Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Open-source software has been a godsend for the development community. They bring lower development costs, faster application delivery, and greater flexibility; it’s no wonder nearly 90% of modern applications comprise third-party software nowadays.
That’s not to say open-source software doesn’t come with its share of pitfalls, including security risks and vulnerabilities. Its popularity might explain why software supply chain attacks increased 742% year-on-year between 2019 and 2022.

In such a setup, the only course of action is to minimize supply chain risks. This article discusses how third-party code weakens security posture and lists 10 preventive measures to reduce the threat.
Feeding open-source code to your application opens it up to threats like injecting malicious packages into the codebase, security vulnerabilities, and licensing complications. The vulnerabilities of open-source code allow a hacker to exploit the gaps since they are rarely built from a security standpoint.
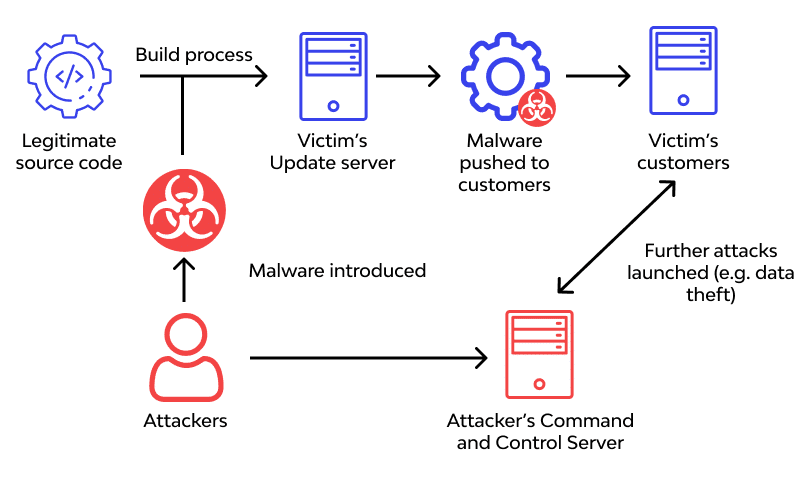
A cyberattack where an organization is attacked through vulnerabilities in its supply chain is known as Supply Chain Attack.
Supply chain attacks work in a domino style. Poor security governance on the vendor’s side is the first piece that can trigger a chain of events leading to a disastrous breach. It leads to vulnerabilities in open-source code. When you use this component within your application, an attacker can breach your and your client’s systems.
The 2020 SolarWinds attack is a classic example. Its ‘Orion’ platform had a supply chain threat injected into it, which was exploited, and 18,000 customer systems were breached. This malicious code cost American businesses and government agencies $100 billion.
Despite the growth of such attacks, IT leaders are increasing their usage of open-source software by 80%. According to Gartner 2022 studies, nearly 45% of companies across the globe will fall victim to software supply attacks.
Some of the latest critical supply chain attack trends include:
While these are the critical attack trends that hostile actors employ, you must also be aware of the common vulnerabilities that are likely in your system. If not addressed in time, they prove detrimental.
Some of the most common vulnerabilities that most developers struggle with to ensure absolute security are:
Most development teams overlook the significance of having a strong secrets management policy when writing code. Here are a few techniques to spot security gaps in your code and other misconfigurations.
Today, developers use a combination of open-source and third-party with their own code. In such a scenario, setting up a robust third-party or vendor risk management system is important. It explains the third-party landscape: what components are used, their access privileges, and security measures against them.
Best practices include:
When crowdsourcing code to an open-source community, it is possible to inherit the vulnerabilities through third-party dependencies. Using dependencies with vulnerabilities has been listed in the Top 10 security risks by OWASP. To manage this situation, put an efficient monitoring practice in place. While the market is flooded with tools to help identify and fix such challenges, pick the one that suits your specific purpose.
Vendors often release patches for known vulnerabilities to eliminate the security risk in their codebase. Automate patch management to keep track of missing patches and deploy patches to the software.
Since open-source software is free and widely available, hackers can easily access these third-party packages, look for vulnerabilities and exploit them. So, when using an external code for your application, do your due diligence before adding these components and giving them access to your sensitive data.
Some of the parameters for assessing a vendor or open-source community are:
The primary target of any cybersecurity attack is to access confidential information and resources, which makes securing this data of utmost importance. Achieve this through several frameworks for implementing a solid authorization and authentication practice.

Establishing Identity Access Management (IAM) best practices for developers will allow you to monitor all the user accounts and minimize risk exposure efficiently.
Adding layered security measures through Two-Factor Authentication makes it difficult for hackers to reach sensitive data. In addition to the password, you can have real-time authentication through SMS or other code-generation apps.
PAM (Privileged Access Management) is another monitoring framework to monitor accounts accessing critical business information. It is slightly more nuanced than IAM, focusing solely on accounts that access privileged information.
Zero-Trust Authentication is a practice where every request is dealt with suspicion, and a thorough authentication process is followed.
Discovering vulnerabilities before they cause damage is key to securing your application from supply chain risks. You can do this only by running multiple tests and assessments across the different stages of the software development process. To detect vulnerabilities, you can run tests, including:
You can ensure that any deviations or changes in your codebase are flagged by implementing digital signatures for your software components. This process of assigning digital signatures is known as Code Signing. It validates the authenticity of your source code, guaranteeing no vulnerabilities go unnoticed.
Employees are a vital defense against any cybersecurity threat. The onus is on the enterprise to define and enforce strict coding practices. It introduces consistency across the development practice and ensures that standard data protection and security policies are implemented across the organization. Employers can also automate policy enforcement to improve the overall security posture.
Conduct cybercrime awareness training for your employees to prevent creative attacks like phishing, clickjacking, and social engineering attacks.

With security moving upwards on the enterprise priority list, DevOps evolved into DevSecOps, where security is a part of every stage of the SDLC process. It is a framework that can identify and eliminate threats through adequate dependency visibility so everyone knows the dependencies and associated vulnerabilities. Here are some ways to achieve the same:
Using SCA tools is a powerful way of identifying what you are harmful ingredients you are adding to your software. These tools read through open source packages you used in your application and highlight all the vulnerabilities. It also goes beyond just open-source code. You can also use these tools to verify the risk appetite of Infrastructure as Code (IaC) and create SBOM.
As much as it is important to have security measures in place, you must also define your incident response workflow to tackle the eventuality of an attack. The plan should include a forensic analysis of the extent of the breach and a process to bring systems back to default mode.
The age of security oversight has long passed. Today, it is safe to say security precedes faster software delivery. While developers can accelerate their development process through third-party code, there is still the threat of supply chain risks. As long as the dependency on open-source packages remains, enterprises must pay extra attention to avoid any backdoor access to their sensitive data.
Implementing best security practices is easier said than done. Tools like Spectral can help to protect your code. Create a free account today.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions