Circle.ci vs Jenkins: Battle of the CI/CDs
Continuous integration and delivery are necessary in any production level software development process. CI/CD are more than just buzzwords. Rather, it is a fully-fledged methodology of
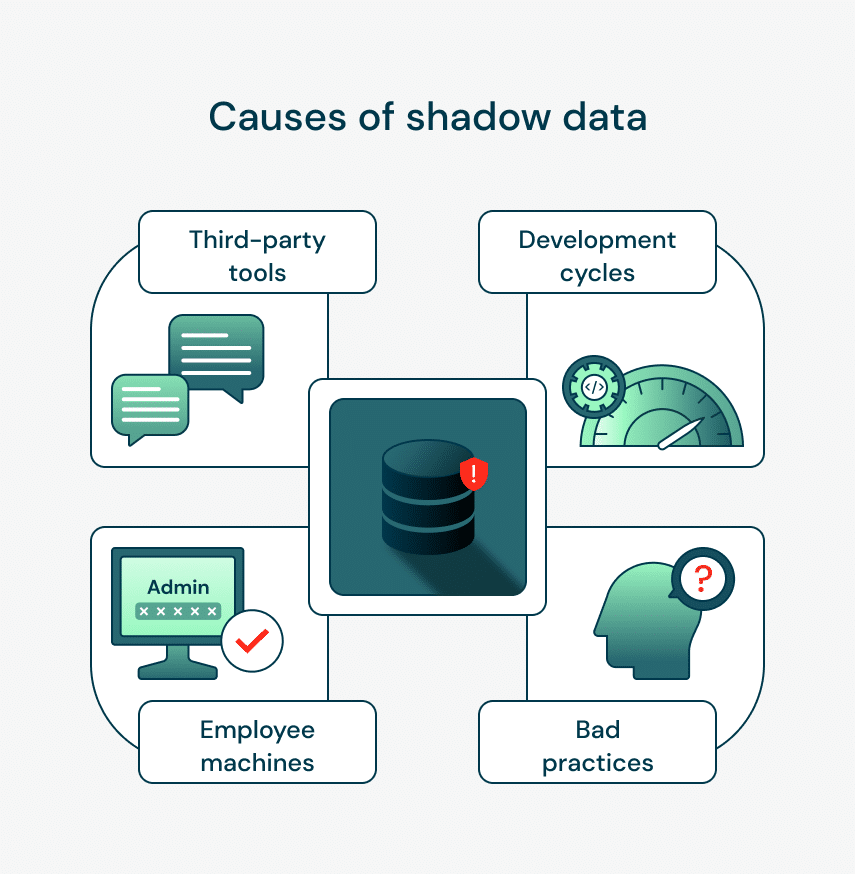
Sensitive data, like customer information and internal processes, often lurks hidden in employee devices or in unmanaged spreadsheets. This “shadow data” poses a security risk because it’s difficult for IT teams to monitor and protect. Without visibility into this hidden data, organizations can’t effectively enforce security policies, putting them at risk of data breaches.
Mishandling sensitive data can have severe consequences. For example, a data breach exposed the information of 18,000 Nissan customers, highlighting the dangers of unsecured data. This type of incident can lead to hefty fines, damage a company’s reputation, and even lead to legal trouble.
However, data discovery tools offer a solution. These tools scan extensively to uncover hidden data. This visibility allows DevSecOps to secure every piece of data throughout the organization, improving compliance and overall security.

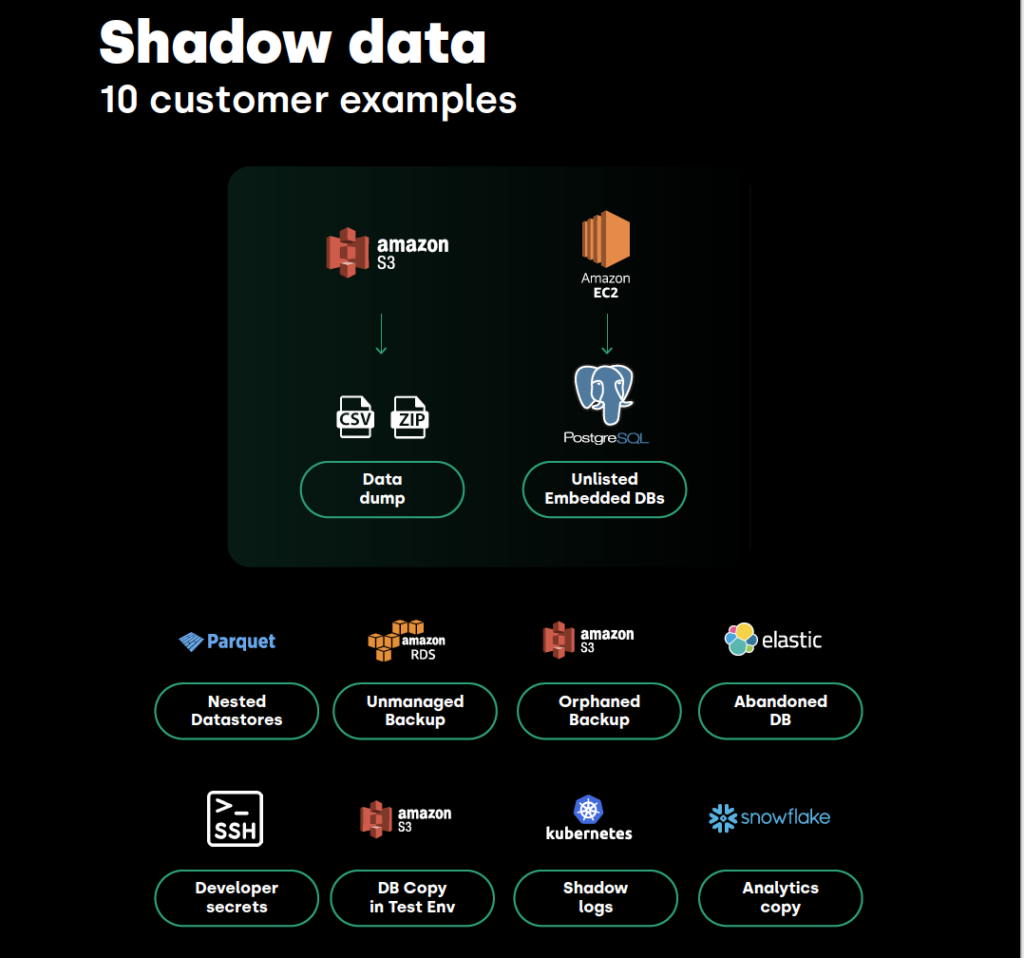
Hidden data poses risks far beyond unnoticed PII on personal devices. Internal configurations, intellectual property, strategic plans, and other sensitive corporate information are as vulnerable. Mishandling of sensitive data can lead to severe consequences, including hefty fines, reputational damage, and potential legal action
This overlooked data is a ticking time bomb, threatening more than just privacy:
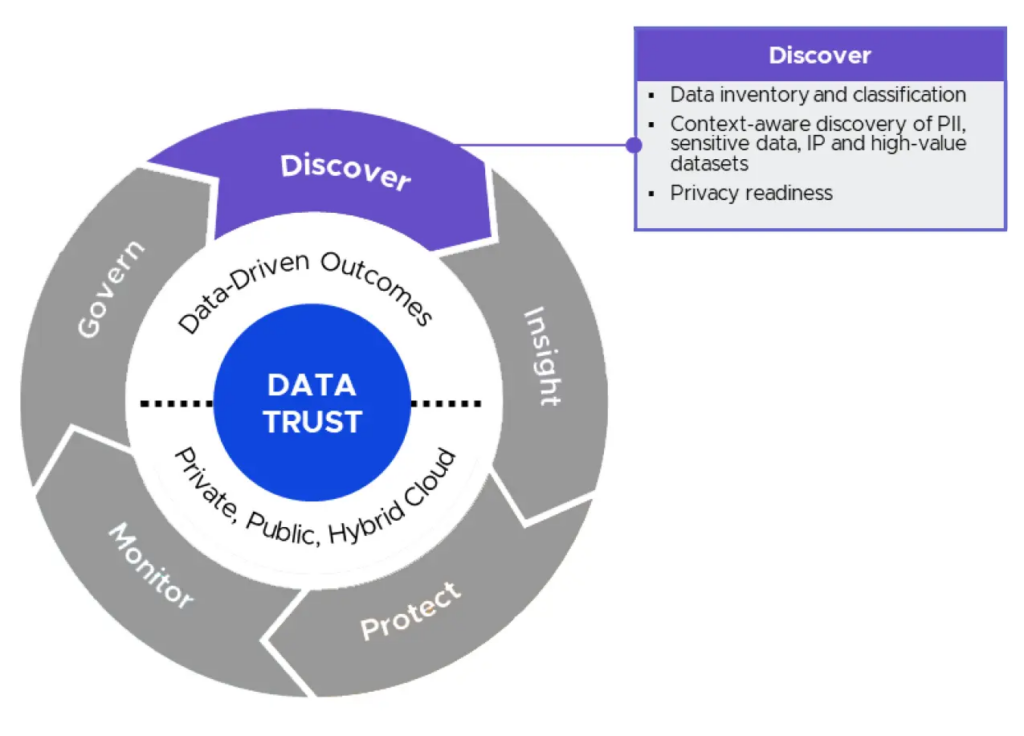
Data discovery is all about getting to know your data better by indexing, profiling, and categorizing data across various sources to create a structured map of all your data assets. It reveals exactly what you have and where it’s stored and organized.
The perks of data discovery are immense.
Data discovery tools help uncover hidden datasets, which could lead to the development of new features, optimization of existing processes, or even the discovery of new revenue streams. Data discovery tools are indispensable for proactive compliance, helping identify and manage personally identifiable information (PII) as required under GDPR, CCPA, and other data protection regulations.
Selecting the right data discovery tool is an investment that goes beyond just finding data. Here’s what you need to consider to make an informed decision:
Kicking off data discovery is strategically mapping out where and how to look for hidden data. You want to ensure your efforts align with your organization’s priorities and security needs.
First, get your data discovery tool to talk about where your data lives.
Data could reside within databases, be stored in cloud solutions, or be distributed among various SaaS platforms. The crucial factor is selecting a tool with extensive compatibility and integration capabilities, which will facilitate a thorough and frictionless discovery process.
With your connections ready, it’s time to get selective. Understand that not all data holds the same value or risk, so focus on the juicy bits: sensitive customer information, data regulators monitor, and anything directly impacting your business goals.
This step is about filtering the noise to spotlight the data that’s either a potential risk or a potential win.
Now, onto the nuts and bolts—configuring your scans. Decide on the frequency and depth of your scans. Deep scans are more time-consuming but essential for sensitive or critical data areas. A lighter scan might be adequate for general oversight.
Decide if you’ll lean more on scheduled scans, which run automatically at set intervals, or on-demand scans, which you can launch manually in response to specific concerns or events.
Consider a scenario where an analyst is preparing for an upcoming audit focusing on personally identifiable information (PII). Aware of the impracticality of manual searches across their extensive data repositories, they turn to their data discovery tool for assistance. Here’s how that process might go down:
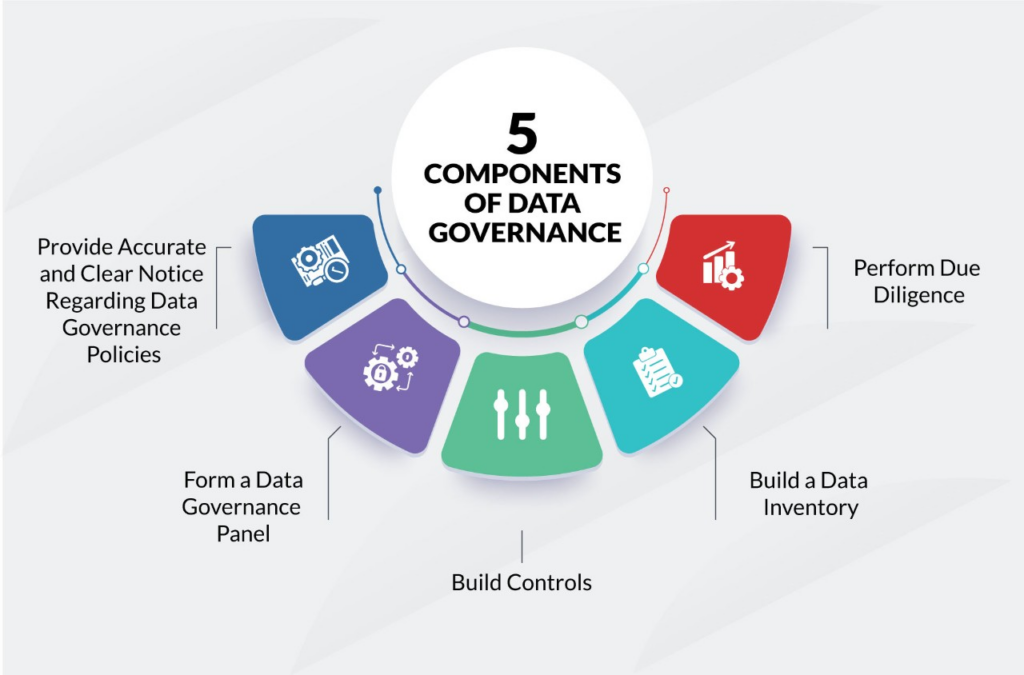
A well-executed data discovery and governance strategy maximizes the value of your organization’s data assets. It’s more than just finding and organizing your data—it’s also about integrating that discovered data into your systems for deep analysis and smart, strategic use.
Feeding discovered data into data catalogs is critical in stitching together solid data governance. This process takes the raw, discovered data and organizes it into a detailed, easily navigable inventory. These catalogs become a vital tool in crafting clear data access policies, laying out who gets to see and use what data, and ensuring it’s done safely and in compliance with regulations.
It’s about smoothing data management and building trust and security around your data assets. It will allow for more intelligent, more controlled data usage throughout the organization.
Structured data revealed through the discovery process forms the bedrock for improved reporting and analytics. By integrating this structured data into business intelligence (BI) dashboards, your organization gains granular insights into operational metrics and customer behavior.
Pinpointing sensitive and high-risk data is the beginning of a truly effective security strategy. Once you’ve identified this critical information, it’s time to dive deeper. Left unchecked, secrets sprawl (like misconfigured API keys or exposed credentials) poses a significant risk and increases the attack surface.
Implement continuous data monitoring alongside user training to receive real-time alerts on anomalies, suspicious activity, or unauthorized third-party access attempts.
Adopting solid data discovery practices boosts your security and how your teams work together. Let’s explore practical strategies to make your data discovery work harder and smarter, aligning with DevSecOps principles.
Getting the most out of your tools means ensuring everyone who needs them knows how to use them. It includes bringing all relevant team members up to speed, from developers to security folks and operations staff.
This training should cover the basics of tool operation, advanced features, best practices for data analysis and threat detection, and the importance of integrating with security orchestration platforms to streamline incident response.
Your data is constantly changing and growing in size and complexity. That means your approach to data discovery must change with it.
Revisit and regularly update your data discovery configurations and goals to maintain relevance and effectiveness against new data patterns and emerging threats. Adjust your data classification schemas and access controls as your data evolves to guarantee accurate detection and safeguard critical information.
In the fast-moving DevSecOps world, the cost of reactivity can be devastating. Data discovery is the proactive advantage you need. It reduces code vulnerabilities, smoothing compliance, and speeds up your response to incidents.
As you consider data discovery tools, prioritize those that align with your unique requirements. Whether your focus is on comprehensive scanning capabilities, integration ease, or specific compliance needs, the right tool does more than just the job – it sets you up for solid data governance and strengthens your security.
Ready to take control of your data and enhance your security posture? Discover hidden data, streamline compliance, and proactively defend against threats. Get started today with a free SpectralOps account and see the difference firsthand.

Continuous integration and delivery are necessary in any production level software development process. CI/CD are more than just buzzwords. Rather, it is a fully-fledged methodology of

Jenkins is the most used open-source CI/CD solution out there. Being a FOSS project usually means that there’s an ever-growing number of extensions and capabilities for
Code fast and break things may be a healthy approach when you’re rushing to present investors with a POC. However, when it comes to developing real-world