Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Have you ever produced a bug-free, well-tested release candidate that later failed the security tests done by InfoSec? This may be due to your security testing being done too late in your development cycle.
Even if you are already using a CI/CD pipeline, there are still things you can do to improve your process and catch security and compliance issues much earlier in your development process. And what better way to see the impact Shift-Left security can have than employ free and open-source tools you can adopt today at no cost?
The waterfall development cycle is a dying breed, but vigorous security checks are often kept for the end of the development cycle even in today’s agile environments. If a security issue is found by a manual test between the Continuous Integration and the Continuous Delivery sections of the pipeline, the software must be kicked back to development, forcing the entire process to halt and revert.
This kickback to the “left” part of the CI/CD pipeline is what Shift Left security avoids. Shift left security aims to minimize interruptions by automating security tests as part of a CI/CD pipeline. When security is tested as part of the regular testing process, there is no halt in the flow.
The benefits of shift-left security all boil down to cost. At the top of the list is improved security. An organization that works with a left-shifted security model promotes a culture of security. When it is not only the security team’s focus to maintain security but also DevOps and developers, the organization’s culture will be security-focused.
When security is kept in mind by all employees, there are simply more eyes (and brains) working on maintaining a high level of security. Better security means fewer leaks, and fewer leaks, you know it, means lower costs.
But what about the development cycle? Shift-left security allows a quicker back and forth between fault detection and the development team prompted to fix it. Without such early intervention, security issues can be very costly.
If a security issue is found late in the pipeline, probably in manual testing, the continuous delivery might hit a wall. Worse, security issues can often require significant overhauls of code, even resetting the development.
Shift left security is about testing for security as early as possible. This is done using automated tools that allow doing so as part of a CI/CD pipeline. These tools enable you to make effective security testing without increasing the time and cost of the development cycle.
SAST is a testing method by which source code is scanned for vulnerabilities without needing to compile and run the code. The best SAST solution will prompt developers as early as during the coding process. SAST can also be integrated into CI/CD pipelines and act as a gateway. Some can also be configured to enforce code structure based on your organization’s guidelines.
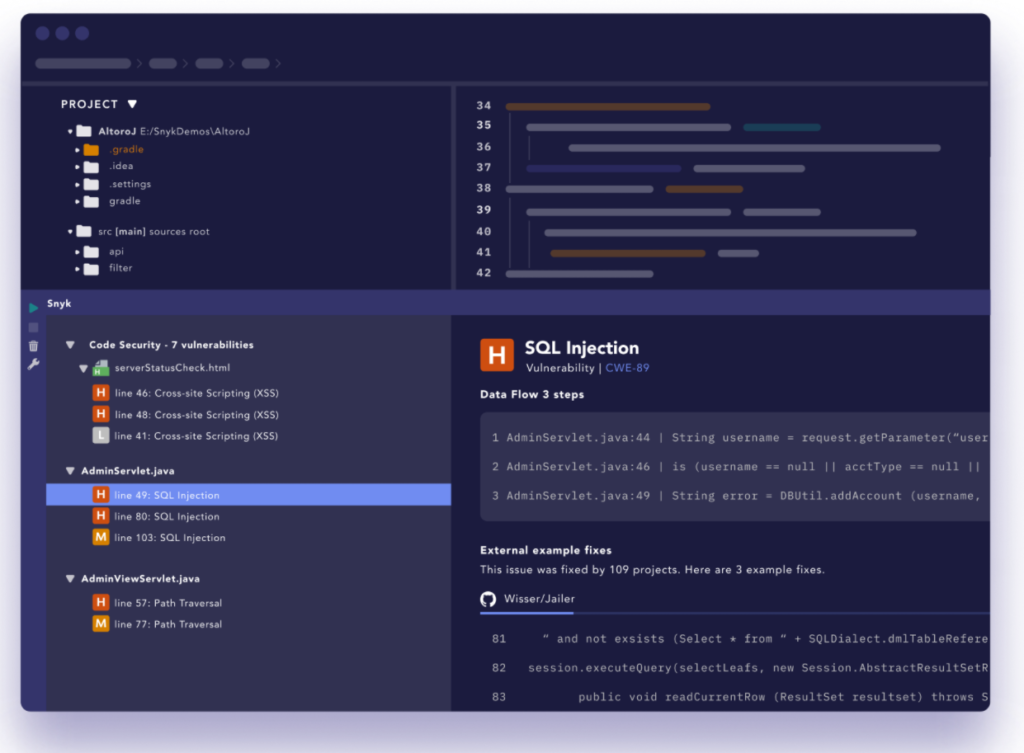
Snyk uses several tools in conjunction to provide a robust security check before code is compiled. An IDE plugin prompts the developer of any issues while still working on the code. A CI/CD gateway prevents bad code from continuing into further steps, and native Git scanning allows continuous monitoring of your source code.
Secrets are used by software to create connections with other software. These secrets can be API Keys, authorization tokens, encryption keys, credentials, and more. What makes them secrets is that they only work correctly as long as they are not publicly available. Secret leakage and credential compromise are worryingly common and expensive. The best way to prevent code secrets from being exposed to malefactors is secret scanning.
Secret scanning is a process that can be done manually, but it is extremely inefficient to do so. The best secret scanning solutions are automated tools that use sophisticated AI or machine learning to detect secrets rather than rely only on RegEx. Only highly specialized tools can find secrets without a high number of false positives and without significant impact on your CI/CD pipeline.
Spectral is a secret scanner built by developers for developers and puts a high focus on not interrupting your workflow. It is easy to set up and provides excellent secret detection at a very low cost to your CI/CD pipeline.
Spectral will scan all your files continuously, without copying or compromising them. With seamless integration with any stack and any language. Try it out and see the impact yourself.
Most if not all software is dependent on frameworks and libraries developed by external sources. Those resources are exposed to various degrees of scrutiny by the development community. Some libraries are so commonly used but such a large variety of developers that they are probably maintained at a higher standard than your organization’s source code. But not all of those resources are created equal.
Sometimes you need access to an obscure set of functions, like say a bridge between two pieces of software that don’t usually communicate. Those types of libraries are often open-source and should be tested and scanned. Dependency Scanners check dependencies for security issues and do so at an early stage of the development cycle, freeing you from worry.
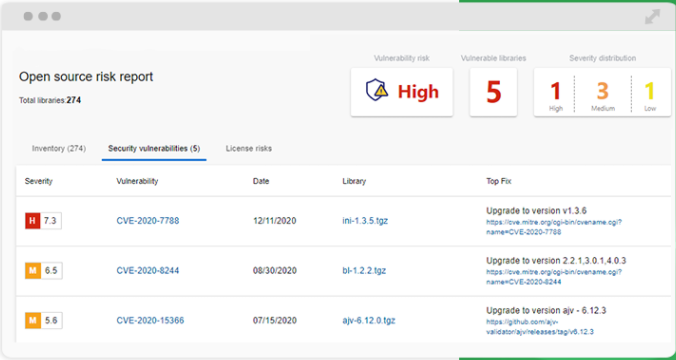
WhiteSource Bolt’s scanner has a GitHub and an Azure app, allowing it to easily scan dependencies from those sources. Bolt provides a detailed report of potential vulnerabilities and offers potential fixes. It’s also completely free.
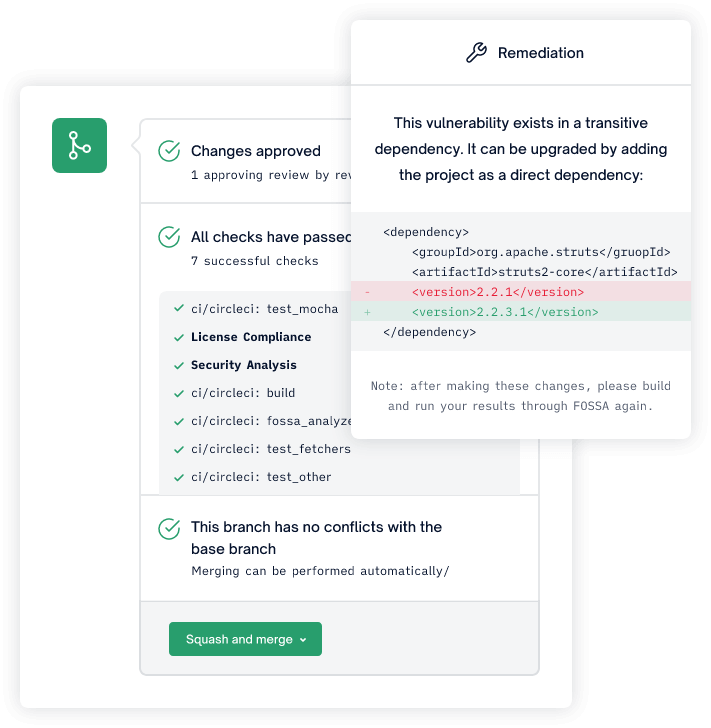
For FOSSA compliance is the name of the game. Fossa provides hassle-free compliance remediation per your policies. It provides fast and accurate insights as part of your CI/CD pipeline. Being easy to use by your team means that the tool will continue to provide value over time.
DAST is a tool to actively assess vulnerabilities in running applications. Also known as black-box testing, DAST tools attempt to find vulnerabilities by exposing your software to common attacks such as SQL injections. DAST tools can provide automated testing at a late stage of your CI/CD pipeline, but can also be manually operated by Quality Assurance and/or security teams.
Burp is a multi-layered application security tool, offering not only DAST, but OAST, IAST, SCA, and SAST. The free community version is quite limited and is probably best to look at it as a demo rather than a possible free solution. That said, if you like what you see, they have scalable pricing so you’re likely to find the tier where the cost-benefit ratio is to your liking.

Zed Attack Proxy (ZAP) is free, open-source, and maintained under the Open Web Application Security Project (OWASP). ZAP positions itself between the tester and the web application as a proxy, allowing it to modify and control packet information to enable better testing. Being open-source means you are free to inspect the code to make sure it does what it says on the box – an important feature for a security tool.
Interactive Application Security testing is a sort of hybrid between SAST and DAST, allowing both source code analysis and runtime inspection. Running later in the development cycle than SAST, it can still be done fairly early as long as there is a stable build to run.
While Contrast Community Edition is limited to a single onboarded application, it provides all the features of the full product. This allows you to quickly assess the value it may provide to your testing suite. An almost entirely automated process that promises to not bother you with false positives and a clear path to remediation.
Run-time Application Self Protection is a protection layer that runs server-side as soon as the application starts. It uses databases and knowledge found by organizations such as the Open Web Application Security Project (OWASP) to prevent attacks and recognize any potential false positives. RASP gives a high level of protection from SQL injection, Server-Side Request Forgery (SSRF), and Cross-Site Scripting (XSS).
Unlike In-App Web Application Firewall (In-App WAF), RASP is integrated into the application allowing it to use context when deciding if a request is malicious or not, reducing false positives.
Aimed at protecting microservices and APIs, this tool is highly specialized and as such does a very good job. Sqreen is a library installed onto your application that acts as an un-intrusive agent to prevent attacks on your application. Sqreen is more than a RASP, as it also provides Content Security Policy (CSP) and (In-App WAF).
OpenRASP is an open-source RASP solution that does what a RASP needs to do. It will stop only attacks that are going to be successful, all but eliminating false positives. It has a relatively small community and as such you’re likely to need to figure out a lot on your own. But there are several forums such as a google group that offers technical support.

There are many free (and even more paid) tools in the market to help shift-left security. The core ones that are often neglected are the SAST, Secret Scanners, and Dependency scanners. Those tools can provide added security through CI/CD integration without modifying your codebase, and are tools necessary in today’s security landscape.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions