Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Your organization’s data and applications are scattered across multiple cloud platforms and on-premise systems. How do you guarantee security in this sprawling digital landscape?
Cloud sprawl is a reality — 76% of organizations grapple with this challenge when they turn to multi-cloud strategies. The rapid adoption also creates complexity and cracks in traditional perimeter-based security. Your attack surface multiplies with users, devices, and data scattered across environments.
This is where Zero Trust Architecture (ZTA) provides a new security framework to help you confidently navigate the complexities of modern cloud architectures.
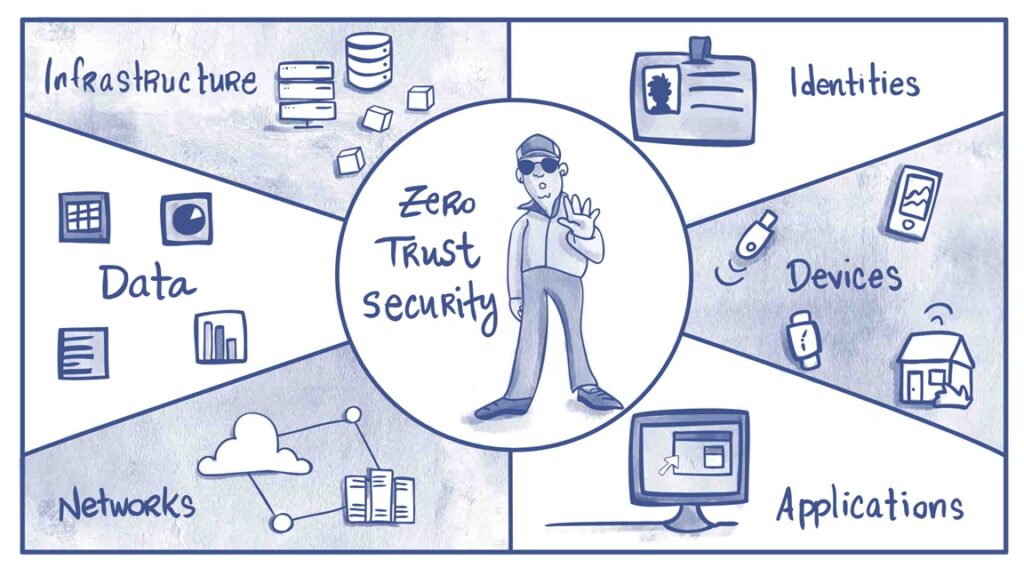
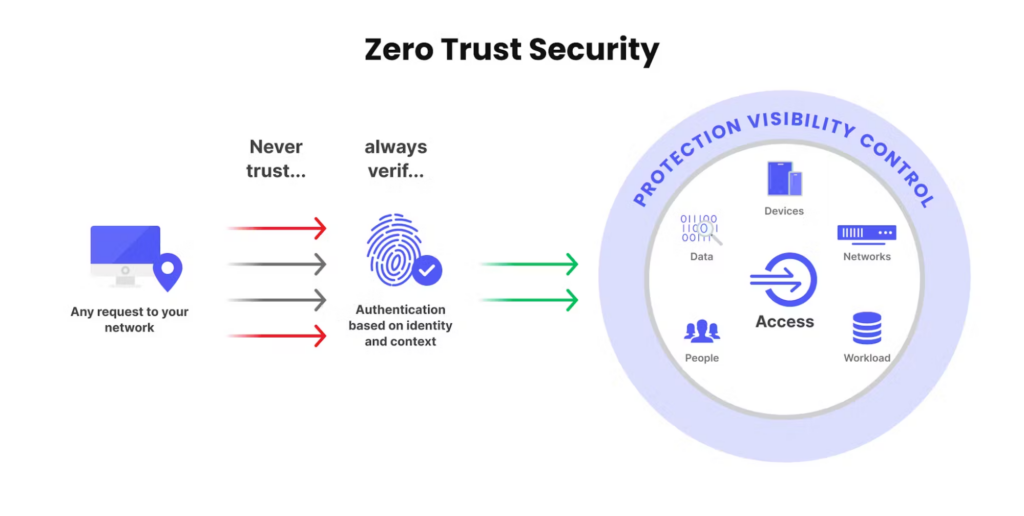
At its heart, Zero-Trust Architecture (ZTA) changes our minds on security. It’s based on the principle of “never trust, always verify.” This means that no one—whether a user, device, or piece of data—is automatically trusted, regardless of whether they’re inside your network. Instead, Zero-Trust Architecture constantly checks for legitimacy before granting access.
Traditional security models focused on creating a solid perimeter. Everything inside the wall was considered safe. But in the age of cloud computing, data and applications are everywhere. Zero-Trust Architecture recognizes that no single “inside” exists and protects your resources with advanced security controls.
Critical components of a Zero Trust Architecture include:
While the foundational principles of Zero-Trust Architecture are clear, understanding its practical advantages is crucial for organizations considering its adoption.
Here are the 9 benefits of Zero Trust Architecture and what it can deliver.
Zero-trust architecture significantly reduces adversaries’ potential attack surface by replacing implicit trust based on network location with granular access controls at every step. This proactive approach is reinforced through micro-segmentation, which logically isolates and secures individual workloads, applications, and resources within an environment.
Micro-segmentation enforces the principle of least privilege, preventing unchecked lateral movement within a breached environment. If an attacker manages to compromise a single component, their ability to pivot and traverse the network is severely limited. Instead of enjoying unfettered access, they are confined to a tightly controlled segment, drastically reducing the potential for widespread damage or data exfiltration.
Zero Trust Architecture’s comprehensive visibility empowers organizations to proactively identify and mitigate risks before threat actors can exploit them. This context-rich information makes it possible to implement granular permission controls, minimizing the potential impact of data breaches
However, even in a Zero Trust environment, blind spots can persist. Codebases can contain hardcoded secrets, misconfigurations, and vulnerable dependencies that standard Zero Trust access controls might miss. To ensure all-around security, organizations need the ability to continuously scan code, infrastructure, and assets for these hidden vulnerabilities.
While implementing the principle of least privilege can be challenging, the long-term benefits of data protection are invaluable.
Zero Trust Architecture significantly reduces the potential blast radius of accidental data leaks and malicious breaches by strictly limiting access rights. If a user account or system is compromised, the attacker’s ability to access and exfiltrate sensitive data is confined to a much smaller scope. A Zero Trust model’s continuous monitoring and adaptive response capabilities enable prompt detection and mitigation of potential data breaches.
The principles of Zero Trust Architecture align with the requirements of various regulatory standards, including those focused on healthcare data. Understanding the importance of these requirements is crucial, as failure to comply with security standards can destroy the trust of developers and users alike.
Many critical components of a Zero Trust Architecture map directly to specific regulatory clauses, streamlining compliance efforts. For instance, the comprehensive logging and continuous monitoring capabilities inherent to Zero Trust Architecture satisfy the audit trail and breach notification requirements outlined in GDPR’s Articles 30 and 33.
Adopting a Zero Trust Architecture (ZTA) can significantly simplify the audit process required for GDPR compliance for organizations operating within the European Union’s territory. The inherent security controls, data protection measures, and comprehensive visibility provided by Zero Trust Architecture are valuable evidence of an organization’s commitment to safeguarding personal data, potentially reducing the burden of regulatory audits.
For organizations looking to embrace hybrid infrastructure models that span cloud, on-premises, and remote devices, the limitations of traditional perimeter-based security have become increasingly apparent. Zero Trust Architecture addresses these challenges head-on by decoupling security policies from physical network locations, providing consistent protection for assets regardless of their environment.
This adaptability empowers organizations to securely leverage the benefits of hybrid infrastructures without compromising their security posture.
The surge in remote work arrangements has introduced new security challenges as employees access corporate resources outside the traditional office perimeter from various locations and devices. Zero-trust architecture eliminates the implicit trust associated with on-premises presence, ensuring that remote access is subject to the same stringent security measures as on-site connections.
With Zero-Trust Architecture, remote endpoints are treated with the same level of scrutiny as any other asset, mitigating their heightened risks. Continuous verification and adaptive access controls are applied regardless of the user’s location or device. This proactive approach safeguards against threats such as compromised home networks, unsecured personal devices, or man-in-the-middle attacks targeting remote connections.
Organizations typically rely on third-party vendors, partners, and suppliers, which can introduce significant security risks. The traditional approach has been to implicitly trust these external entities to deliver secure software, services, or components. However, high-profile incidents like the SolarWinds breach have highlighted the devastating consequences of supply chain compromises.
Zero Trust Architecture extends security controls beyond an organization’s boundaries, enforcing stringent authentication and authorization protocols for all third-party interactions. Rather than granting blanket trust, ZTA scrutinizes external entities as closely as internal resources, minimizing the potential impact of a supply chain compromise.
A well-designed Zero Trust Architecture, leveraging single sign-on (SSO) and context-aware access policies, can significantly reduce friction for authorized users. By eliminating the need for multiple authentication prompts and granting access based on continuously verified identities and contexts, ZTA can enhance the overall user experience.
While potential UX pitfalls exist, such as developers or users unfamiliar with multiple layers of authentication finding the process cumbersome, these challenges are avoidable with thoughtful implementation. Organizations can balance robust security measures and a streamlined user experience by carefully considering user workflows and incorporating intelligent policy orchestration.
Zero-Trust Architecture’s constant monitoring establishes a comprehensive baseline of ‘normal’ activity, making it easier to identify anomalies. This empowers organizations to develop a robust cyber threat intelligence framework. Continuous learning allows Zero-Trust Architecture to detect unusual access attempts, data exfiltration attempts, and deviations from established patterns.
For example, if a log aggregation service, typically accessing internal logs within a specific network segment, suddenly starts making outbound network calls directly to the organization’s database, established security protocols within a Zero-Trust environment would not only cause these unauthorized calls to fail but also trigger a series of automated responses.
To strengthen these capabilities further, consider solutions that actively monitor public assets for exposed credentials, secrets in code, and other critical blind spots that can jeopardize security. This adds an extra layer of protection beyond the core ZTA framework.
Adopting a Zero-Trust Architecture (ZTA) is a journey, not an overnight switch. Organizations should approach it through a phased implementation, starting with their most critical assets and expanding from there. Secure identity and access management (IAM) are the foundation for ZTA, ensuring that identities are appropriately vetted, authenticated, and continuously verified throughout the access lifecycle.
Equally important is the cultural shift that accompanies a zero-trust transformation. Successful implementation requires buy-in and commitment from stakeholders across the organization, as traditional notions of implicit trust are replaced by a “never trust, always verify” mindset.
In the modern cloud landscape, where threats lurk in seemingly every corner, building trust is a commitment to always verify the source. Zero Trust Architecture (ZTA) embodies this principle.
Even the most robust Zero Trust implementation can leave blind spots. Hardcoded secrets in code, misconfigurations, vulnerable dependencies, and exposed assets on public repositories pose critical risks that traditional access controls might overlook. Organizations must proactively address these vulnerabilities to achieve truly comprehensive security.
Spectral can seamlessly integrate with Zero Trust frameworks, empowering you to scan your code, infrastructure, and public assets for these hidden risks. Ensure that your security posture remains uncompromised with a free account today.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions