Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Modern cybercriminals aren’t just after your average employee. They’re targeting DevOps engineers – the gatekeepers of critical infrastructure and valuable data.
90% of data breaches start with phishing. Traditional awareness training often needs more technical depth. These programs tend to focus on generic red flags (e.g., suspicious links and requests for sensitive information) that are easily recognized by most.
This guide introduces technical phishing awareness training methods that empower DevOps engineers to become the first line of defense against this persistent threat.
Phishing is a cyber attack that leverages social engineering to manipulate victims into divulging sensitive information or performing actions that compromise security. While seemingly simple, phishing has evolved into a multifaceted threat, employing various vectors like email (phishing), targeted emails (spear phishing), SMS messages (smishing), phone calls (vishing), and social media interactions (angler phishing).
The success of phishing attacks hinges on the exploitation of human psychology. Cybercriminals craft deceptive messages that trigger emotional responses (urgency, fear, curiosity), leading victims to bypass rational judgment and inadvertently expose vulnerabilities. This human factor often renders even the most robust technical defenses ineffective. A click on a malicious link or a moment of trust in a seemingly legitimate request can open the floodgates to devastating consequences, including compromised sensitive data, customer records, financial information, and intellectual property.
Phishing awareness training is not merely about recognizing suspicious emails – it’s about understanding the technical underpinnings of these attacks. It is essential when considering privileged access management.
We need to move beyond generic warnings. By understanding the technical vulnerabilities that attackers exploit, DevOps engineers can transform from potential targets into proactive defenders.
Let’s delve into these specialized training approaches, designed to equip DevOps engineers with the tools to dissect and dismantle phishing attack.
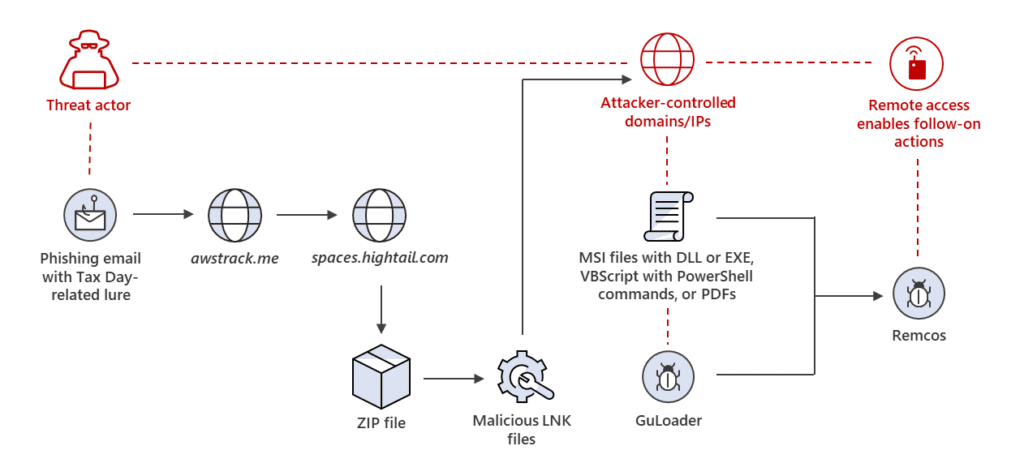
Traditional phishing simulations focus on the click, but for DevOps engineers, the real learning lies in the technical anatomy of the attack. By providing detailed feedback on the phishing email’s structure – including header analysis, identification of spoofed domains, and examination of embedded code – we can cultivate an understanding of how these threats operate, which ultimately enhances an organization’s information security controls.
Moreover, you can tailor these simulations to exploit specific technical vulnerabilities within your organization’s infrastructure. For instance, if a software weakness is known, you can craft a simulated phishing email that mimics an attack targeting that vulnerability. It provides DevOps engineers with a safe, controlled environment to practice identifying and mitigating real-world threats before they occur. By analyzing the technical artifacts of the attack, engineers develop a stronger intuition for spotting anomalies and malicious intent in future phishing attempts.
DevOps engineers uniquely leverage email headers as a powerful tool against phishing attacks. These workshops will empower them to decode the hidden information within email headers, revealing crucial details about the message’s origin and authenticity. Additionally, incorporating elements of DevOps automation into the email analysis process can significantly enhance efficiency and scalability.
Key topics should include:
Through hands-on exercises analyzing legitimate and phishing emails, DevOps engineers will develop the skills to spot forged headers, unauthorized senders, and other telltale signs of malicious intent. By understanding the technical nuances of email authentication, they become active participants in the fight against phishing.
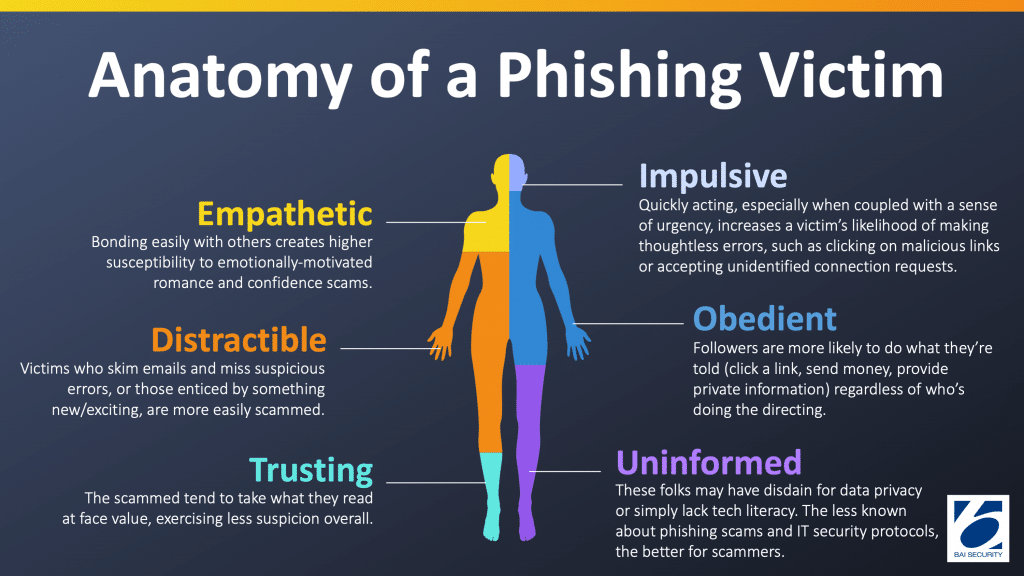
Phishing attacks are not just about technical trickery but about manipulating human behavior. This training module delves into the psychology of social engineering, equipping DevOps engineers with the knowledge to recognize and counteract the tactics that prey on cognitive biases. Understanding these psychological tactics is crucial in developing effective security orchestration strategies, as it allows for a more comprehensive approach to threat detection and response.
It should include:
By understanding the psychological underpinnings of social engineering, DevOps engineers can develop a heightened awareness of the subtle manipulation techniques used in phishing attacks. It empowers them to make informed decisions, resist deceptive tactics, and ultimately strengthen the security posture of the entire organization.
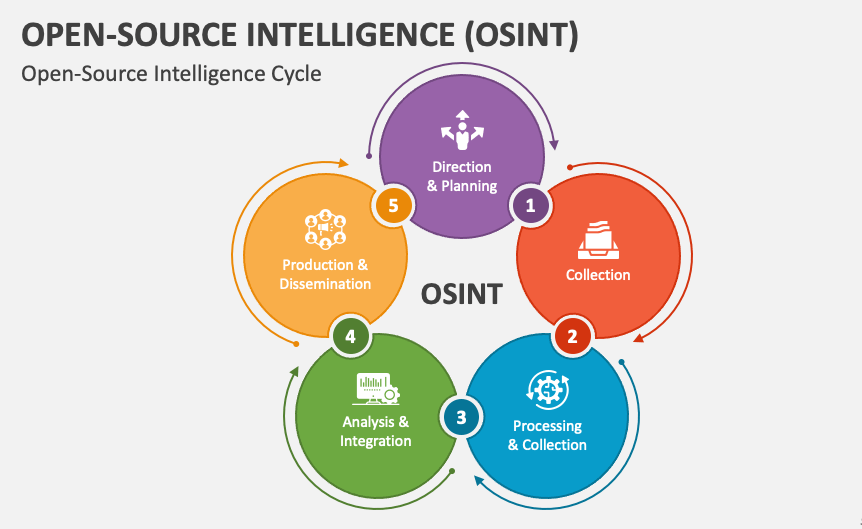
DevOps engineers, already adept at navigating complex technical landscapes, can leverage Open-Source Intelligence (OSINT) to identify and neutralize phishing threats proactively. OSINT involves collecting and analyzing publicly available information to gain valuable insights into potential attacks. By monitoring underground forums, paste sites, and social media channels, engineers can uncover leaked credentials, phishing kits, or domains used in active campaigns.
Specialized OSINT tools and techniques enable engineers to search for indicators of compromise (IOCs), such as specific email addresses, URLs, or file hashes associated with known phishing attacks. Adhering to industry standards such as PCI DSS compliance levels can further enhance the identification and remediation of these vulnerabilities, ensuring that sensitive data remains protected. Engineers can also leverage threat intelligence platforms that aggregate and analyze OSINT data, providing actionable insights on emerging threats.
Phishing emails often serve as the initial delivery vector for malicious software (malware). DevOps engineers can better assess the risks associated with suspicious attachments and links.
This training delves into the technical aspects of malware analysis, starting with an overview of common file types used in phishing attacks, such as executables (.exe), scripts (.js, .vbs), and document macros (.docm).
For example, Magecart, a group of hackers who target e-commerce platforms to steal customer information, often delivers malware through phishing emails. Knowledge of such groups can help the DevOps team mitigate against their malicious attempts.
Hands-on exercises will involve using sandboxing environments (virtual machines or cloud-based sandboxes) to safely detonate and analyze suspicious files, observing their behavior and network activity without risking infection of production systems. Participants will learn to identify common malware behaviors, such as persistence mechanisms, data exfiltration, and command-and-control communications.
Responding to a phishing incident requires more than just theoretical knowledge – it demands practical experience and swift, decisive action. Incident response simulations bridge the gap between theory and practice, providing DevOps engineers with experience managing a simulated phishing attack.
The practical approach aligns with Policy as Code (PaC) principles, where security measures and incident response protocols are codified and automated, enabling faster and more consistent responses to threats. By integrating PaC into incident response simulations, DevOps engineers can gain valuable experience in reacting to attacks and proactively defining and enforcing security policies throughout the software development lifecycle (SDLC).
These simulations go beyond the basics, immersing participants in scenarios where they must:
Key metrics such as click rates (the percentage of employees who click on phishing links) and reporting rates (the percentage who report suspicious emails) provide a quantitative measure of training effectiveness. By tracking these metrics over time, organizations can identify trends, measure progress, and pinpoint areas where additional training or reinforcement is needed.
Dynamic risk assessment is a continuous process of identifying, assessing, and mitigating cyber security risks. It is an essential component of any cyber security program and can help organizations protect their assets, data, and reputation.
Furthermore, a detailed analysis of phishing email content, attack vectors, and employee responses can reveal specific vulnerabilities and knowledge gaps. This information can be used to tailor future training modules, addressing specific topics or techniques that are challenging for employees.
Effective phishing awareness training for DevOps engineers requires a departure from generic approaches and a shift toward specialized methods that target their technical skills and responsibilities. Understanding the intricacies of phishing attacks is paramount for these high-value targets, which protect critical infrastructure and data.
In phishing awareness training for DevOps, Spectral tackles common pain points head-on. From public blind spots to secrets leakage, strengthen your defenses with practical guidance and protect against data breaches. Try Spectral today.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions