Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
The trouble with allowing developers to deploy code directly to production is that security threats are often overlooked in the process. These vulnerabilities only show up later during runtime. Once this happens, it falls on the shoulders of the Ops team or SREs to engage in firefighting.
What every developer & Ops team needs is a tool that helps them find secrets in code, misconfigurations, and other threats at build time, something that gives them a quick overview of what security threats are going to present themselves later. Application Security Testing (AST) is just that: a solution that helps to protect the build from security threats.
There are three types of ASTs: SAST, DAST, and IAST. Static Application Testing tools (SAST) and Dynamic Application Testing tools (DAST) are the older generation of application testing tools, while IAST is the newer version filling in the gap left by the previous versions.
Static Application Security Testing scans and analyzes code during non-runtime. SAST is easy to deploy and looks for patterns in the code that would predict a security risk at the time of deployment. Though helpful, there are flaws in the SAST process. SAST can only run to detect and analyze at the early stage of development before runtime.
Scaling SAST is a challenge for newer distributed applications that work on a large scale. It also creates false positives and false negatives because it does not accurately model code behavior.
Dynamic application security testing is a slower testing method that focuses on testing security from the outside by penetration testing. It is a black-box testing tool that scans during the application’s runtime. It looks at the exterior to find security flaws through penetration testing and doesn’t use or require the source or binary codes.
DAST takes a long time to provide results–a usual estimate takes about five to seven days. Also, it can’t be automated as this method requires experienced AppSec team members to run it. The tool user needs to know and understand the penetration testing process. Since DAST doesn’t have information about the internal code, it doesn’t help to pinpoint the cause of the problem.
Interactive Application Security Testing was made to build on and solve the gaps in both SAST and DAST. IAST was made to scan and analyze threats in code while automated testing or manual testing (or both) are running. It provides real-time analysis of the threats in the build and helps the developer fix these issues while it scans the source code. This gives the developer an excellent vantage point for the build, and the real-time response adds to the speed at which a developer can make changes in their code before the application is released.
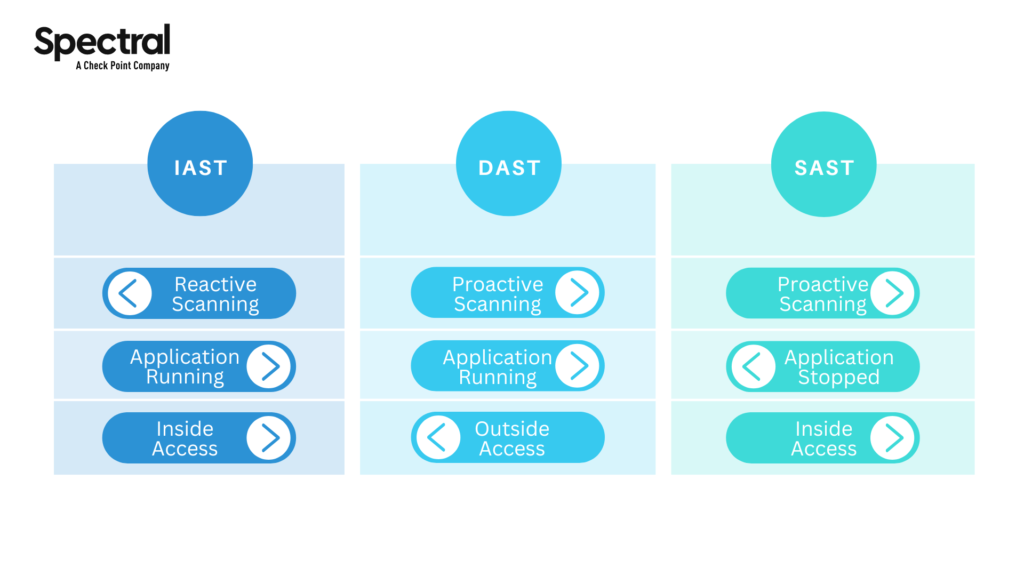
Now we know that IAST is the best of the three testing methods as it doesn’t suffer from the drawbacks the previous approaches had. But how does IAST work, what are some of its other key benefits, and which IAST tools are the best?
Companies are slowly adopting IAST tools, but many developers are still unaware if their company uses them. If you are familiar with IAST, this list may ring a bell if your organization already uses one of them. Alternatively, you can take steps to introduce these in your organization to reap the benefits of IAST.
Invicti builds automated testing tools that help large organizations to secure their applications and website from threats and attacks. They use DAST and IAST scanning methodologies to help automate web security in complicated environments with ease and confidence.
Pros: Invicti provides low to zero false positives and a straightforward configuration to secure many websites and web applications.
Cons: Lacks support for 2FA and MFA web applications
Contrast Security embeds security analysis and prevention of attack into the software with instrumentation. It automatically detects the vulnerability while developers write code and eliminate false positives. It helps developers and the Ops team to collaborate more closely.
Pros: Reduces noise and increases the focus on vulnerabilities. It gives the DevOps team a better view as there are fewer interruptions.
Cons: There have been some problems with .NET and Azure, with fewer robust features available for them.
A tool developed by developers for developers, SpectralOps monitors code while it’s being written and after it is deployed. Although not exclusively an IAST tool, it monitors and detects security misconfigurations and other threats in real time, giving developers a robust 360-degree view of the application so they can code with confidence and enhance security.
Pros: It is easy to set up and helps excavate old and new threats that may not have been discovered otherwise.
Cons: Some reports and metrics can be hard to generate and get to, but they are being worked on and constantly improved.
With a focus on SAST and some add-on features, Checkmarx aims to cover every stage of the software development lifecycle. It is specially developed for DevOps teams to improve their QA testing and CI/CD. It fits directly into your QA system and helps improve existing tests.
Pros: Checkmarx provides a good flow of code from source to deployment with great integration for CI/CD.
Cons: The count of false positives is more than its competitors.
Jit is an open source security orchestration platform. Jit orchestrates several open source solutions into a single user interface to protect the entire SDLP lifecycle. One of the open source solutions Jit orchestrates is Bandit, a SAST solution for Python applications. Jit integrates Bandit into the CI/CD and automatically runs it with every new PR.
It is time for organizations to focus on securing their applications right from build time. Concentrating on the threats and vulnerabilities that tend to escape developers’ view is important given that threats don’t just affect devices but also applications. It’s possible to protect every layer of an application from an attacks, as we have seen, using a good IAST tool. With this in mind, if you don’t have one yet, picking the right IAST tool to secure your application should be on your to-do list.
In the meantime, learn how to stay on top of security loopholes with in-depth visibility that traditional security solutions fail to cover.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Continuous integration and delivery are necessary in any production level software development process. CI/CD are more than just buzzwords. Rather, it is a fully-fledged methodology of