10 Types of Vendor Related Risk Cloud Native Organizations Need to Manage
If you are a developer in the current cybersecurity climate, you already know your application’s security is paramount. But have you considered the risks associated with
No one wants to send their precious information over unencrypted channels. This is why most websites and web services use HTTPS to encrypt data by default.
When it comes to connecting to GitLab, many users and developers default to using HTTPS. Why? Because everyone knows how a username and password work. Albeit maybe not on a technical level but intuitively it makes sense.

Things tend to get a little more complicated when sending Git commands to a server over HTTPS demands the user submit their username and password in order to perform each action. This can result in quite a lot of prompts. Moreover, when using CI/CD and automation tools, SSH keys are a much better choice for securely authenticating your GitLab account.
In this article, we’ll review what SSH keys are in the context of GitLab authentication, how to create them, and how to keep them safe.
In order to communicate over SSH (Secure Shell), you must have an SSH key pair. Each SSH key pair has a public and a private key.
Public Key – Can be used to encrypt data in such a way so only the holder of the corresponding private key can decrypt it.
Private Key – Can be used as proof of identity, and is used to authenticate a user’s connection to the server.
When using an SSH key pair as a method of authentication, the public key is stored on the server. It doesn’t really matter if it can be viewed as it is public information. The private key, however, is kept by the user and should not be copied or exposed in any way.
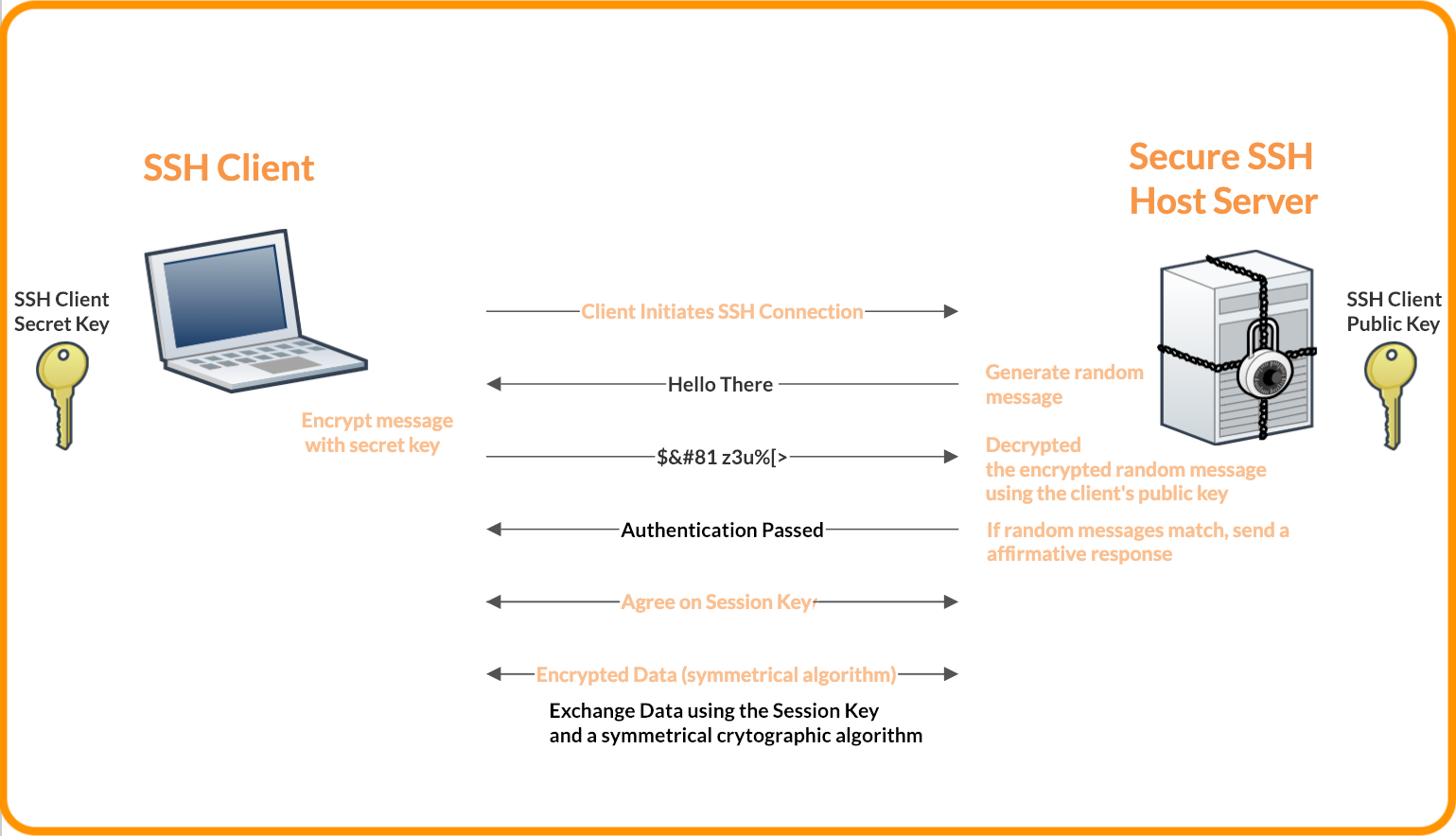
Once this is set up, the server can ask the user for proof of identity using the public key and the user can prove it using the private key.
SSH keys are one of the choices for authentication against GitLab servers. The vast majority of actions you will be taking on GitLab via SSH will be pushing changes from your local git repository to the hosted repository on GitLab.
Although there are other actions you can take, such as starting the GitLab CI/CD pipeline, once started you’re not going to need to interact with the GitLab runner often. Whenever you push code to the hosted repository, it will trigger the pipeline and it will be automated from there, and that action might be scheduled to run many times a day.
It is generally recommended you use ED25519 SSH keys, which are more secure, and should be available on any system.
However, if you have a good reason to, there are also RSA SSH keys, which would work just as well on GitLab. Although it is recommended you use an SSH key of at least 2048 bits. Do note that by default, a 1024 bit key is generated, so make sure to not use the default.
Aside from the comfort provided by not having to submit your username and password for each action you take, SSH keys are generally much more secure than a username and password. Humans aren’t very good at remembering a large number of secure passwords so they tend to reuse passwords over multiple sites, resulting in many vulnerabilities. No system connected to the internet is truly secure, but with an SSH key you greatly reduce the chance of human error giving away your access privileges.
The official documentation is fairly comprehensive, but for completeness sake, I will walk you through the process.
One thing you won’t find in the above page, since it shows up in another place in the documentation, is where to type in the commands.
I’m assuming you are using GitBash, as it is the terminal that is supplied with git. For MacOS, Windows PowerShell or Linux terminals instructions, please see the documentation.
To generate ED25519 SSH key you will need to run the following terminal command:
ssh-keygen -t ed25519 -C "<comment>"
The -C and the comment in quotations is optional, but should be used if you’re going to generate more than one pair.
You should see the following response after typing the above command:
Generating public/private ed25519 key pair. Enter file in which to save the key (/home/user/.ssh/id_ed25519):
If you wish to generate an RSA key pair, use the following command:
ssh-keygen -t rsa -b 2048 -C "email@example.com"
Note the -b 2048, which denotes the number of bits for the key. If you choose to use RSA, the US National Institute of Science and Technology recommends 2048.
The output should look like this:
Generating public/private rsa key pair. Enter file in which to save the key (/home/user/.ssh/id_rsa):
Unless you know you need to use a different one, use the default path. But whatever you choose, do not use a network path (more on security later). Your chosen terminal will also use the generated SSH key without further input.
After generating the pair, you will be prompted to optionally add a passphrase:
Enter passphrase (empty for no passphrase): Enter same passphrase again:
This is optional, but recommended if others may have access to your computer where the key is stored.
The first thing you’ll need is your public ED25519 SSH key in text form, to get this, you can use this command it Git Bash:
cat ~/.ssh/id_ed25519.pub | clip
Or if you’re using RSA:
cat ~/.ssh/id_rsa.pub | clip
Which will copy the SSH key in text form to your clipboard.
While logged into your GitLab account on gitlab.com, follow these steps:
SSH keys are far less prone to human error, but they are not foolproof. If you’re going to use SSH keys you should have a general idea about the security risks and how to mitigate them. Why? Because not doing so may cost you. In 2019 GoDaddy, one of the largest domain registrars in the world, suffered a critical security breach due to mismanaged SSH keys.
There are many things you could do in order to make your SSH communications more secure, but most of them are done from the server side, not the client side. As an admin, you may want to set up expiration policies, so that new keys need to be generated, and old keys will no longer be valid. This greatly reduces the risk of the keys falling into the wrong hands.
As a user on GitLab though, the main thing you need to concern yourself with is that the private key generated and stored locally should never ever be copied or moved. If you feel your private key may have been compromised, remove the corresponding public key from the server. You might want to do this periodically regardless, to ensure your server’s safety.
If you ever find yourself on a different computer, simply generate a new SSH key pair and upload the public key to GitLab. If a computer is lost, simply delete the public key from your GitLab account and all is well.
Do not backup your SSH keys as the only thing that does is create a vulnerability. As a rule, creating new keys and revoking old ones is a lot less painful than dealing with the fallout of a leaked SSH key pair.

If you are a developer in the current cybersecurity climate, you already know your application’s security is paramount. But have you considered the risks associated with

The trouble with allowing developers to deploy code directly to production is that security threats are often overlooked in the process. These vulnerabilities only show up

Rapid digitalization and increasing remote business operations place a significant burden on developers, who are continuously pressured to push out software faster. As a result, CI/CD