Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
If you are a developer in the current cybersecurity climate, you already know your application’s security is paramount. But have you considered the risks associated with your vendors?
With over 50% of new applications developed in the coming years being Cloud-Native, vendor-related cyber security risks are a growing concern.
Cloud-native organizations must consider all vendors during risk assessment. Today, you rely on countless vendors, some of whom are unknown to IT. Every vendor increases your attack surface, whether misconfigured infrastructure, unsanitized APIs, or poor authentication hygiene. To push back the tide, you must prepare to scrutinize every vendor and take steps to safeguard your cloud applications.
Vendor risk is relevant to any organization, but Cloud-Native environments are particularly prone to exposure due to extensive reliance on vendors. Everything from the cloud computing infrastructure to your email accounts is potentially vulnerable. When developing cloud-native applications, developers must balance the risks of cloud development against the benefits, which are, of course, substantial.
Cloud-native development allows you to remain agile, but the cost is loss of direct control over the platforms and infrastructure that would otherwise be on-premise. However, this lack of direct control is part of the benefit, as IaaS and PaaS providers take care of substantial IT overhead.
The last thing to consider is the increased attack surface with every additional connected vendor. Privileged escalation through exposed APIs, compromised container images, or leaked passwords stored on git repositories can cost millions of dollars in damage and reputation. But fear not; vendor risk is manageable with the proper preparation.

APIs are the lifeblood of cloud-native systems, serving as the conduits through which data flows. Every API is a potential attack vector, and securing them through just-in-time self-service access is crucial to prevent public blindspots. According to OWASP’s top API security risks, the main culprit of API vulnerabilities is the improper handling of authorization and authentication. Further, APIs expose functionality that can be expensive to run, exposing you to denial-of-service attacks.
Rate limiting and proper disposal of authentication and authorization objects are crucial to maintaining healthy APIs. Third-party APIs should be configured correctly to prevent attacks and maintain security.
Most cloud services have extremely permissive default permissions, which makes sense from an onboarding perspective. When setting up a cloud service, you won’t bother changing permissions and authentication, especially when using a new service. The problems surface when you never properly fix those settings to secure the service.
The shared responsibility model, a key aspect of IIoT security essentials, means that the vendor is responsible for securing the cloud, but you are responsible for security in the cloud. Remember that it is your responsibility to configure cloud services with secure principles in mind.
Containers offer unparalleled flexibility and efficiency but harbor hidden vulnerabilities within their images. Using pre-built container images without proper validation is akin to playing Russian roulette with your system’s security. Manually checking each image for vulnerabilities is time-consuming and ineffective.
Use container scanning tools to test images and Infrastructure as Code (IaC) to replicate secure settings, aligning with the essentials of a cyber threat intelligence framework and addressing security misconfigurations that can lead to data breaches.
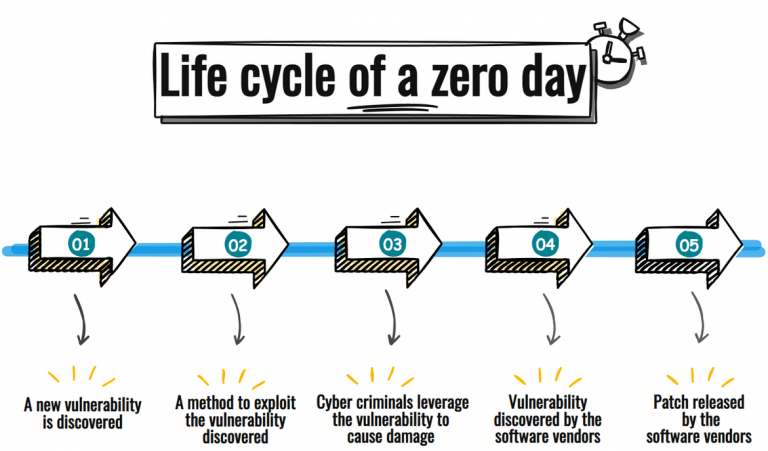
Zero-day exploits, vulnerabilities unknown to the software vendor, pose a significant threat as they can be weaponized before patches are available. It leaves organizations exposed, regardless of the vendor’s size or reputation. While you may have limited control over fixing the exploit directly, proactive measures can mitigate the impact. Implementing continuous monitoring of vendor security advisories, subscribing to relevant threat intelligence feeds, and utilizing intrusion detection systems (IDS) and intrusion prevention systems (IPS) can provide early warnings of potential zero-day attacks.
Additionally, data security posture management (DSPM) solutions can help identify and prioritize vulnerabilities in your environment, enabling swift patching or rollbacks of affected vendor software to minimize the attack surface.
GDPR, CCPA, and many industry-specific regulations cast a long shadow over cloud-native development, demanding meticulous attention to compliance. To achieve compliance, every one of your vendors must be compliant. You can trust industry giants to comply with most regulations, but smaller vendors must be scrutinized.
The ever-changing nature of compliance means you must periodically monitor vendors. If a vendor is non-compliant, you may need to switch service providers, which brings us the risk of vendor lock-in.
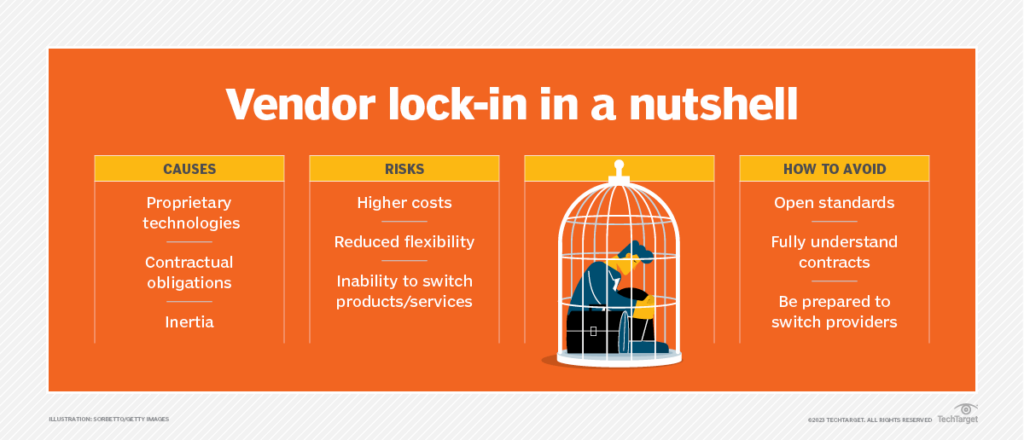
Single-vendor cloud development is dead. Vendors have a strong incentive to make it hard for you to switch to a competitor, and they might try. Educated clients, however, know to avoid vendor lock-in artificially created via proprietary formats and standards. Even without considering compliance, vendor lock-in hinders agile methodology and carries costly risks when changes are required, as highlighted in the threat intelligence lifecycle.
The principle of least privilege is the “need-to-know basis” of cyber security. While the principle applies to personnel, it also applies to vendor software and platforms. Every cloud-native application communicates with other services via APIs. It can be tempting to allow the free flow of data and not worry about it, but this is a significant oversight. Limiting privilege to absolute necessities, an essential practice in cloud-native application security assessments, severely limits the attack vectors of a malevolent actor (internal or external) who gains unauthorized access, thus reducing the risk of leaked secrets or compromised credentials.
A cloud-native application is only as secure as its weakest link, and in the case of vendors, that could be a long way down the software hierarchy. It’s enough for a vendor to rely on a compromised package to expose you, emphasizing the need for automated DevOps practices and security scanning to detect and mitigate software supply chain attacks, protecting against insecure code.
This interconnectedness means that a security breach in a seemingly minor component can have a domino effect, ultimately compromising the integrity and confidentiality of your entire system. It’s crucial to scrutinize your direct vendors and delve deeper into their dependencies and sub-dependencies.
Implementing robust software composition analysis (SCA) tools can help identify and address potential vulnerabilities within these nested layers of software, ensuring that your application’s security posture isn’t undermined by hidden risks lurking within your vendor’s codebase.
Data knows no boundaries, but legal jurisdictions beg to differ. When hosting data on-premise, you only adhere to local regulations, but things are more complicated when you store cloud data. California Privacy Act (CPRA) and the European (GDPR) are just two examples of data compliance that differ significantly. If your organization serves a regulated market, you must adhere to local laws and regulations, but your vendors may comply with different regulations.
When vetting vendors, it is essential to ensure they comply with the same standards you’re bound by and intend to remain compliant.
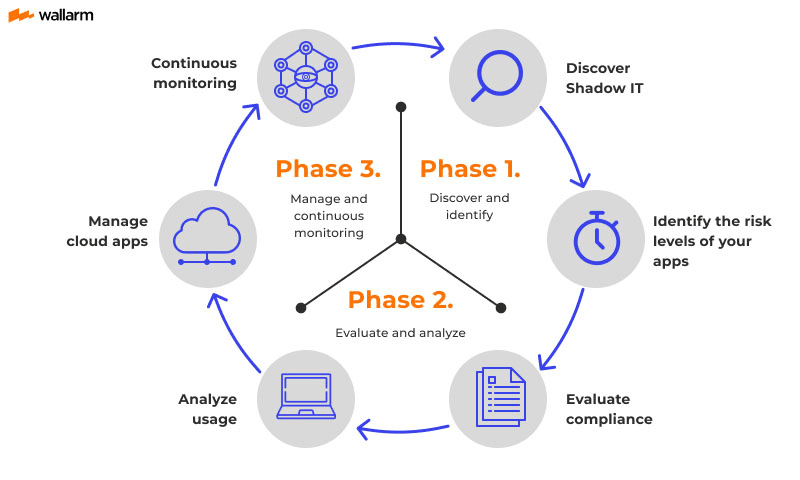
A lack of security awareness may lead developers to introduce new vendors into your ecosystem without your knowledge, creating shadow resources. It can occur when individuals or teams bypass established procurement and security review processes, opting for convenient but potentially risky solutions. For instance, unauthorized and ungoverned SaaS usage can result in data being stored in locations that need more security controls or compliance with regulatory requirements like GDPR or CCPA.
Furthermore, sensitive information, such as API keys, credentials, or customer data, may be transmitted or stored within these unsanctioned applications, exposing them to potential breaches. Insecure configurations and a lack of visibility into data handling practices within shadow IT environments also increase the likelihood of data exfiltration or unauthorized access.
The best way to combat Shadow IT is with security awareness training and robust technical controls. Implement clear policies and procedures regarding vendor onboarding and data handling.
“Trust but verify” takes on new urgency. Adopting a zero-trust approach isn’t just about mitigating risks – it’s about proactively safeguarding your cloud applications against the ever-evolving threat landscape. By embracing the principle of least privilege, holding your vendors accountable, and fostering a security-conscious culture, you lay the groundwork for a resilient cloud environment.
Spectral empowers your team to confidently build and deploy secure applications by automating vulnerability detection, secret scanning, and compliance checks. Don’t wait for a breach to expose your vulnerabilities – take control of your cloud security today. Get started with Spectral and protect your cloud-native future.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Quick announcement: with SpectralOps you can prevent data breaches by protecting your code from hard coded secrets and misconfigurations. You know how it goes: Every website,

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our