, yet a small percentage of usage, it’s time to revoke unused access. You can also measure types of most used access – say, which roles use their access to a certain resource more – to better understand what’s really required.

This metric is about how long your tech and/or team takes to detect threats.
Why it’s critical: The longer a threat is in your system, the higher the chance of an escalated problem. For example, a hacker might go further into your system, reaching more sensitive data.
How engineers can measure it: Track how long it took to discover a threat from the moment the incident began. Maybe one time it took 15 minutes, another time 75 minutes and another day, 125 minutes. Then, combine all these times (15 + 75 + 120 = 210) and divide them by the number of incidents (3) to discover your mean time to detect (MTTD). In this case, your MTTD is 70 minutes. You won’t need to do this manually if you have relevant tools. In any case, your goal here is to show how you reduce this security metric over time.
How many new vulnerabilities do you discover in your organization? These could include unpatched software, vulnerable code dependencies, infrastructure misconfigurations, and weak authorization credentials.
Why it’s critical: Vulnerabilities are access points for hackers to get into your network. You need to discover them to ensure they can’t be exploited.
How engineers can measure it:Measure the number of new vulnerabilities you discover and how that number changes over time. If the number rises, it’s time to investigate why. On the other hand, if you suddenly see a major drop, pay attention too. It’s important to analyze whether your detection software no longer works for you, or whether it’s happy news, such as your team is improving at reducing vulnerabilities.

Once you’ve detected a threat, MTTR lets you know how quickly you resolve it and regain safe and complete system functionality.
Why it’s critical: Like MTTD, the faster you resolve an issue, the less severe (and expensive) it becomes.
How engineers can measure it: Similarly to MTTD, you can measure how long it takes to resolve incidents from the moment they started, then divide it by the number of incidents to discover your MTTR. About all else, you can aim to continuously reduce this number.
Part of cybersecurity’s is ensuring businesses comply with regulations and laws involving, among others, data privacy and integrity.
Why it’s critical: Failing to comply might lead to significant financial fines or certifications getting revoked. This could negatively impact clients’ and prospects’ ability to trust your company. After all, failure to comply could indicate your organization is vulnerable, and the data that’s been entrusted to you isn’t safe.
How engineers can measure it: Break down what it takes to comply with your next audit, and create security metrics to check in internal audits beforehand. Conduct internal audits regularly and score them. Finally, you can aim to improve your score each time.
Cybersecurity management costs will increase by almost 70% by 2028. It takes many resources – human resources, hardware, software and… yeah, the cost of getting attacked.
Why it’s critical: Reducing costs of incident management, as well as improving resource usage by combining efficient technology and employee training, can make a direct impact on the company’s bottom line and its ability to succeed. When you do that, it’s easier to prove to management why you need additional resources.
How engineers can measure it: You can start by calculating the costs you save by managing incidents well. Include what it would cost to lose work time or company assets or the regulatory fines the organization would have paid. Similarly, if you’re incorporating a new software, track how many hours it saved your team and how they used these hours to further protect the company.
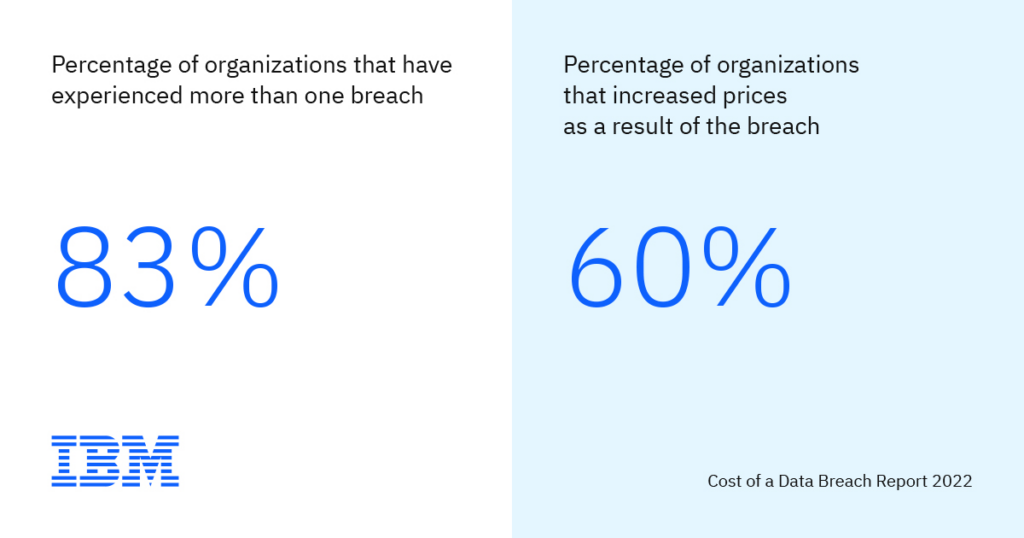
Check how your cybersecurity management compares to others in your industry.
Why it’s critical: If you’re doing significantly better on the cybersecurity front, it could be a market advantage, especially if you work in or serve highly regulated industries. Knowing your company is ‘behind’ on some metrics enables you to take action and close the gap before your company experiences business consequences.
How engineers can measure it: You can use cybersecurity management software products that allow anonymous metric comparison or invite your peers to an anonymous survey.
68% of companies are shifting towards […] making developers share responsibility for a secure software development lifecycle. Understanding and measuring key security metrics is critical, but you don’t have to do it all manually. Spectral’s scanning engine, for example, automates the secret protection process to secure API keys, tokens, credentials, and more. With Spectral, you can proactively assess the security posture of your applications and infrastructure. It allows you to prioritize security efforts, detect and respond to incidents efficiently, maintain compliance, and mitigate potential vulnerabilities.
Launch your free code scan today.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Part of the Spectral API Security Series Yelp.com is one of the most influential crowdsourcing sites for businesses. The company is worth just over one billion