Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
If you use the Azure cloud, Azure security groups should be on your radar because they’re a fundamental component of securing your resources. As we move into 2023, 63% of SMB workloads are hosted in the cloud, and cyber threats continue to increase, with 45% of breaches reportedly being cloud-based. The good news is Azure security groups act as virtual firewalls, allowing you to define and control access to your network resources, such as virtual machines, subnets, and applications.
Setting up Azure security groups correctly is crucial in safeguarding your environment from unauthorized access, data breaches, and other security risks. By implementing well-structured security groups, you can establish a robust security posture for your Azure resources, adhere to industry best practices, and maintain compliance with relevant regulations.
Today we share insider tips on creating a secure and efficient network architecture that supports your business needs and protects your cloud environment.
There are two main types of Azure security groups: Network Security Groups (NSGs) and Application Security Groups (ASGs).

NSGs act like traffic cops for your network, controlling inbound and outbound flows. By creating and applying NSG rules, you can dictate which ports are open and which IP addresses can access your network resources. NSGs are perfect for securing your Virtual Networks (VNets) and Virtual Machines (VMs), ensuring that only authorized traffic is allowed.
ASGs help you achieve micro-segmentation by logically grouping VMs with similar functions and applications. This lets you apply NSG rules based on the group’s specific needs, making it easier to manage large-scale environments. Think of ASGs as the superhero sidekicks of NSGs. Together, they protect your precious resources from security threats.
But remember, with great power comes great responsibility. By understanding the different types of Azure security groups and how they work, you’ll be well-equipped to create a secure and efficient network environment for your applications. So here are our tips to help you start setting up and optimizing your Azure security groups.
Before diving headfirst into Azure security groups, it’s crucial to have a solid understanding of the process. Here’s a brief overview of the steps involved in creating and assigning Azure security groups:
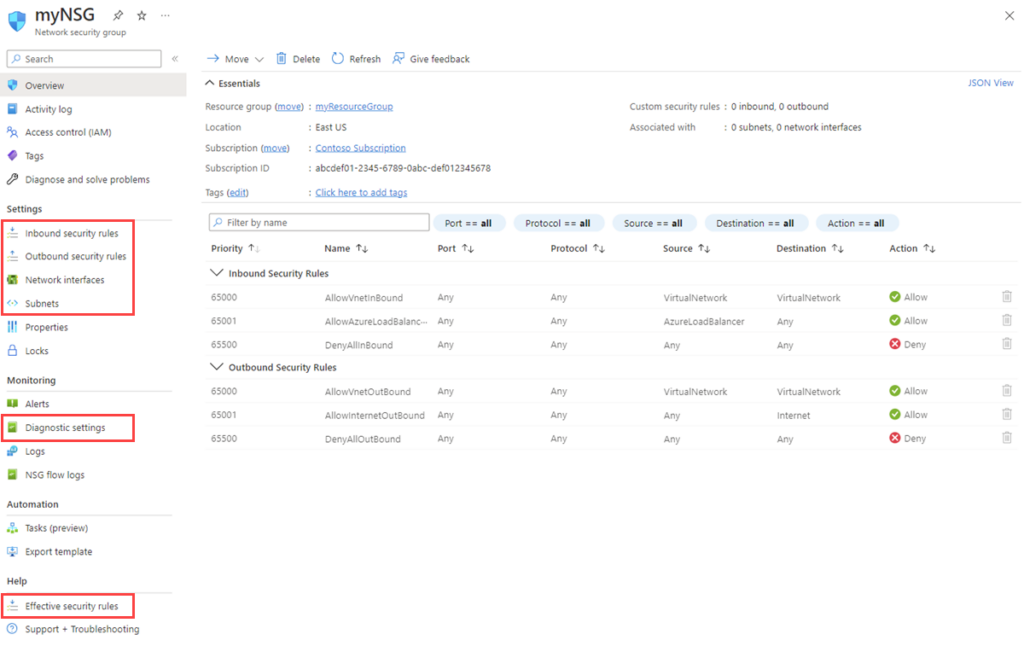
Lay out a plan for your security groups based on your application architecture and network design. Consider the various Azure security group types (such as NSGs and ASGs) and how they will secure your resources together.
Create NSGs in the Azure portal by navigating to the “Network Security Groups” service and clicking “Add.” Fill in the required information, and your NSG will be ready for action.
With your NSG in place, it’s time to define the rules dictating your network traffic. Create inbound and outbound rules specifying the source, destination, protocol, and port numbers. Remember, order matters! Rules are processed in priority order, from lowest to highest.
For a more granular approach, use ASGs to logically group VMs with similar functions. Go to “Application Security Groups” in the Azure portal and click “Add.” Provide a name and choose your subscription and resource group.
Now that you’ve created your security groups, it’s time to assign them to your resources. You can associate NSGs with VNets, subnet levels, or individual VM network interfaces. To assign ASGs, update your NSG rules by selecting the ASG as the source or destination.
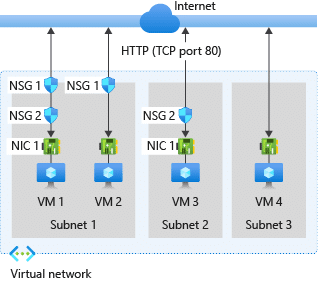
Before configuring Azure security groups, make sure you understand the basics. This includes knowing how Network Security Groups (NSGs) and Application Security Groups (ASGs) work together to secure your network resources. When naming your resources, use a clear and consistent naming convention that makes them easy to identify and manage.
NSGs are key to defining inbound and outbound traffic rules for your VMs and subnets. By creating NSG rules, you can allow or deny specific traffic based on source and destination IP addresses, protocols, and port numbers. This granular control helps you protect your network from unauthorized access.
Azure Firewall is a managed, cloud-based network security service that offers stateful packet inspection, intrusion detection, and application-level gateway services. It provides advanced threat protection and helps secure traffic between virtual and on-premises networks. By integrating Azure Firewall with your security groups, you can achieve a comprehensive and robust security solution for your environment.
Azure Bastion is a fully managed PaaS service that provides secure and seamless RDP/SSH connectivity to your virtual machines directly from the Azure portal. With Azure Bastion, you don’t need to set up VPNs or expose your VMs through public IP addresses. It acts as a secure “jump server,” enabling you to access your VMs while protecting your environment from threats.
It’s crucial to define security rules that reflect your business needs. For example, you may need to allow specific IP addresses or port numbers for inbound and outbound traffic to meet compliance requirements or to secure access to critical resources. You’ll create a more secure and efficient network by tailoring your rules to match your unique environment.
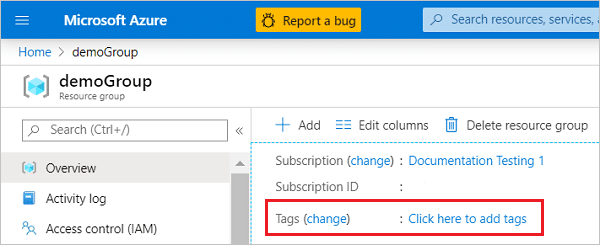
As your environment grows, managing security groups can become challenging. Tags help you easily organize and manage your security groups by adding metadata to your resources. For instance, you can create tags based on environment (production, staging, test), application, or owner. With tags in place, you can quickly filter, search, and report on your security groups, making management a breeze.
Implementing the principle of least privilege is essential for maintaining a secure environment. Limit access to management ports such as SSH, RDP, and SQL to only authorized users or IP addresses. This can help prevent unauthorized access and reduce your attack surface. Consider using tools like Azure Bastion or Just-In-Time (JIT) VM access to further secure your management ports.
Azure Active Directory (AD) is a cloud-based identity and access management service that provides authentication, authorization, and single sign-on (SSO) capabilities. Integrating Azure AD with your security groups allows you to manage resource access based on user roles and permissions.
Azure Security Center is a comprehensive security monitoring and management service that helps you protect your Azure resources. It provides advanced threat protection, security recommendations, and compliance management capabilities. To set it up, navigate the Azure portal, locate Azure Security Center, and follow the onboarding process. By enabling Azure Security Center, you’ll gain insights into your security posture and receive actionable recommendations to improve it.
Security isn’t a one-time task. Regularly review and update your security rules to ensure they remain relevant and aligned with your business needs. Continuously monitor security logs for suspicious activity and investigate any potential security incidents.
Congratulations, you’re now equipped with a wealth of insider tips to set up and manage Azure security groups. To further enhance security without compromising speed, integrate Spectral with Azure so you can build and ship software without worry. Spectral’s scanning engine combines AI and hundreds of detectors to monitor, classify, and protect your code, assets, and infrastructure from exposed API keys, tokens, credentials, and security mistakes. The tool is designed to find harmful security errors in code, such as cloud misconfigurations, in real-time so that you can build and ship software without worry. Request a free demo today.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Continuous integration and delivery are necessary in any production level software development process. CI/CD are more than just buzzwords. Rather, it is a fully-fledged methodology of