Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
The software development landscape moves quickly. As organizations seek to innovate at increasing speed, developers find ways to develop and deploy digital apps faster. More than 500 million cloud-native digital apps and services are being deployed this year–the same number of apps developed over the last 40 years! Against this backdrop, ensuring software code security and quality has become more critical–and challenging.
Developers must manage large volumes of open-source and third-party components that make up their software supply chain. To run a secure workflow, they must ensure that these components comply with all licensing requirements and are free of vulnerabilities. One need only think of Log4j to remember why. This is where Software Composition Analysis (SCA) tools come in handy.
SCA provides developers with an automated and efficient way to detect and monitor the usage of open-source and third-party components, evaluate their security and license compliance, and reduce the risk of supply chain attacks. Let’s look into the security features a standard SCA tool has to offer and the best SCA tools in the market today.
When you use open-source and third-party components in your code, it’s critical to know how those components are programmed and used, so they don’t introduce security vulnerabilities and compliance issues, or impact the overall code quality, as was the case with Log4Shell. SCA tools can automate this process and provide further insights to identify and mitigate issues. However, you must proactively seek visibility into what third-party components are used in code. Otherwise, it would be difficult to look for issues that SCA tools are designed to mitigate in the first place.
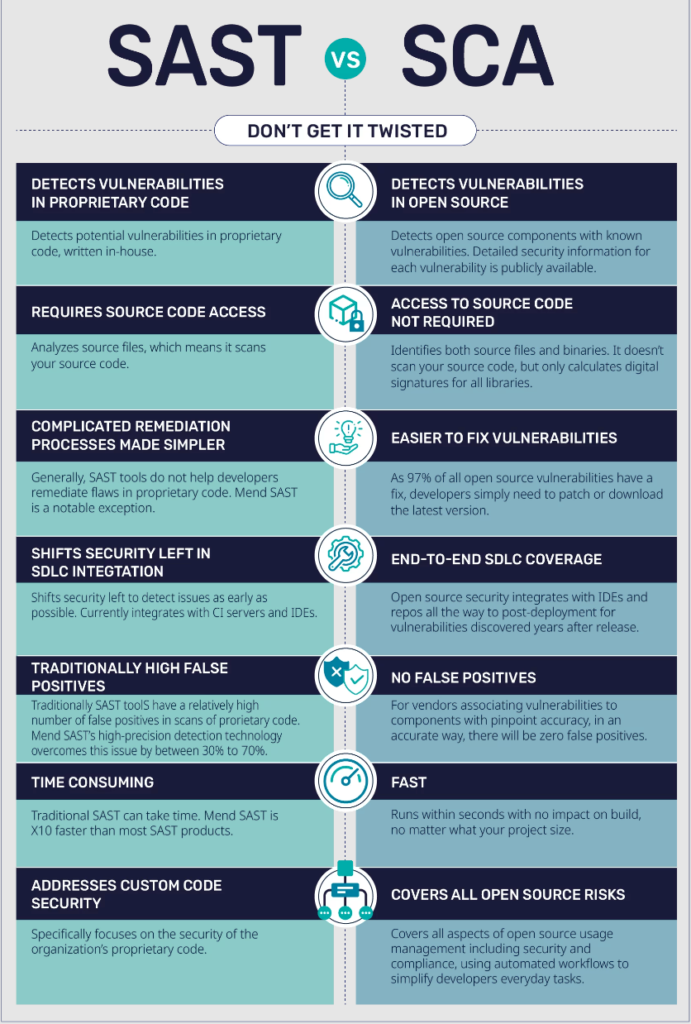
For reference, a similar range of resources known as Static Application Security Testing (SAST) tools are designed to identify issues like buffer overflows, cross-site scripting (XSS), and SQL injections. SAST and SCA tools serve different purposes: SAST tools scan your application’s codebase for potential vulnerabilities based on a set of predetermined rules. SCA instead focuses on identifying the open-source codebase so developers can manage their exposure to vulnerabilities and license compliance issues.
Here are the 5 prominent types of SCA tools to help you manage and analyze third-party and open-source components:
Regarding software development, speed, reliability, and security are three essential factors for any successful project. Here’s how having an SCA tool in your arsenal can help you gain on these three fronts:
Speed – SCA tools can help developers avoid a time-consuming, manual process of tracking and managing open-source components. This allows you to focus more on writing code, testing, and delivering software, ultimately speeding up the development process.
Reliability – With SCA tools, you can ensure that your applications are built using secure and reliable open-source components. By identifying potential security vulnerabilities or licensing issues early on, you can mitigate risks and ensure that your applications are built on solid grounds.
Security – SCA tools have a crucial role in ensuring an application’s security. By identifying and addressing any security vulnerabilities or dependencies on outdated components, SCA tools help you protect your applications from potential attacks.
With that in mind, here are some of the key features that you should look for when choosing an SCA tool:

Spectral provides a powerful suite of capabilities to ensure that the open-source components you’re using are secure and always compliant. Key features include automated scanning, customizable policies, and advanced rule creation, allowing you to monitor and track your dependencies. The tool also provides an API-first approach, making it easy to integrate into your present DevOps workflows.
Focusing on developer experience, with user-friendly interfaces and workflows that prioritize speed and ease of use, Spectral provides detailed and actionable reports to help developers stay informed on potential security risks and take immediate corrective action.
This tool is best suited for DevOps teams on medium to large-scale projects and teams that need an SCA tool that can provide advanced rule creation and flexible customization options.
Learn more about the product and its pricing here.

Snyk is a cloud-native security platform that allows developers to find and fix vulnerabilities in open-source dependencies. Snyk offers automated scans, integration with popular developer tools, real-time vulnerability alerts, and a vast database of known vulnerabilities. With it, you can apply patches and upgrades with just a few clicks.
Snyk is best known for its simplicity and ease of use. It’s a great option for most development teams and organizations that value speed and agility due to its real-time vulnerability warnings and vulnerability database.
Snyk offers 6 pricing editions ranging from $0 to $178.

Azul Vulnerability Detection is an agentless cloud service designed to continuously detect known vulnerabilities in Java applications in production. Its purpose is to help organizations extend their software supply chain security to production, resulting in more accurate results with no performance penalty and no false positives.
The tool is built on OpenJDK and plays well with other Java technologies such as Kafka and Spark. It boasts 24/7 problem resolution support, strict SLAs, and 100% customer satisfaction rating. Flexible pricing options accommodate various requirements for performance, security, and value, starting at $35,000 per year as a base charge for Premium support level. Quotes can be requested here.

In February 2023, ShiftLeft rebranded to Qwiet AI and turned its focus to the mission of using AI to “prevent the unpreventable” by detecting zero-day and pre-zero-day vulnerabilities in code.
Intelligent SCA is one of the key components of its platform. It uses AI to examine the flow of data across an entire software application to determine which open-source libraries contain vulnerabilities that attackers can reach, flagging to developers what needs to be fixed immediately. The solution aims to reduce noise so developers can focus on meaningful, high-fidelity results that have the greatest impact. A free demo is available for new customers.

OSV Scanner is an open source SCA solution developed by teams at Google. OSV-Scanner provides an officially supported frontend to the OSV database that connects a project’s list of dependencies with the vulnerabilities that affect them. Since the OSV.dev database is open source and distributed, it has several benefits in comparison with closed source advisory databases and scanners.
Where OSV Scanner really becomes useful is when it is deployed through Jit.io. Jit.io is a DevSecOps orchestration tool that deploys open-source security solutions for new pull requests through the CI/CD. Jit.io+OSV Scanner makes for a security tool that has 0 impact on software development speed while still providing obvious security benefits.

CAST Highlight is a cloud-based SCA tool for measuring and managing software applications’ quality, risk, and cost.
Its comprehensive software inventory identifies open-source components and potential vulnerabilities, enabling efficient software supply chain management. The tool provides metrics, including code complexity and architecture health, to help teams prioritize areas requiring attention and allocate project resources efficiently. It is also easy to integrate with various development tools, including Jira and GitHub.
The annual subscription to CAST Highlight starts at $27,000 for SCA Insights and goes up to $36,000 for the Complete Insights package.

SOOS SCA + DAST is a combo of 2 security tools that provide both software composition analysis and dynamic application security testing (DAST) capabilities. They help developers identify and manage open-source vulnerabilities, providing remediation guidance, prioritizing issues, and allowing them to test applications for security vulnerabilities while running.
SOOS Core SCA Platform is priced at $199 per month, while SOOS DAST comes at $398 per month.

Black Duck SCA helps organizations manage open-source components and potential vulnerabilities in their code. It identifies open-source components, checks them against a vulnerability database, and provides detailed reports. It easily integrates with popular development tools and uses advanced machine learning and AI capabilities to detect potential threats.
It is best suited for larger organizations with complex software ecosystems looking for a comprehensive and powerful SCA tool that can automate their entire process to save time and reduce the risk of human error.
The subscription to Black Duck SCA is priced based on customer requirements.
SCA is non-negotiable when it comes to ensuring the reliability, security, and maintainability of software applications. But there’s no silver bullet for ensuring application security. SCA tools primarily focus on pre-production environments, leaving developers to address issues discovered post-production. That’s why at Spectral, we focus on helping developers catch issues earlier in the development process and provide actionable insights for remediation. With that in mind, combining SCA with other security testing tools can create a more comprehensive and effective approach to application security. Access our free content or join our open-source community to learn more.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Continuous integration and delivery are necessary in any production level software development process. CI/CD are more than just buzzwords. Rather, it is a fully-fledged methodology of