Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
As organizations push the boundaries of innovation, the need to embed security into every layer of the development process has never been more pressing. DevSecOps—a practice that integrates security directly into the DevOps pipeline—has emerged as a critical approach to staying ahead of potential threats. Yet, the challenge is knowing how to weave security seamlessly into these complex, fast-moving environments.
By the end of this year, the predicted global cost of cybercrime will reach $9.5 trillion, with projections suggesting it will rise to $10.5 trillion by 2025. These numbers underscore the growing risks that accompany our increasingly digital world.
So, where does threat modeling fit into all this? Let’s dive into some practical examples.
Source: What is Threat Modeling? Methodologies, Types, and Steps
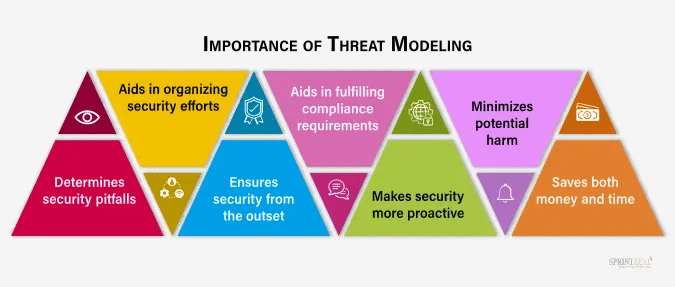
Threat modeling isn’t just a checklist—it’s a fundamental approach that drives proactive security throughout the software development lifecycle. Threat modeling ensures that security measures evolve in tandem with development.
Key Benefits of Threat Modeling in DevSecOps:
Each threat modeling framework serves a different purpose and excels in specific areas. Here’s how you can apply them effectively in a DevSecOps context.
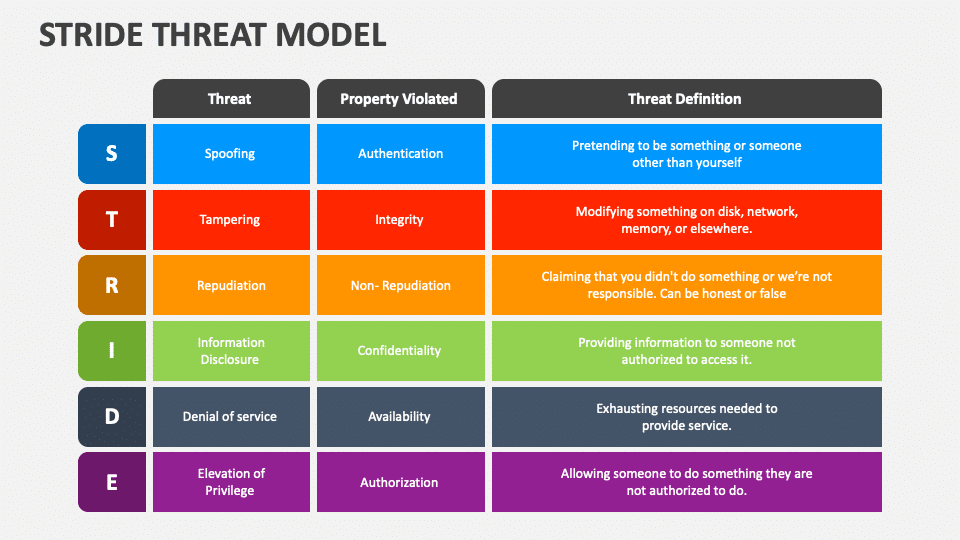
Source: Enhance Your Cybersecurity with STRIDE Threat Modeling
The STRIDE model breaks down threats into six categories: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. It’s particularly effective in identifying and addressing security risks during the development design and planning stages.
Example in Action: Suppose your team is developing a microservices architecture for financial transactions. Applying STRIDE during the design phase can help identify spoofing risks.
Implementing mutual TLS (mTLS) between microservices ensures that each service verifies the identity of the other before any data exchange, significantly reducing the risk of an attacker slipping into the system.
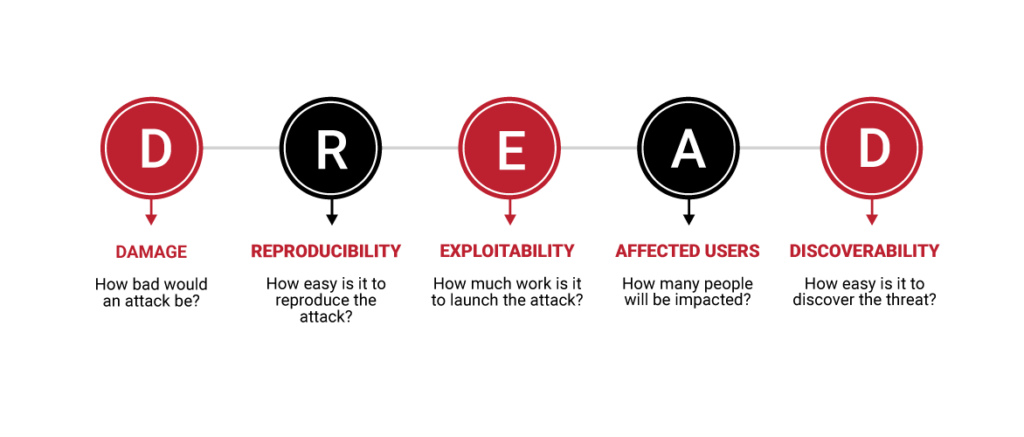
Source: Threat Modeling
DREAD provides a structured approach to evaluating and prioritizing threats based on Damage potential, Reproducibility, Exploitability, Affected users, and Discoverability. Why is this beneficial? The DREAD model helps guide resource allocation by focusing on the most significant risks.
Example in Action: In a web application where user data is entered into forms if a SQL injection vulnerability is discovered, DREAD helps your team prioritize fixing the issue.
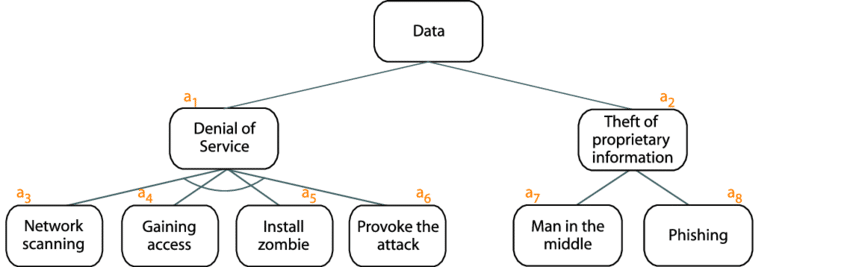
Source: An example attack tree.
Attack Trees provide a hierarchical, visual representation of all the possible ways an attacker could compromise a system. Each tree branch represents a different strategy or method an attacker might use.
Example in Action: Imagine you’re securing a CI/CD pipeline that automates deployments. The root of your Attack Tree might be an attacker gaining access to your deployment server. Branches could include compromising the CI/CD tool, stealing credentials, or exploiting a vulnerability in the deployed application.
By detailing each potential attack path, the team can prioritize securing the CI/CD tools with strong access controls, patching all components regularly, and using environment-specific secrets that are rotated frequently.
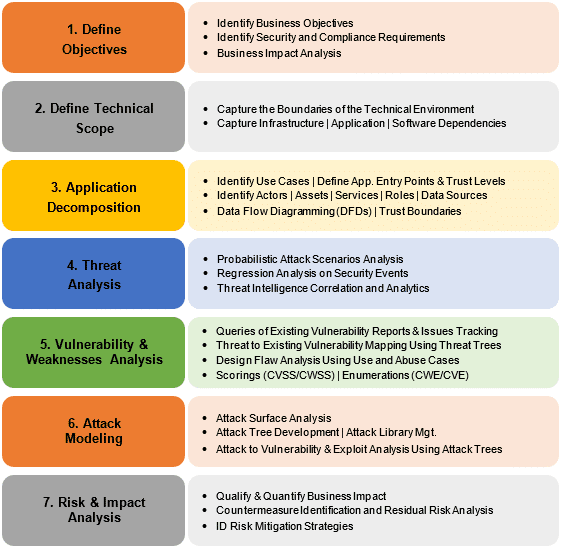
Source: Introduction of PASTA Threat Modeling
The Process for Attack Simulation and Threat Analysis (PASTA) is a framework that emphasizes aligning security measures with business objectives. It’s a seven-step process that integrates technical and business perspectives, making it particularly valuable in environments where security priorities must be balanced with organizational goals.
Example in Action: For an online retail platform, PASTA could simulate an attack where an attacker tries to exploit a vulnerability in the payment processing API. By running this simulation, the DevSecOps team might discover that the API lacks sufficient rate limiting, allowing the attacker to overwhelm the system with fraudulent transactions.
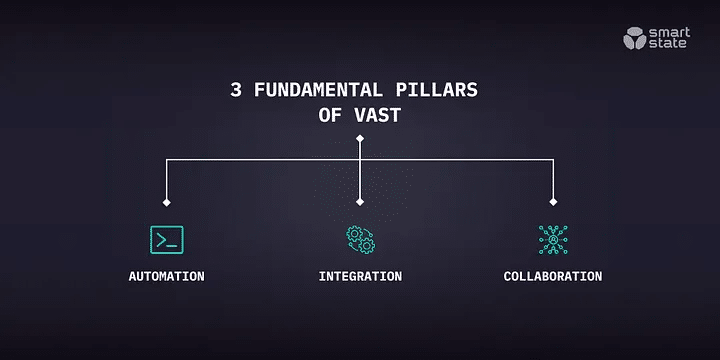
Source: Threat Modeling Methodology: VAST
VAST (Visual, Agile, and Simple Threat) is designed for large-scale environments, emphasizing simplicity and scalability. It integrates well into Agile workflows, making it ideal for organizations needing to continuously and collaboratively assess threats.
Example in Action: In a company with multiple Agile teams working on interconnected microservices, VAST allows each team to model threats relevant to their specific service during every sprint. For example, one team might focus on securing the communication between microservices, using VAST to visualize and address potential IoT protocol security issues.
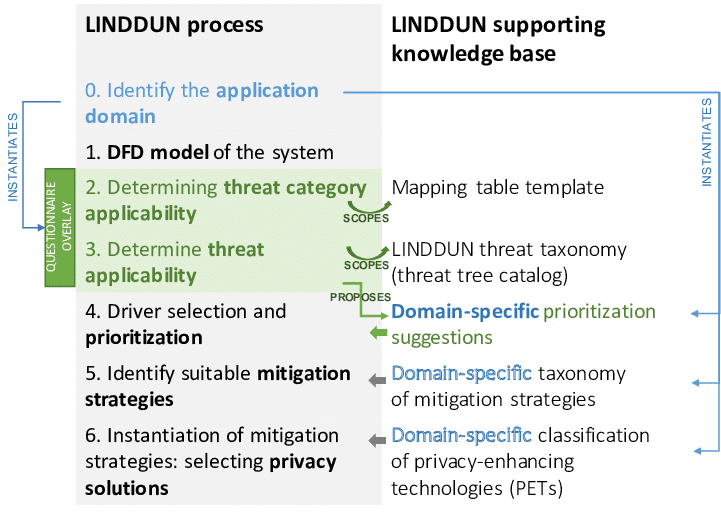
Source: Presented improvements to the LINDDUN framework
LINDDUN is focused on identifying and mitigating privacy threats, making it indispensable in projects where data privacy is paramount. Each component of LINDDUN—Linkability, Identifiability, Non-repudiation, Detectability, Disclosure of Information, Unawareness, and Non-compliance—addresses different aspects of privacy risk.
Example in Action: Consider a healthcare application that manages patient records. Using LINDDUN, the DevSecOps team might identify that certain data elements—like patient IDs—could be linked to other datasets, potentially compromising patient privacy.
To mitigate this, the team implemented strong encryption and data discovery tools to ensure that even if data is intercepted, it cannot be traced back to individual patients.
To effectively implement threat modeling, it’s essential to understand where each framework fits within the DevSecOps pipeline. Below is a table that categorizes the frameworks discussed above and provides examples of where they can be applied:
| Framework | Pipeline Stage | Example of Application |
| STRIDE | Design and Planning | Identifying spoofing risks in a microservices architecture. |
| DREAD | Risk Assessment | Prioritizing SQL injection vulnerabilities based on severity. |
| Attack Trees | Development and Deployment | Mapping potential attack vectors in a CI/CD pipeline. |
| PASTA | Business Alignment | Simulating API attacks to protect payment processing systems. |
| VAST | Continuous Integration | Assessing security threats in microservices during each sprint. |
| LINDDUN | Data Privacy Compliance | Protecting patient data privacy in a healthcare application. |
To effectively integrate threat modeling into your DevSecOps culture, consider these essential practices and tools:
By integrating these practices with the right tools, threat modeling becomes a seamless part of your DevSecOps pipeline, supporting continuous improvement and adaptability.
Incorporating threat modeling into your DevSecOps practices is essential for maintaining a robust security posture in today’s increasingly complex digital environments. By understanding and applying frameworks like STRIDE, DREAD, and LINDDUN, teams can proactively address potential threats before they escalate.
As you refine your threat modeling processes, consider leveraging tools to enhance efficiency and effectiveness. Spectral offers powerful capabilities to automate and integrate threat modeling within your existing CI/CD pipelines, helping you avoid potential risks.Ready to take your DevSecOps security to the next level? Explore what Spectral can do for your team.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions