Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
When it comes to software development, certain security measures need to be baked into the core of the development process. This ensures long-term compliance and maintains the reputation of the organization by preventing data leaks.
Depending on a number of circumstances, the cost may vary, but a breach is not something any organization can afford. According to a recent IBM report, the average cost of data breaches has risen in 2021 to $4.24 million, from $3.86 the previous year.
This is why frameworks for auditing and reporting have been established. SOC 1 and SOC 2 are the most common auditing and reporting frameworks for DevSecOps. This article will compare the differences between the two, and provide insight into which you may choose for different objectives.

SOC stands for System and Organization Controls. The American Institute of Certified Public Accountants (AICPA) developed these controls as a set of standards. They’re designed to assess how well a company manages and regulates its data, whether it’s financial, customer-related, or otherwise.
SOC standards are designed to reassure customers and third parties that the service providers with whom they engage have the necessary procedures in place to protect their data.
When a company is being SOC audited, it is being evaluated to those standards.
There are several types of SOC audits, including SOC 1, SOC 2, SOC 3, and SOC for cybersecurity.
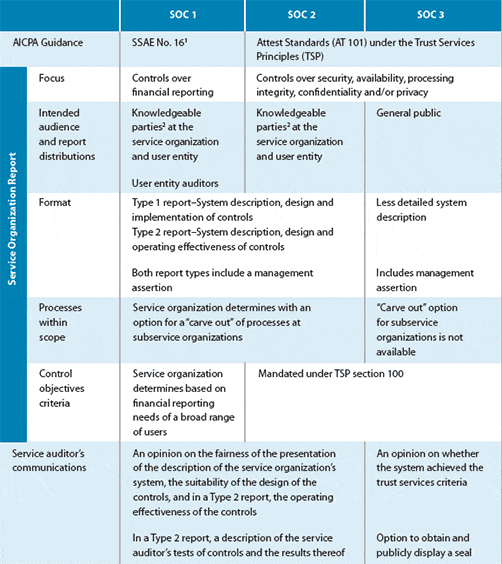
The audit’s result is the SOC report. Its goal is to provide a comprehensive, consistent, and unbiased assessment of a company’s compliance with relevant standards.
It informs external stakeholders about the policies and procedures in place, as well as how well they are followed, in order to accurately assess the potential risk of engagement.
The following are the reports that are part of the SOC framework:
SOC 1 is a report that covers financial reporting controls.
SOC 2 expands on SOC 1 by addressing organizational oversight, risk management, vendor management, and regulatory oversight procedures.
SOC 3, which requires less formalized documentation, is a simplified version of SOC 2.
SOC for cybersecurity is a voluntary framework designed to assist organizations in communicating their cybersecurity risk management programs and the effectiveness of their controls.
Furthermore, SOC 2 reports do allow for the inclusion of additional criteria relating to industry-specific frameworks like the HITRUST CSF (of the Health Information Trust Alliance), HIPAA (for protecting sensitive patient health information), and NIST (National Institute of Standards and Technology) (standards for the security of information systems at federal agencies).
A SOC 1 report, according to the AICPA, explains how well a company’s internal controls over accounting and financial reporting are structured, how effective they are, and whether they help the firm reach its financial goals.
External auditors and the management teams of the organization’s clients are the intended audiences for SOC 1 reports.
SOC 1 reports are divided into two types:
SOC 1 Type I is meant to demonstrate if internal controls are well-designed to effectively prevent financial transaction and statement data errors, with testing done at a single point in time.
SOC 1 Type II assesses the operational efficacy of internal business, and IT controls and is intended to reduce the risk of financial inaccuracy through ongoing testing.
SOC 2 is mandatory for technology services, and as such, is in high demand.
SOC 2 covers:
SOC also has two types of reports:
SOC 2 Type I is a report of policies and procedures at a single point in time.
SOC 2 Type II is a continuous process where systems, policies, and procedures are audited over at least six months.
The customer’s management team, like with SOC 1, is among the readers and consumers of SOC 2 reports, but so are prospective customers, business partners, external auditors, and regulators.
As we have seen, SOC 1 and SOC 2 do differ from one another. Below is a quick summary of these differences:
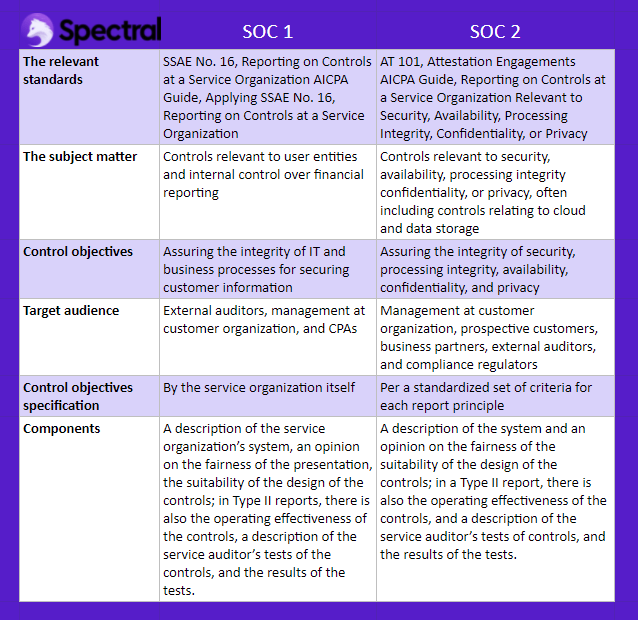
The sensible question is which audit is best for your company; SOC 1, SOC 2, or both?
When assessing which audit you should pursue, you should look at multiple factors such as the number of services your organization provides, the number of locations from which it operates, and lastly, how your users access your services.
If your organization has a software development division and provides software-based services, SOC 2 is a must. Part of the DevSecOps philosophy is having a secure culture among developers. If developers are aware of a set of regulations such as SOC 2, then you are already on the right track to maintaining compliance.
An organization that provides solutions and services that may impact its clients’ internal controls over financial reporting, such as providers of billing and collections data-related software, should pursue a SOC 1 certification.
Regulations such as PCI-DSS and HIPAA do not require SOC 2. Regardless, organizations that process or host sensitive data will need to show that they take the necessary precautions to protect this information and prevent breaches.
Having the proper controls in place and demonstrating their effectiveness, robustness, and reliability through SOC 1 and SOC 2 reporting is a surefire strategy to increase market competitiveness, organizational stability, and brand trust.
While the two reports appear to be similar at first glance, as we’ve seen, they’re not. SOC 1 is concerned with a company’s financial processes and reporting, while SOC 2 is concerned with data and technology security.
Though SOC 2 compliance isn’t mandatory, it does offer substantial benefits. Among others, it allows SaaS providers to boost their credibility and provide a superior service compared to those who do not. That said, SOC 2 compliance can prove a challenge for DevSecOps as it requires integration of security standards in the CI/CD pipeline at every part of the development cycle.
SOC 2 is essential for any organization looking to provide software services and a core ingredient to SOC 2 compliance is a SAST solution as a foundation of your CI/CD pipeline cybersecurity stack.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions