Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Sensitive customer information leaked, operations disrupted, and reputation tarnished – this is not the headline you want splashed across the internet.
There’s a 76% spike in data theft victims and a 75% increase in cloud intrusions. Vulnerabilities are lurking within every organization’s digital infrastructure – but how do you stay ahead of security threats?
The answer is simple – proactive security testing.
Penetration testing (or pen testing) and vulnerability scanning are two critical tools in the fight against cyberattacks. Penetration testing (or pen testing) simulates real-world cyberattacks to assess how well your defenses hold up. In contrast, vulnerability scanning involves automated checks against databases of known security flaws, helping you identify and prioritize potential weak points in your systems.
Vulnerability scanning is an automated process that analyzes systems, networks, and applications to identify potential security weaknesses. Different vulnerability scanners exist, including network-based scanners that scan systems remotely, agent-based scanners that use installed software on the target systems, and container scanners that analyze containerized applications. Misconfigurations are a common security risk, so identifying and addressing them is crucial.
At its core, vulnerability scanning involves matching the configurations, software versions, and other attributes of the scanned environment against databases of known vulnerabilities, such as the Common Vulnerabilities and Exposures (CVE) database maintained by MITRE. These databases contain detailed information about publicly disclosed vulnerabilities, including their severity, affected products, and potential impacts.
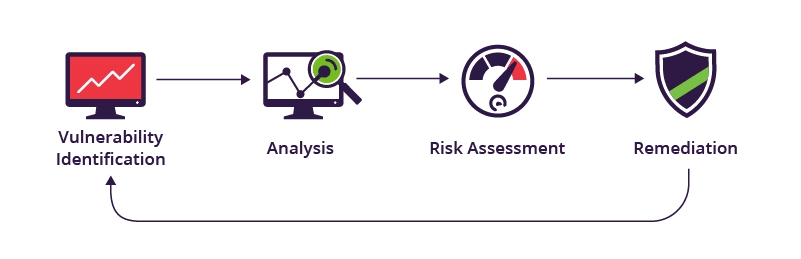
Vulnerability scanners can detect many issues, from network vulnerabilities like misconfigured firewalls to outdated software and web application flaws. Staying informed about the most common web application vulnerabilities, such as those in the OWASP Top 10 list, is essential for proactive security.
One of vulnerability scanning’s primary advantages is its automated and scalable nature. Scanners can efficiently assess large and complex environments, making it possible to maintain a regular cadence for proactive risk identification. This systematic approach helps organizations avoid emerging threats and promptly address vulnerabilities as they are discovered.
While vulnerability scanning is a valuable tool, it has its limitations. False positives, where vulnerabilities are incorrectly reported, can waste time and resources. Additionally, scanners rely on known vulnerability signatures and may not detect zero-day vulnerabilities or complex attack vectors.
While a scanner may identify a potential weakness, it cannot determine with certainty whether an attacker could successfully exploit that vulnerability in the specific context of the target environment. For some organizations, exploring the benefits of a multi-cloud architecture may be a strategic way to enhance security posture.
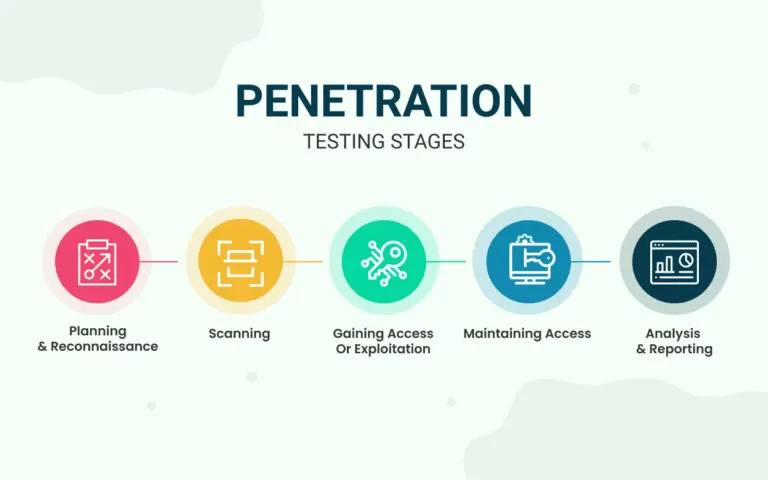
Penetration testing, or pen testing, is a comprehensive process that mimics real-world cyber attacks to identify and exploit vulnerabilities in an organization’s systems and applications. The process typically follows a structured approach involving a few phases:
Pentesters use many tools and techniques throughout the process, including port scanning, social engineering tactics, web application attacks (such as SQL injection and cross-site scripting), privilege escalation methods, and more.
Penetration tests can be conducted on various components of an organization’s infrastructure and applications, including:
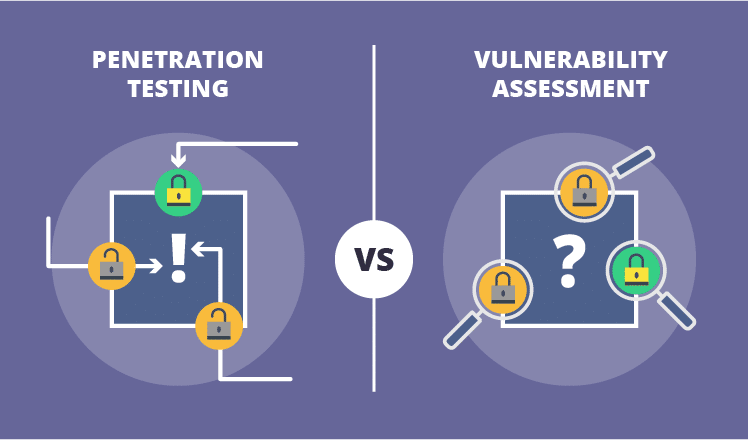
The primary benefit of penetration testing is that it goes beyond mere vulnerability identification and actively demonstrates the potential impact of successful exploitation. By simulating real-world attacks, pentests can uncover logic flaws, chained vulnerabilities, or misconfigurations that vulnerability scanners might overlook.
Pentesting provides a more realistic view of an organization’s security posture, helping to prioritize remediation efforts based on the actual risk posed by identified vulnerabilities.
While highly valuable, penetration testing can be time-consuming and more costly than vulnerability scanning, especially for large environments. Additionally, the scope and rules of engagement for pentests must be clearly defined to avoid potential legal issues or unintended impacts on production systems; overall, pentests require more thought and rigorous planning.
The decision to employ vulnerability scanning or penetration testing depends on various factors, including the criticality of the systems, the maturity of the organization’s security program, regulatory compliance requirements, and available budget and resources.
Situational Suitability: Highly critical systems that handle sensitive data or support mission-critical operations may warrant the in-depth assessment provided by penetration testing. In contrast, less critical systems may benefit from regular vulnerability scanning.
Maturity of a security program: Organizations with established security practices and mature vulnerability management processes may find value in penetration testing to validate the effectiveness of their security controls. Conversely, organizations in the early stages of building their security program may start with vulnerability scanning to establish a baseline.
Regulatory compliance requirements: Certain industries and regulations have specific security standards. Understanding frameworks like NIST SP 800-53 and how they apply to your systems is crucial for ensuring compliance. For example, the Payment Card Industry Data Security Standard (PCI DSS) explicitly requires periodic penetration testing for sensitive data systems.
Budget and resource availability: Penetration testing can be more resource-intensive and costly than vulnerability scanning, making it essential to consider budget and staffing constraints when deciding on the appropriate approach.
Vulnerability Scans: Vulnerability scans are ideal for organizations seeking broad coverage across many systems and applications. When choosing a vulnerability scanning solution or an MSSP (Managed Security Service Provider), consider factors like frequency, automation capabilities, and the ability to prioritize vulnerabilities based on risk.
Vulnerability scanning is well-suited for:
Penetration Tests: Penetration tests, on the other hand, are best suited for in-depth assessments of critical assets and validating the effectiveness of security controls. Understanding which assets are most critical to your business operations is a crucial first step in prioritizing security testing.
Pentesting is particularly valuable in scenarios such as:
While vulnerability scanning is typically a continuous part of the development process, penetration testing provides a deeper, more targeted evaluation of an application or system’s security posture at specific milestones or before critical deployments.
| Feature | Penetration Testing | Vulnerability Scanning |
| Approach | Active exploitation of vulnerabilities, mimicking real-world attacks. | Automated scanning against databases of known vulnerabilities. |
| Focus | In-depth assessment of security posture, validating exploitability. | Broad coverage and frequent identification of known risks. |
| Depth | Uncovers logic flaws, chained vulnerabilities, and misconfigurations. | It may not detect zero-day, complex attack vectors. |
| Cost | Typically, it is more expensive due to manual effort. | More cost-effective, scalable solution. |
| Ideal Use Cases | * Critical systems or applications. * Validating security controls. * Meeting regulatory compliance (e.g., PCI DSS). | * Broad coverage across many systems. * Frequent, recurring security checks. * Baseline vulnerability identification. |
While vulnerability scanning and penetration testing have distinct methodologies, a robust security posture often involves a combination of proactive measures. Establishing well-defined security policies is a foundational step, alongside regular vulnerability assessments and targeted penetration testing. By leveraging the strengths of both approaches, organizations can achieve a proactive strategy for identifying and assessing potential security risks.
Vulnerability scanning provides a scalable way to continuously monitor systems and applications for known vulnerabilities. The results of these scans can streamline the initial reconnaissance and discovery phases of a penetration test, allowing pen testers to focus their efforts on actively exploiting the identified vulnerabilities and uncovering potential logic flaws or misconfigurations.
Conversely, penetration tests’ findings demonstrate the real-world impact of successful exploits. Pen testing results can help organizations prioritize the remediation of the most critical vulnerabilities based on their actual risk exposure, which can be valuable when developing a cyber resilience framework.
While vulnerability scanning and penetration testing have distinct methodologies, they are complementary practices that can significantly enhance an organization’s security posture. By leveraging the strengths of both approaches, organizations can achieve a proactive strategy for identifying and assessing potential security risks.
Don’t let your organization remain vulnerable. If you’re looking for a powerful tool to streamline your vulnerability scanning processes, SpectralOps offers a developer-first solution that seamlessly integrates into your development workflows. Prioritize security from the earliest stages of development, enabling your team to build more secure applications. Sign up for your free SpectralOps account today to protect your systems and data proactively.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions