Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Imagine a world where a single line of code, tucked away in a common library or framework, could bring your entire digital world to a screeching halt—welcome to the ever-evolving landscape of software supply chain security.
Like any supply chain, the security of your software is only as strong as the weakest link in the system that produces and delivers working code. 62% of surveyed organizations in 2021 experienced a software supply chain attack, which reflects an ever more complex software ecosystem. Here’s a look at 10 of the most common software supply chain risk factors and what you can do about them.
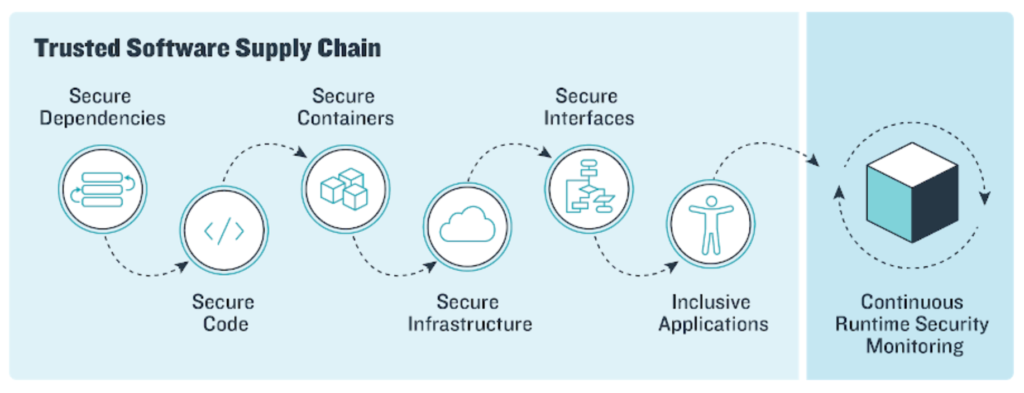
Software supply chain security refers to efforts to manage security risks arising in the processes, components, and tools needed to develop and run modern software applications. Hackers can either gain knowledge via supply chains or conduct malicious activities within supply chains.
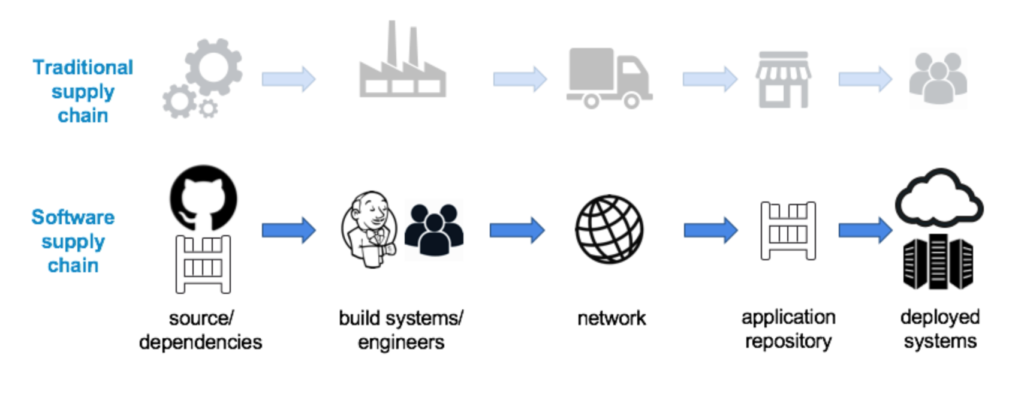
Gone are the days of monolithic applications developed in-house with an easily visible supply chain. Developers today build their apps as a collection of microservices, often using open-source components to provide desired capabilities and speed up software releases. These apps then get deployed on virtualized infrastructure like containers, which are hosted in the cloud.
Some examples of supply chain security breaches that even people outside of cybersecurity have likely heard of include Solarwinds and Log4j. The former saw threat actors weaponizing Orion, an IT monitoring solution with malicious updates and infiltrating the networks of companies like Cisco and the US government. The latter saw a zero-day vulnerability in Log4j, a Java-based logging utility common in enterprise IT ecosystems worldwide.
Software supply chain vulnerabilities have the potential to impact thousands of organizations that depend on vulnerable components that play a part in their software ecosystems. The risks range from nation-states conducting espionage to large-scale ransomware attacks encrypting sensitive data.
When supply chain vulnerabilities impact just a single organization, the consequences can still be severe, with malware, backdoors, or other malicious code finding its way into your environment. In the worst cases, critical systems go offline, customers lose money, and regulatory penalties ensue from sensitive data loss.
Here’s a list in no particular order of ten major software supply chain risks, how they work, their consequences, and what you can do to prevent them.
It’s important not to forget that the definition of a supply chain includes the code developers write to build their apps. This includes how different services speak to each other through application programming interfaces (APIs). Protecting code against vulnerabilities should include secret management and solutions capable of finding harmful security errors in code and configurations.
Third-party vendors, partners, and service providers all play a role in the modern software ecosystem. Whether it’s through running apps on cloud instances, procuring commercial libraries/frameworks, or using services to streamline software availability, these dependencies subject your code to possible sources of risk.
The discipline of third-party risk management is essential for a comprehensive understanding of your dependencies, including the access privileges specific third parties have to your code. Managing these risks helps to avoid the kinds of trojans, spyware, and backdoors that lead to cyberespionage against the US government.

Beyond code repositories, various public-facing distribution systems provide an easy download of new versions of apps and services. Common locations include sites like Softpedia and FileHippo. App stores are also veritable software distribution systems. Hackers could compromise these distribution systems and install backdoors that enable the infiltration of your software environment. Be careful about where you source any software from.
One estimate says free and open-source code constitutes 70-90% of modern software. Public repositories are great in making code from various open-source projects available to everyone on the Internet, but they carry significant software supply chain risks.
A particular concern is typosquatting, where authors write malicious code with similar project names to legitimate packages. It’s easy to glance at a name and assume it relates to the usual legitimate package. Unfortunately, upon downloading a typosquatted package, developers unknowingly introduce malware into their code. A similar issue is impersonating other authors or brands to dupe people into downloading malicious components.
Modern software development workflows use continuous integration and continuous delivery to automate, become more efficient, and spark more innovation in the apps developers create. Central to CI/CD pipelines are code repositories, containers, and build servers that have the potential for compromise.
Common build tools include Buddy, Jenkins, and Bitbucket. Not letting automation and innovation supersede any concern about software security is important. Make sure to adopt IaC (Infrastructure-as-Code) and PaC (Policy-as-Code) in addition to leveraging the benefits of continuous security testing.
Hijacked updates have appeared prominently in news stories about cybersecurity in recent years. In one incident from 2019, Asus pushed a malicious software update to thousands of users after malicious actors compromised the company’s IT environment.
These hijacked updates pose a software supply chain risk when your code and its infrastructure depend on other tools that sometimes need updating. The point here isn’t to avoid applying software updates; it’s more to recognize this risk and exercise due diligence in the vendors whose tools and apps play a part in your software supply chain.
Using only signed code is a good security best practice because it uses digital signatures to confirm the authenticity of the code. Unfortunately, though, code signing is only as effective as its implementation. Code signing is subject to being undermined by stolen private keys to digital certificates or the use of expired/revoked certificates. While the mitigations here are obvious (secure private keys in hardware security modules, validate certificates), remember that vulnerable code will remain vulnerable even if signed.
Excessive access to resources across the supply chain often makes software security incidents more severe. Developer tools, repositories, cloud systems, and other tools involved in software development should all have their access stringently controlled. Ideally, implement the principle of least privilege throughout the supply chain to ensure each component and person has only the necessary access required for your software to function as it should.
To go one step beyond access control, educate everyone involved in the software supply chain on important security concepts. This calls for dedicated training and awareness programs.
Connected devices like endpoint laptops and workstations are also involved in the software supply chain. The concept of security hardening is a pivotal way to strengthen the resilience of connected devices and your code against common compromises. Defense measures worth considering include encryption, data loss protection, advanced endpoint detection and response, and standard antivirus scanners.
Suppliers and business partners are a source of software supply chain risk to the extent that they provide services of applications that you use or collaborate on. To help reduce these risks, include vendor dependencies in source code control while not neglecting the helpful tasks of third-party risk assessments and validations.Contractual agreements should specifically mention vulnerability disclosure.
To prevent costly mistakes, software supply chain security requires a holistic approach that addresses all possible weak links in the chain, from the code your developers write to the tools you work with and the companies you partner with. Developers can’t downplay the role they have in hardening security. With that in mind, check out our checklist for security hardening for developers: Get your free security hardening checklist now.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions