Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Security testing? Ain’t nobody got time for that. Or budget. Or the necessary skills to align coding practices with organizational and regulatory compliance efforts. Developers are too busy racing against themselves and the expected development velocity of modern development teams. Mistakes are bound to happen.
As many as 38% of IT and InfoSec professionals in the software industry estimate that between 21% and 40% of their code contains vulnerabilities, and 13% have identified vulnerabilities in most (61-80%) of their code.
How can you catch these vulnerabilities and issues before they become threats that turn into breaches? An excellent place to start is by getting to know two of the most common approaches to application security testing: SAST and DAST.
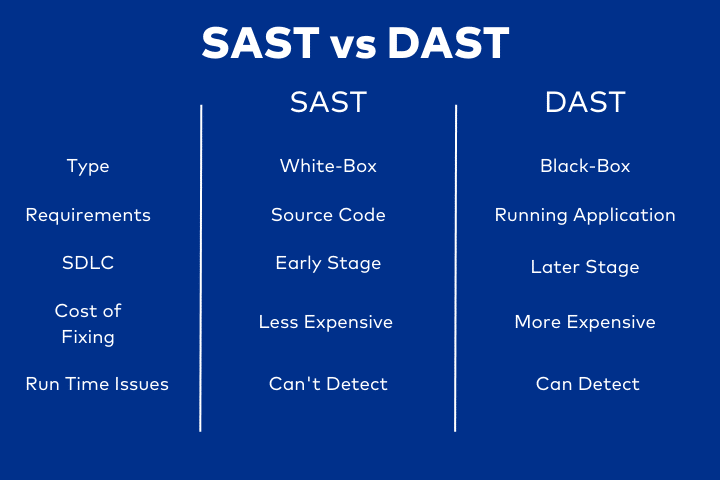
SAST (Static Application Security Testing) is automated white-box testing that checks an application’s code for potential vulnerabilities and known issues in its static (non-running) state. In white-box testing, the tool has full access to the application code. The input for SAST is not limited to code alone and includes other types of assets such as documentation, configuration files, and dependencies (libraries and frameworks).
To run, SAST refers to a set of predefined rules that scan your source code and mark the location of the issue detected. SAST can help identify issues like buffer overflows, exposed code secrets, input validation errors, insecure infrastructure configurations, and other lousy coding practices as part of a comprehensive application security strategy.
The main advantage of SAST scans is that security teams run them as part of secure CI/CD pipelines before code deployment. Ideally, teams perform them as soon as developers commit code to ensure they address security issues earlier in the software development lifecycle (SDLC). Additionally, teams can apply SAST scans to sections and parts of an application before comprehensive vulnerability scanning or penetration testing is possible.
DAST (Dynamic Application Security Testing) is a type of black-box testing (the scanning tool has no access to the application source code) that checks the application for vulnerabilities and weaknesses as it runs.
The DAST tool simulates attacks on the system and its environment. It analyzes the system’s responses and provides developers with invaluable insights into how their app behaves when facing real-world attack scenarios. Typically, security teams run DAST later in the SDLC, traditionally executing it in the CI/CD pipeline just before deployment to a testing environment.
DAST (and its main benefit) is to identify and flag runtime vulnerabilities that may not appear as weaknesses in the application code but can turn into potential exploits when the application runs. For example, DAST can help uncover XSS (cross-site scripting) and SQL injection weaknesses in your web apps, as well as server-side misconfigurations and authentication issues. DAST is particularly useful for applications that rely on internet protocols, as these are often the target of malicious actors.
| SAST | DAST | |
| Stage of implementation | Pre-runtime phases of the SDLC, ideally on every code commit | After the application is deployed to a testing environment and is actively running |
| Requirements | Static application source code and related assets | Fully deployed and executable application |
| Testing methodology | From the inside out | From the outside, mimicking an attacker |
| Types of weaknesses flagged | Known vulnerabilities (according to pre-set scanning rules and templates) | Vulnerabilities that result from the application’s interaction with users and its environment |
| Accuracy | Prone to false positives | Higher signal-to-noise ratio |
Development teams optimize SAST by using it early in the SDLC. Before code compilation for testing, the commit or pre-commit stage facilitates the early detection and resolution of security-related bugs and issues. Rapid feedback ensures the code remains fresh, allowing developers to address contextual vulnerabilities without needing documentation.
Development teams incorporate SAST into CI/CD pipelines and DevSecOps processes that prioritize automation to maximize productivity. SAST continuously monitors every piece of code entering the codebase for bad coding practices and automates testing for a range of vulnerabilities using external security industry data sources, such as the OWASP Top 10.
Another scenario where development teams require SAST is when dealing with compliance and regulatory requirements for data privacy in their applications. They can use SAST scanners with specific rulesets to test their application and its configuration against data protection regulations and laws, like the Health Insurance Portability and Accountability Act (HIPAA) and the Payment Card Industry Data Security Standard (PCI DSS). For example, SAST tools can be used to identify sensitive data within code and configurations, ensuring it is properly protected and handled in compliance with relevant regulations.
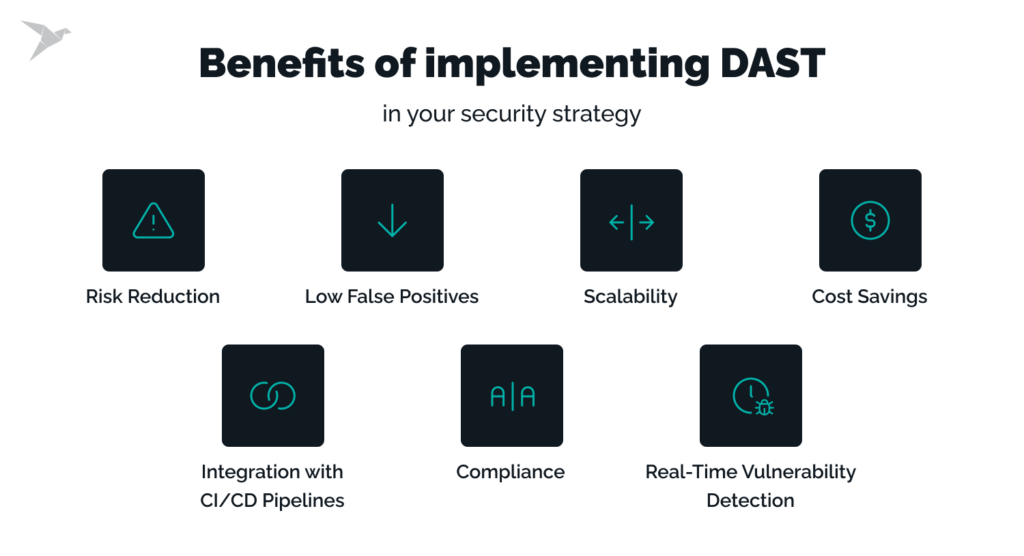
DAST shines when an executable application runs in a dynamic environment that responds to versatile input. Security teams leverage DAST to pinpoint misconfigurations in the application’s backend that affect functionality at runtime and vulnerabilities arising from integration issues. Furthermore, DAST helps test the application’s APIs and web services and assess the security posture of the infrastructure where it runs.
Since the tests require a fully working and executable application, it’s best to run your DAST scans after you deploy your application to a pre-production testing environment. When integrated as part of your CI/CD pipeline, DAST can be an always-on monitoring tool for application and infrastructure security in runtime, protecting your applications from XSS and SQL injection attacks.
SAST and DAST are not mutually exclusive but serve two different roles in your application security testing strategy at different stages of the SDLC. Using SAST and DAST in your DevSecOps pipeline provides a more comprehensive view of the application’s security posture. It significantly increases your security testing coverage by allowing the tools to complement each other and address one another’s limitations, ultimately reducing the risk of application fraud.
SAST critically identifies and remedies issues in the early stages of development by directly analyzing the source code. Conversely, once the application is running, security teams implement DAST later in the SDLC to uncover and address runtime vulnerabilities. These vulnerabilities, such as JavaScript injections, become apparent only when the application is actively running or under attack and may arise after deployment or under specific attack conditions.
Combining DAST, SAST, and other code scanning tools like Spectral as part of your DevSecOps pipeline provides comprehensive security testing throughout your SDLC, ensuring all your proverbial bases are covered.

The choice between SAST and DAST (or the integration of both depends) highly on the organization’s specific goals, needs, and constraints. Among the factors that may impact your tool selection are:
The general rule of thumb for developing and shipping secure software is to start with SAST scanning as soon as code is committed to a repository, with DAST incorporated later in the SDLC. Implementing security best practices for code repositories, like GitHub, can further enhance the effectiveness of both SAST and DAST.
That said, it’s important to remember that, even when combined, SAST and DAST don’t provide complete end-to-end protection against security breaches to your application. As your application security strategy evolves alongside your application, you must adopt the tools and technologies that will provide a broad net to catch any potential vulnerabilities in your software.
SAST and DAST are critical application security testing methodologies for any DevSecOps pipeline and any organization prioritizing application security. SAST ensures that your code doesn’t contain errors and weaknesses, while DAST checks your application’s deployed state for runtime vulnerabilities.
While both SAST and DAST contribute to your application’s security, complete protection requires both methods. However, many tools and services offer integrated solutions combining both. For example, Spectral’s developer-centric platform provides essential SAST scanning and DAST runtime protection, ensuring compliance with regulations and applying best practices early in the development lifecycle (“shift-left”). With Spectral, you can safeguard your organization and its software from IaC misconfiguration, code leaks, code tampering, and CI/CD vulnerabilities.
Start baking security into your SDLC with Spectral by Check Point today and start here with a free account.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions