Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Every day, headlines scream about data breaches and cyberattacks. Could your organization be next? If you’re not using Mandatory Access Control (MAC), you’re leaving your sensitive information vulnerable to unauthorized access.
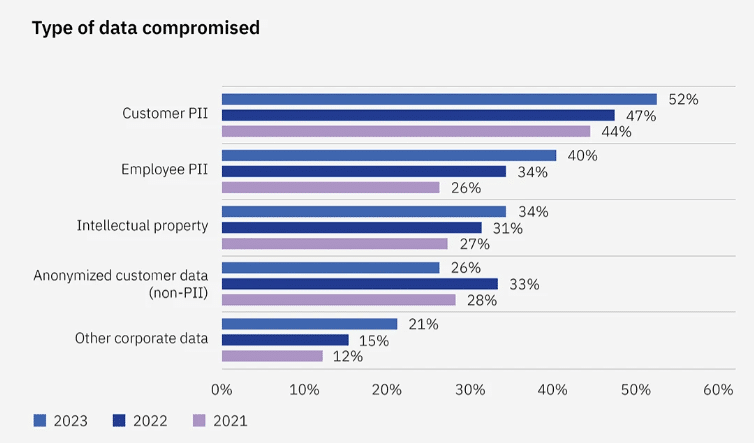
The fear is real – 52% of data breaches expose customer information, wreaking havoc on reputations and bottom lines. But what if you could drastically reduce this risk?
Mandatory Access Control (MAC) is not just another security tool; it’s a paradigm shift. By enforcing strict access controls based on data classification and user clearance, MAC creates a multi-layered defense that protects your most sensitive information. Imagine a robust security system that adapts to your organization’s unique needs, safeguarding data from internal and external threats.
That’s what MAC is for.
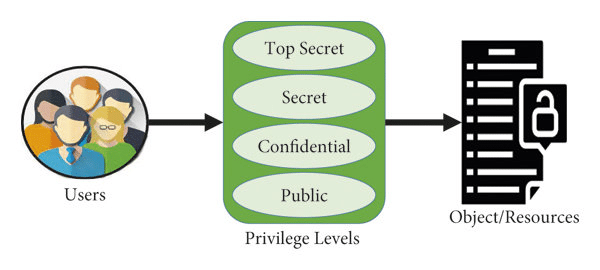
In a Mandatory Access Control (MAC) security model, a central authority manages resource access according to classifications and clearance levels. To ensure the safety and security of critical information, MAC assigns labels and clearances to both users and objects.
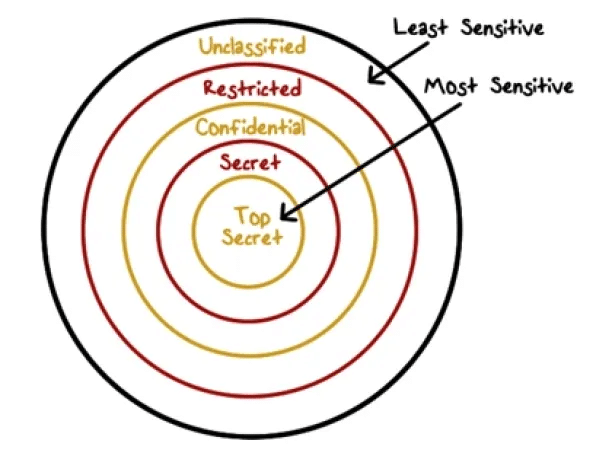
In this lattice-based system, classifications and clearances form a structured hierarchy. Security administrators assign users matching clearance levels, determining what they can access. For instance, someone with a Secret clearance can access Confidential data but is barred from top-secret information.
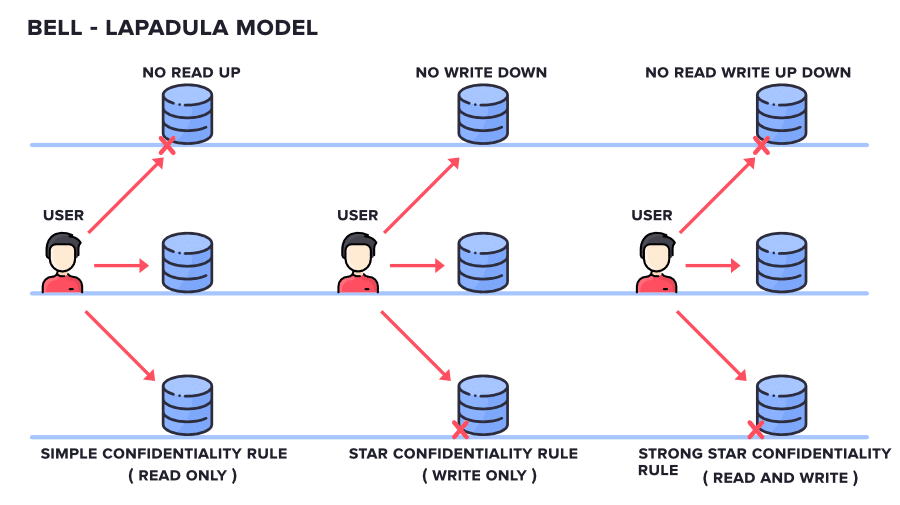
By enforcing the Bell-LaPadula model, aka the “no read up, no write down” rule – users can’t read data above their clearance level or write data to a lower level, guaranteeing tight control over information flow and preventing data leaks.
Organizations can leverage tools like SaaS Security Posture Management (SSPM) to complement MAC and further enhance security. SSPM solutions can help monitor and continuously secure software-as-a-service (SaaS) applications.
Mandatory Access Control (MAC) offers a range of benefits, especially in settings where data confidentiality is paramount. With centralized control, MAC enforces uniform access policies, significantly reducing the risk of data leaks. This setup means only users with the correct clearance can access sensitive information, keeping it out of unauthorized hands.
One of MAC’s standout advantages is its ability to help organizations navigate regulatory compliance. Adhering to strict security standards is a legal necessity in fields like government, military, and healthcare. MAC supports compliance by providing a well-structured access control framework.
For instance, in the military, MAC restricts classified information access to personnel with the correct clearance, aligning with national security regulations. MAC facilitates HIPAA compliance in healthcare by limiting access to authorized staff records safeguarding patient privacy and sensitive health data.
If your application handles highly sensitive information, you need MAC. This includes PII (names, addresses, Social Security numbers), medical records (patient data, diagnoses), trade secrets (proprietary algorithms, business strategies), financial data (credit card numbers, transactions), and exposed secrets (e.g., API keys, credentials).
MAC locks down access to this data – protecting your most critical information from breaches and leaks. Airtight IT security policy locks down access to sensitive data. Additionally, phishing attacks targeting this sensitive information can be mitigated through AI-powered defenses, enhancing the overall security posture.
Regulatory compliance is a critical concern if you’re working in industries like healthcare, finance, or government. MAC helps you meet these regulations and avoid costly non-compliance fines. Vital regulatory considerations include:
When only specific individuals should access certain data, relying on user discretion can be risky. For example, a developer might accidentally stumble upon or be tempted to access confidential project files beyond their scope of work.
MAC addresses this by enforcing the “need to know” principle – if you don’t need the data, you don’t have access to it. In this scenario, MAC would make top-secret project files only accessible to team members directly involved.
In a hospital, different roles need varying degrees of access to patient data. This requires multiple security levels. MAC assigns specific clearance levels to each role based on their access needs. Consider this setup:
MAC employs a “no read up, no write down” rule to maintain data confidentiality. This means users cannot read data above their clearance level or write data to a lower classification level. This rule is essential for preventing data leakage due to accidental access, malicious intent, or misconfigurations. The Sisense breach underscores the importance of this rule, highlighting the need for robust secrets protection mechanisms.
The rule is enforced through Access Control Lists (ACLs), security labels, and reference monitors. ACLs specify user permissions and check clearance levels. Security labels tag data and users with classification levels, aiding real-time decisions. Reference monitors evaluate access requests against ACLs and security labels to grant or deny access.
Hierarchical enforcement maintains strict boundaries between data sensitivity levels, reducing the risk of breaches and preserving the integrity of the security framework.
MAC’s scalable security model is also perfect for large organizations or systems with complex classification structures. By organizing data into a hierarchy of classifications and clearances, MAC can manage access efficiently across vast and intricate networks.
With Zero Trust Architecture, the security model remains effective and adaptable as an organization expands or data classification needs to change.
Implementing and maintaining Mandatory Access Control can be complex and resource-intensive. Consider all the access controls and classification levels needed. However, this trade-off is worthwhile when granular control over data access is essential.
Where data breaches can have serious consequences, MAC’s tight control outweighs the flexibility of less stringent models. You must consider whether MAC’s security benefits are worth the added complexity.
Overclassification—labeling data as more sensitive than necessary—can over-restrict access, slow productivity, and frustrate users. On the flip side, underclassification can expose sensitive data to unauthorized access.
Automated labeling solutions can help. Tools like SELinux and AppArmor offer robust frameworks for labeling. They can automatically classify files, processes, and network communications based on predefined policies. Incorporate these tools into your development pipeline for consistency.
Enforcing MAC policies involves extra system calls and checks, which can slow down operations. Every access request must be evaluated against access control lists and security labels, adding latency to file operations and network interactions.
To lessen these impacts, consider using lightweight MAC implementations or applying MAC selectively to critical subsystems. Tools like SMACK (Simplified Mandatory Access Control Kernel) provide a simpler, less resource-intensive alternative.
Mandatory Access Control (MAC) is a powerful tool for safeguarding sensitive data, but it’s just one piece of the security puzzle. To fortify your defenses, you need a multi-layered approach that addresses vulnerabilities throughout your software development lifecycle.
Spectral complements MAC by providing a developer-first solution for detecting and remediating the very risks that MAC is designed to protect against. Spectral acts as a watchful guardian over your source code and other assets, continuously scanning for exposed secrets, misconfigurations, and other vulnerabilities that could lead to costly data breaches.
Integrating Spectral into your workflow strengthens your MAC implementation and empowers your development teams to address security risks before they escalate proactively. This comprehensive approach ensures that your sensitive data remains confidential, compliant, and secure.
Don’t leave your organization’s security to chance. Discover how Spectral can help you fortify your MAC implementation and protect your most valuable assets. Try Spectral today and take the first step towards a more secure future.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions