The Beginner’s Guide to Preventing Data Breaches in Your Code
Quick announcement: with SpectralOps you can prevent data breaches by protecting your code from hard coded secrets and misconfigurations. You know how it goes: Every website,
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open source in their development pipeline.
The reasons are clear – it’s cost effective, it offers quick feature integration, ease of access and is often maintained by others. There are also risks to open source code, with security and compliance being two of the top factors.
Lets face it, when developing software you want to keep costs down and deliver fast. What you do not want is to waste time re-inventing the wheel by writing your own implementation of code that others have previously released as open source. Not to mention the added value of fewer and faster bug fixes, open standards and of course – community support.
However, nothing in life is perfect, and open source solutions are no exception. FOSS is rarely well documented or tested. Moreover, with the transparency of open code comes the risk of many eyes looking for vulnerabilities to exploit (and potentially weaponize).
More and more software companies integrate open source into their code. As a result, the need to proactively monitor projects for continuous integration (CI) and continuous delivery (CD) through DevSecOps (development security operations) has become vitally important. The role of DevSecOps includes a number of functions and tasks that covers both pre and post development stages:
Unlike open source libraries maintained by internet giants, most open source libraries targeting specific features may not be designed with security in mind. In addition, they are often maintained by a single developer or a small team of “volunteer” developers (if not abandoned altogether). How often the code is audited for vulnerabilities is a complete unknown and almost certainly not a part of any formal process.
Dependencies in an open source library may integrate code from other open source libraries which themselves may be vulnerable. Beyond exploits in the code itself, there are other risks of forked repositories with intentionally vulnerable code masquerading as the original repository, as well as abandoned repository take-overs.
As use of open source libraries spread, the number of vulnerabilities discovered has grown significantly. In 2019, 968 new vulnerabilities were assigned a CVE (Common Vulnerabilities and Exposures) designation, up from 421 in 2018 – a 224% increase year over year. Add to that the fact that 7 in 10 applications have a security flaw in an open source library, while attacks targeting open source components have risen by 430%.
The main culprit in security breaches lies in the difficulty of tracking hundreds of dependencies used by open source libraries developers rely on. This is not limited to the vulnerabilities themselves, 90% of which are fixed in a timely manner. Without knowing that a down-stream open source library is vulnerable or has a fix available, vulnerabilities may remain lurking in code for years, waiting for hackers to exploit.
Real life examples include typosquatting Python libraries stealing SSH and GPG keys and critical vulnerabilities found in SaltStack’s open-source event-based IT automation and configuration management tool Salt. In the case of Salt, the vulnerabilities were actively exploited within days of it being patched, before several prominent users of the tool noticed the issue and installed the fix.
It’s worth noting that open source risks are not limited to vulnerabilities and exploits. A major pain for software developers is realizing (after the fact) that code included from an open source library is using an incompatible license (e.g. GPL), requiring additional rewrites and delaying the product’s deployment.
It’s pretty obvious that securing code against open source vulnerabilities requires tools and services integrated throughout the software development lifecycle. It is also quite unsurprising that there’s a broad selection of such tools and services out there.
To make your search easier, we collected the top open source security solutions for DevSecOps.
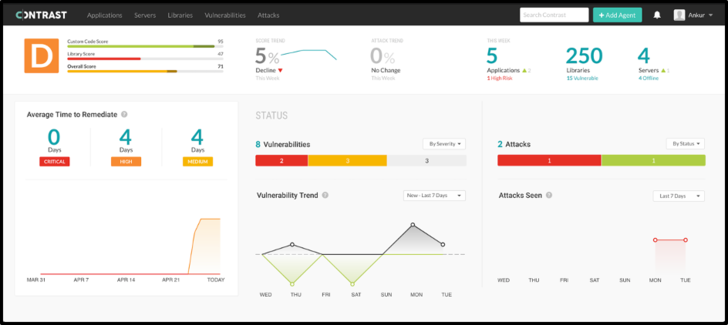
Alerts are triggered when risks and policy violations are detected anywhere across the SDLC. In production, Contrast monitors, blocks and alerts on attacks targeting open source libraries and components.
Price: Not listed, but it is priced per-application. There is a demo available and you can try the tool with one app for free.
Pros: A cool interface and low false positive reports.
Cons: There is room for improvement in the reporting features as users claim it is not suitable for a high-level view that can be presented to management personnel. In addition, Contrast lacks support for client-side libraries such as jQuery or JavaScript. Contrast is also described by users as difficult to automate as setup differs for each application.
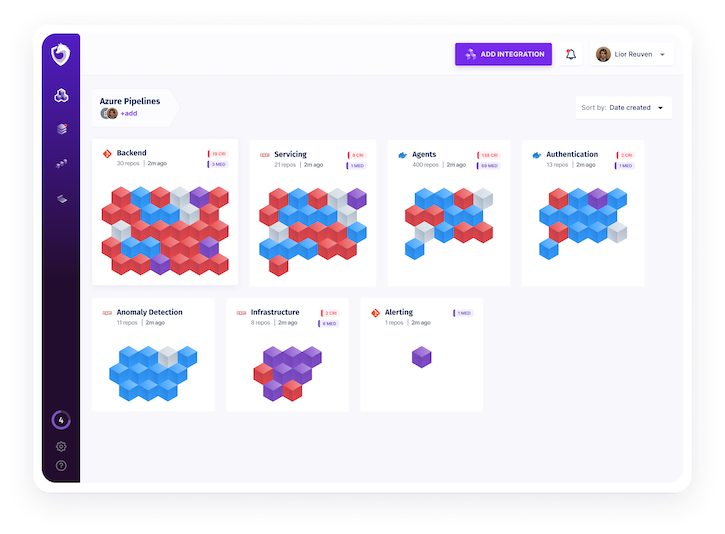
Price: Spectral does not announce its pricing. You can request a free trial by clicking the “Get Started” button on Spectral’s home page.
Pros: Highly optimized, an average sized repository can take less than a second to scan. Very flexible, scanning logs, code, apps, images and more.
Cons: While Spectral introduces many interesting new features, it is still the new kid on the block and as such, it still has to prove its worth.
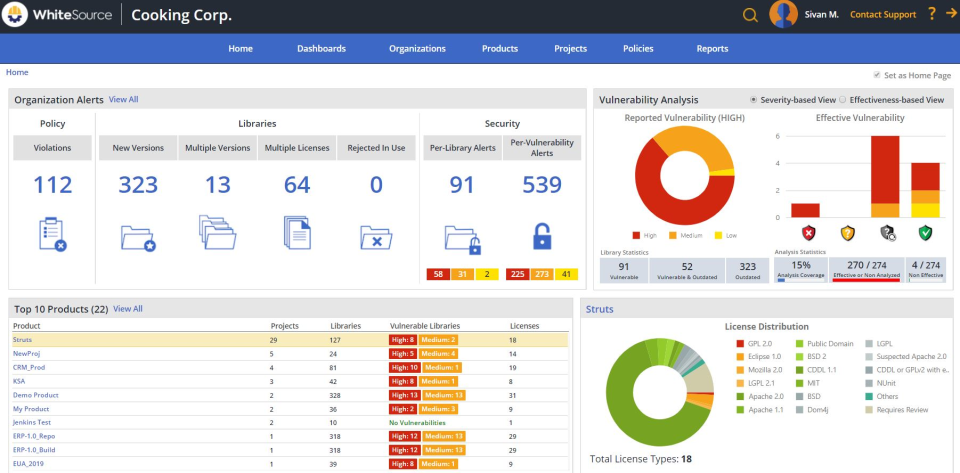
WhiteSource promises to reduce up to 85% of security alerts by prioritizing vulnerabilities based on whether your proprietary code is utilizing them.
Price: The annual pricing depends on the number of contributing developers and ranges from $5,460 for a single developer up to $192,400 for 500 developers. A free trial is available.
Pros: The ‘fix suggestions’ feature traces back to where the vulnerability is within your code and offers suggestions on how to fix the issue. The attribution and license due diligence reports satisfy the required software licenses copyright and component usage disclosures.
Cons: The user interface and user experience are not as intuitive as they could be. Some detected libraries do not specify where in the source they were used.
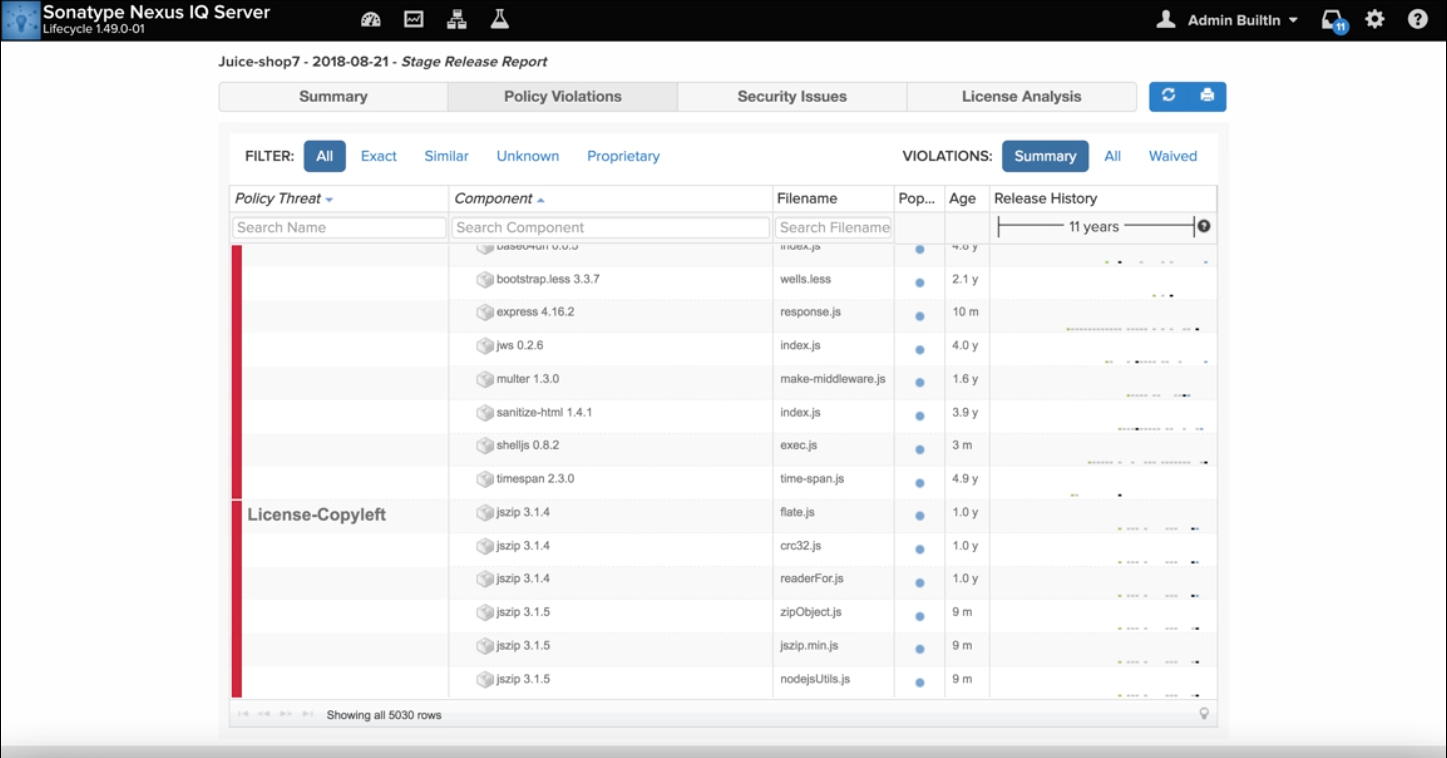
Price: Nexus offers multiple products covering different aspects of open source security with annual subscription prices ranging from $120-780 per user and $1,000 per app.
Pros: The vulnerability description clearly shows where the problem is and the software offers an explanation of the vulnerability as well as a recommendation on how to fix the problem. This is especially helpful when there is no possibility to fix the issue by updating the library. The low rate of false positives keeps developers happy and the product features a REST API that can be used for automation.
Cons: Mainly Java centric with support for other languages somewhat lacking. The API is fairly limited, lacking support for the more powerful RESTful API. In addition, users have claimed that the user interface is not very intuitive.
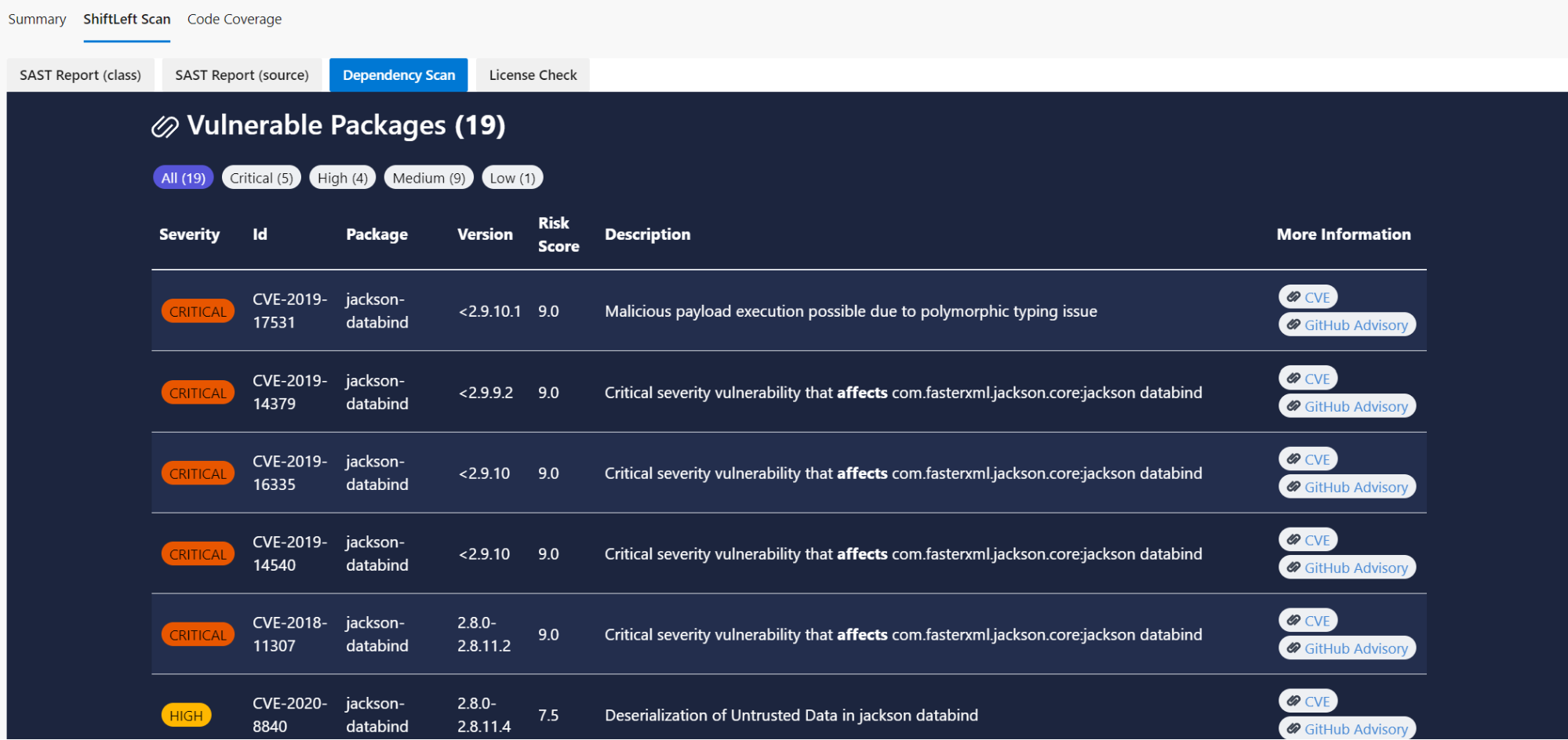
Price: As an open source project released under the GPL3 license, ShiftLeft Scan is free to use.
Pros: Privacy! Your code, dependencies, and configuration never leave your builds. All scanners, rules, data and vulnerability databases are downloaded locally.
Cons: It looks like ShiftLeft is shifting away from Scan and no longer providing support for the solution, focusing on their new “NextGen Static Analysis” product instead.
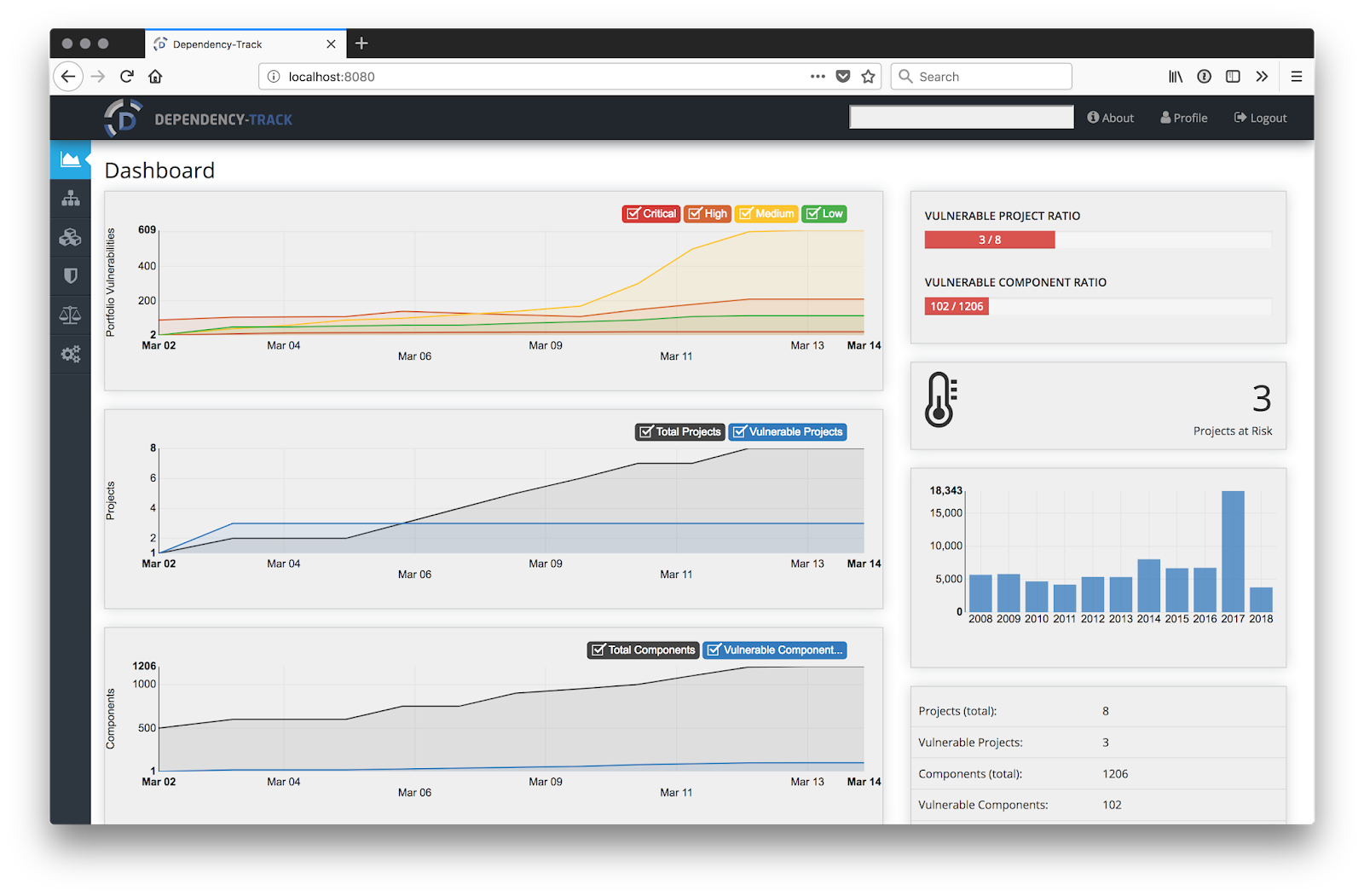
Price: Released under the Apache 2.0 license, Dependency Track is free to use.
Pros: Well documented and easy to integrate. Includes an extensive automation API, and tracking for application, library, framework, operating system, and hardware components.
Cons: With a small community of part time developers, fixes may be harder to obtain and support is limited to volunteers.
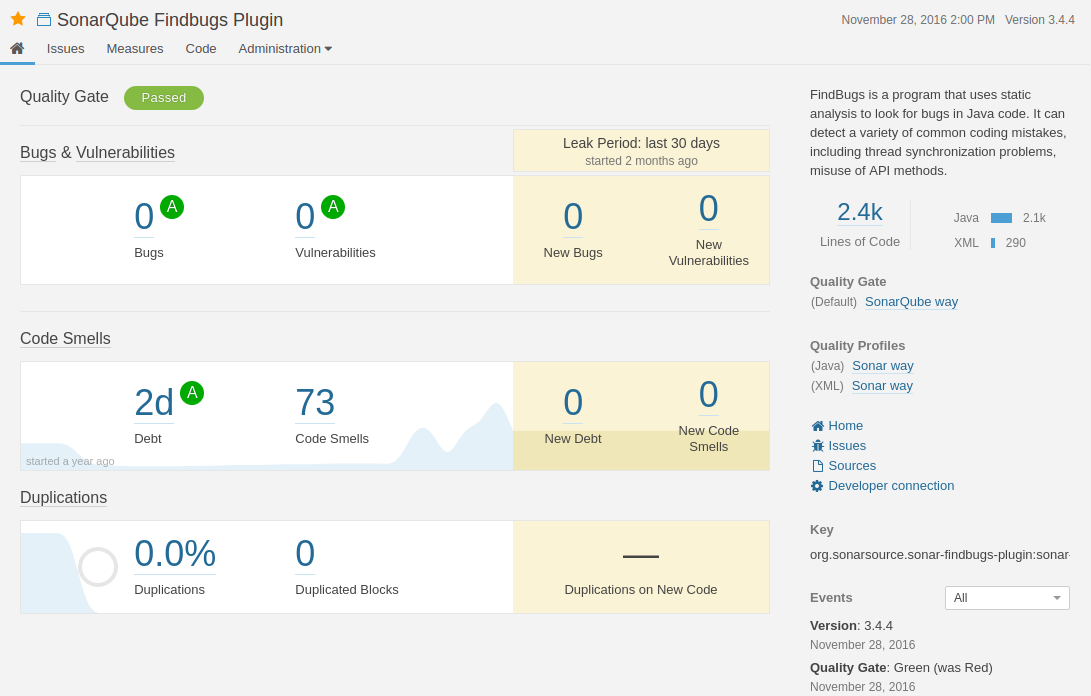
Price: A free community version is available while a developer version starts at 120 euro plus additional cost based on the project’s line count.
Pros: A friendly UI that is easy to use and understand. A security hotspot feature that identifies where your code is prone to have security issues.
Cons: Users claim it is difficult to set up without support and documentation is not clear enough. They also note that SonarQube sometimes misses security breaches in code that were caught by competing products.
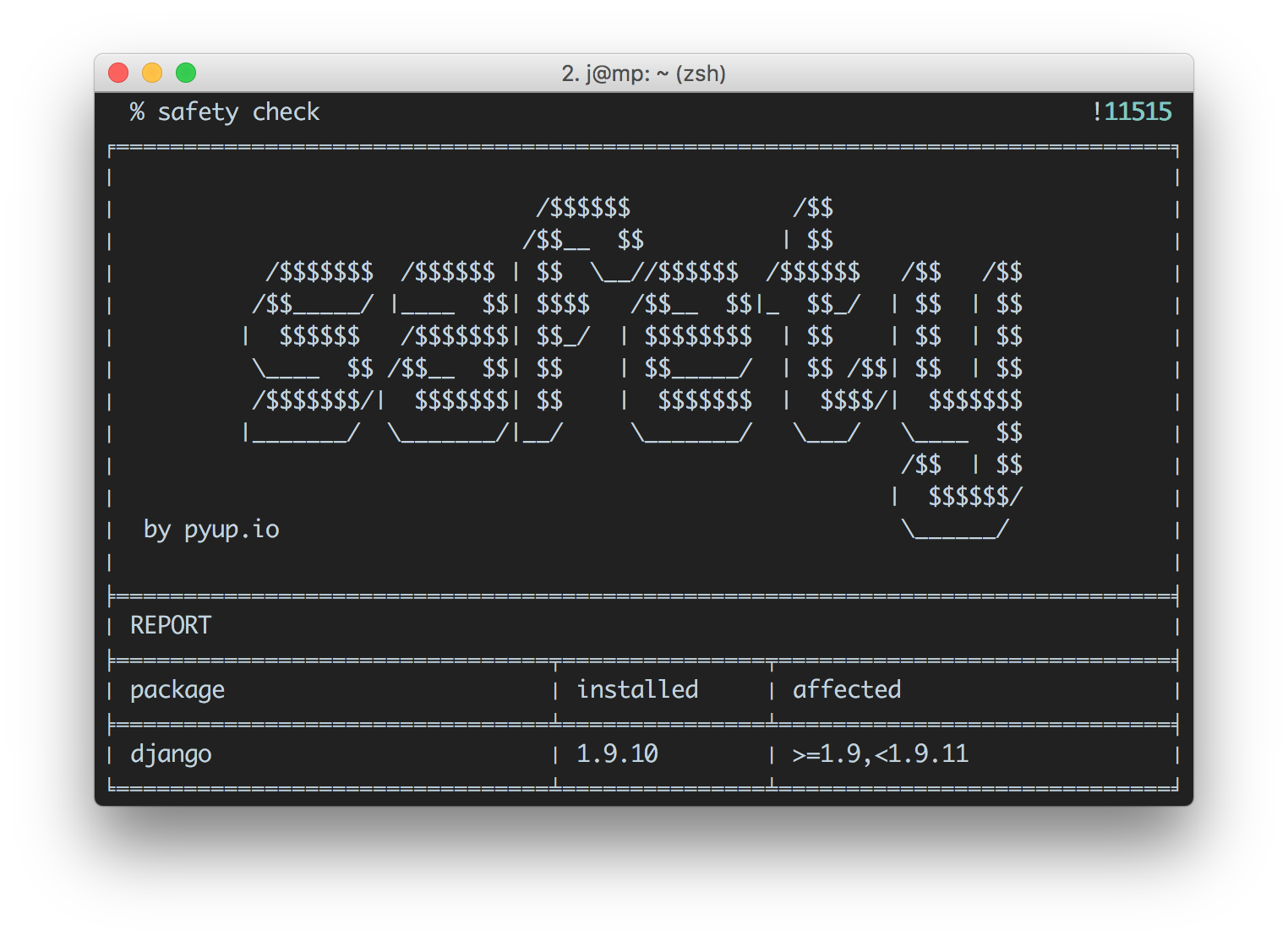
Price: As an open source tool released under the MIT license, Safety is free to use. However, the vulnerability database is only updated once per month. For more frequent updates, you will need to invest $99/month on a subscription.
Pros: Simple to install and use.
Cons: Very limited feature-set, with support only for the Python language.
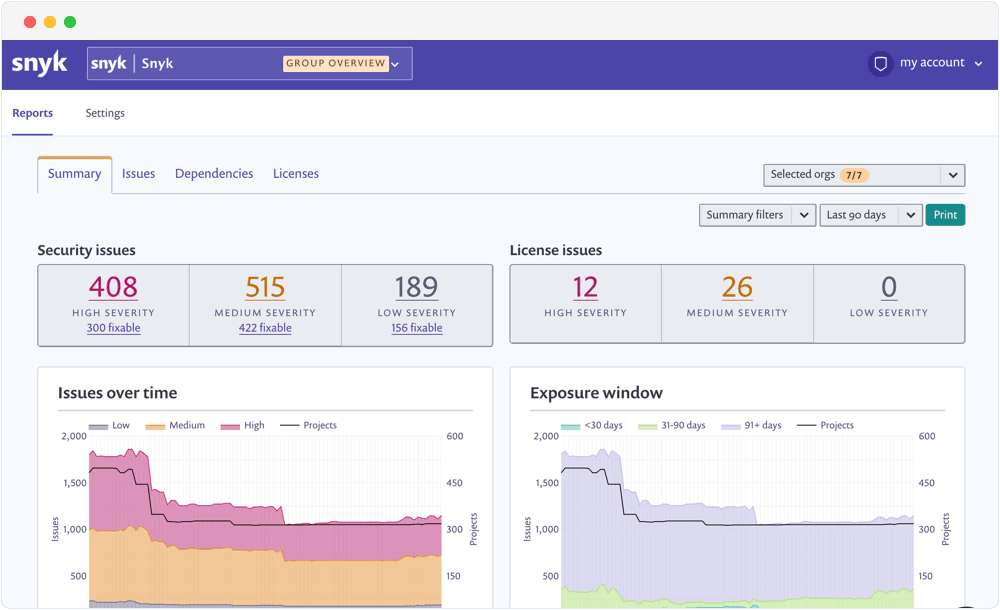
Price: Snyk includes a limited, free plan for open source developers and more feature rich Standard and Pro tiers starting at $417 and $1,999 respectively, billed on an annual basis.
Pros: Powerful Kubernetes, GitLab and JIRA integrations, as well as rich vulnerability information in terms of layer of origin and dependency tree.
Cons: The generated reports are not as clear as they could be. Filtering could be enhanced to improve clarity and notification could be ranked on a greater scale. In addition, users claim that more documentation and tutorials are needed.
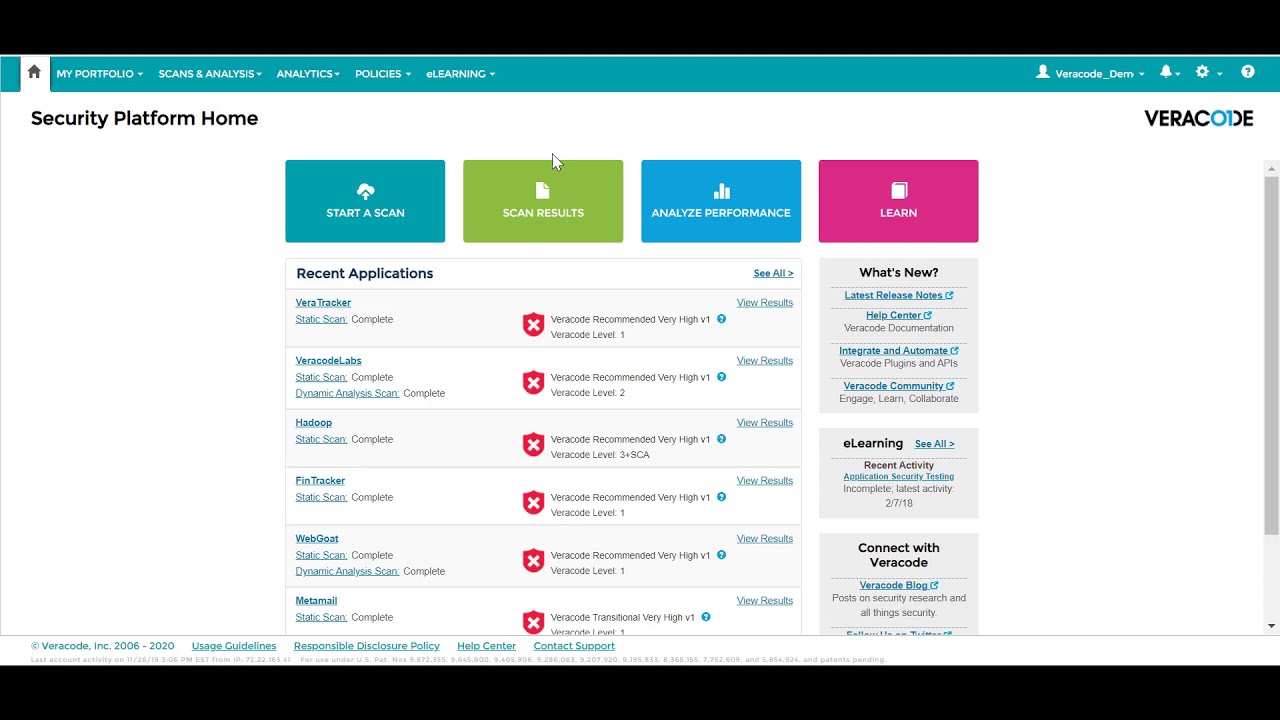
Price: Veracode does not announce its pricing. You can request a demo or a price quote.
Pros: Veracode uses data mining, natural language processing and machine learning to expand its SCA database beyond the National Vulnerability Database. It provides both static and dynamic scanning with good IDE integration support.
Cons: Some users found the user interface and user experience to be a bit confusing. The generated reports could be clearer and more concise.
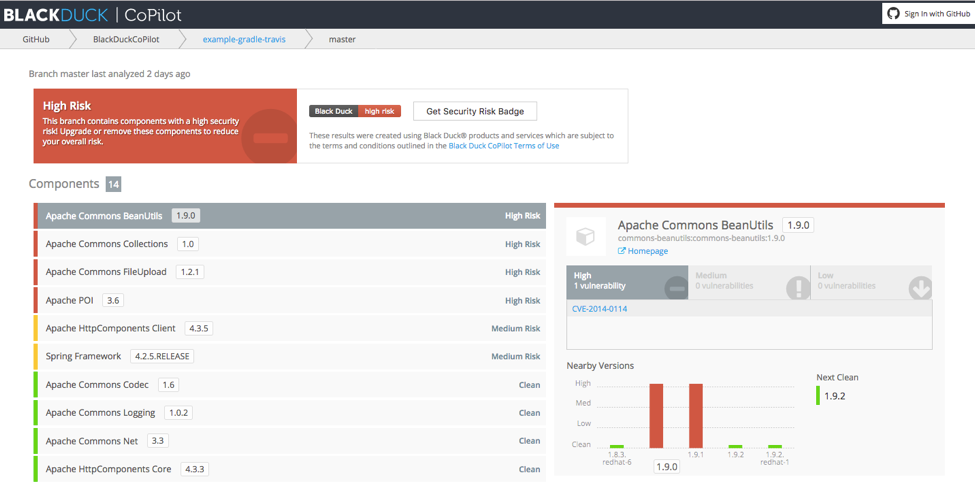
Price: Synopsys Black Duck does not announce its pricing. You can request a demo or a price quote.
Pros: Auto analyzes components where other vendors only make fuzzy recommendations. Good training videos and professional support.
Cons: Users say that Black Duck needs to be more user-friendly. They also cite confusing setup and limited scanning for larger projects that must be split to process.
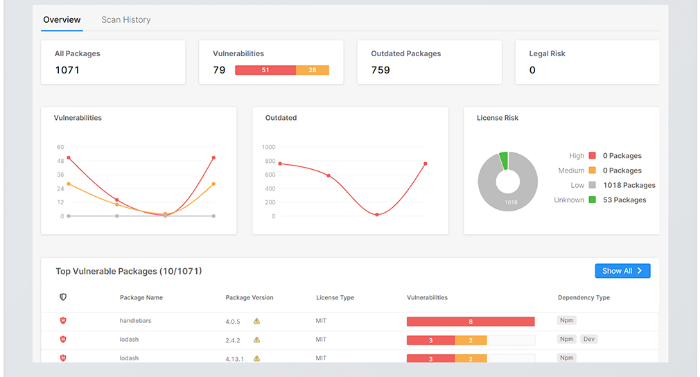
Price: Checkmarx does not announce its pricing. You can request a demo.
Pros: Analyzes open source code in all common languages and frameworks while being very user friendly. Always ahead of the game when it comes to finding any vulnerabilities within the database.
Cons: Creating/Editing custom rules is difficult due to additional licensing cost and UI complexity.
Open source is becoming ubiquitous. The great value it provides encourages software developers to integrate open source deep within their projects. With popularity expanding, hackers are looking at every opportunity to exploit open source vulnerabilities.
To remedy this, DevSecOps processes and policies must be enforced with intelligent tools. In our list, we included the top open source security tools that can help software development teams and organizations side-step DevSecOps issues without breaking a sweat. That said, it’s worth noting that security is a moving target. Which means that new tools and technologies are released on a frequent basis. If we missed a particularly new player in the DevSecOps field – do let us know in the comments below.
Quick announcement: with SpectralOps you can prevent data breaches by protecting your code from hard coded secrets and misconfigurations. You know how it goes: Every website,

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions