Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Becoming and staying PCI compliant both take a lot of work. Developers are often already swamped with an endless list of tasks, and adding PCI compliance can be overwhelming. Security awareness is one thing, but a set of requirements is entirely different. It means you have less freedom in how you wish to implement security in your application, and you must understand the requirements demanded by your organization.
But if you’re using AWS, you can rely on their security expertise and toolset to remain PCI compliant over time without pouring endless resources into audits and third-party security experts. Let’s look at your high-level responsibility as a developer in keeping your application secure.
Security standards are a way to uphold and maintain a minimally-accepted standard to protect the public. The PCI security standards council is responsible for setting, maintaining, and updating standards in the payment card industry. With the PA-DSS discontinued as of 28 October 2022, the PCI-DSS will remain the universal standard for secure storage, transfer, and protection of credit card information.
Any business that handles credit or debit cards in any fashion must adhere to the PCI-DSS or risk fines and the possibility that credit card companies will revoke your merchant status. But it’s important to note that PCI compliance defines the baseline security standard and not the highest possible level of data protection.
Amazon Web Services provide cloud services under the shared responsibility model. This, simply put, means that Amazon is responsible for the security of the cloud, while you, the user, are responsible for security in the cloud.
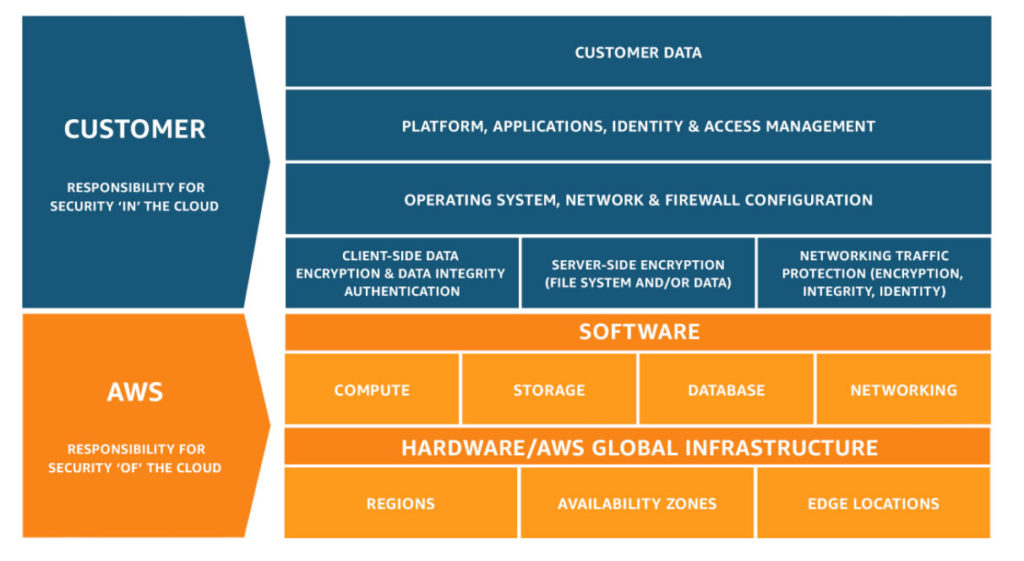
Your responsibility is to maintain and manage the platform, applications, operating systems, and access to those infrastructures. Correct configuration, security patches, data encryption, and network traffic protection are all part of your responsibility. To become and remain PCI compliant, you must be able to prove (under audit) that you have adequately performed your role in securing your systems.
PCI requirements differ based on your organization’s size and the number of transactions you want to process. When you pass the 1 million transactions per year, you’ll be required to maintain a higher standard of compliance with PCI. Developers working on applications that handle credit card transactions must be aware of the specific requirements under PCI-DSS that are relevant to the scope and type of application they are developing.
Data storage, encryption, access control, and network security are at the root of every application that handles cardholder data. Maintaining PCI compliance relies on a secure application with encryption for all sensitive data in transit and adequate access control to prevent data leaks.
Cardholder data is more than the credit card number; it includes names, expiration dates, and CVV numbers. Users will enter this information into your application, and you must ensure it remains secure while the application is running.
Ideally, you should not store cardholder data anywhere. Every system that stores or handles sensitive data must be secured and audited. If you choose to store cardholder data, you must enact adequate security policies to protect them from theft.
Your application will need to share sensitive data over unsecured networks as a matter of daily operations. A cybercriminal can snipe the information in transit. You must ensure the data is encrypted correctly to prevent such attacks. Encryption protocols for all sensitive traffic, such as SSH or SSL, will ensure that data is unusable if you experience a leak.
Cyber security is not a fair game. You must play perfect defense to protect your data, as the slightest error will welcome attackers with open arms. You can stay ahead of potential security threats by continuously monitoring your application and delivering security updates as often as needed.
AWS does more than simply take a share in the responsibility of your PCI compliance. They give you many tools that will simplify maintaining compliance. The AWS Firewall Manager is at the forefront of those tools, streamlining access control using rules you can automatically apply across all your resources and accounts.
Firewall Manager is a central management tool for your VPC security groups that helps prevent unauthorized access to cardholder data across all your AWS infrastructures and resources. The critical feature to help you maintain PCI compliance is the AWS security groups that control incoming and outgoing traffic. The feature groups filter incoming traffic based on ports and source/destination IP addresses.

Security groups are best suited for casting a wide net and applying access control throughout your organization. Implementing baseline controls prevents accidental misconfiguration, as the default may be secure enough to comply with PCI standards. While you can use security groups as a blanket solution, you can also use finesse to apply where and how you need it. AWS Firewall Manager gives you centralized control over your network.
Auditing and logging are core requirements of any compliance regulation, and PCI is no different. AWS Firewall Manager lets you continuously monitor your security groups. The audit scope is up to your specific needs, but you should generally monitor all changes to any accounts and resources. Robust monitoring can help you catch mistakes before they cause damage.
You can even create auditing rules to recognize unused or redundant security groups. Limiting the scope of your security policies means there are fewer opportunities for errors. There are additional options to specify which security groups are allowed in your organization, limiting potential misconfiguration issues.
AWS has built-in compliance monitoring for PCI and includes other standards such as SOC, FedRAMP, and HIPAA. You can get reports and alerts whenever your resources or policies fall into non-compliance. There are additional tools to remediate non-compliance automatically, which you should enable and configure.

Security groups are the cornerstone of a secure and compliant environment. The AWS Firewall Manager is a centralized tool that gives you complete control over network traffic to and from your cloud resources. Staying compliant with PCI in a multi-cloud environment can be challenging. Still, AWS makes it easier both with a shared responsibility model and by providing you with the tools you need to define baseline security, monitor for any changes, and remediate any issues.
Auditing your distributed resources and security policies requires logging—the more logging, the better, as it will be easier to prove compliance. However, the more logs you have, and the further they are scattered across your systems, the higher the likelihood of the logs themselves being a leak source. Spectral ops can provide you with a solution. Spectral Logs is the tool that will grant you visibility over your multitude of logs and ensure no sensitive data can leak by way of logs. With minimal overhead to system resources and maximum efficiency in reducing false positives through an AI monitoring tool, Spectral helps you log everything without a second thought. Try a free demo and see for yourself.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Continuous integration and delivery are necessary in any production level software development process. CI/CD are more than just buzzwords. Rather, it is a fully-fledged methodology of