Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Did you know that 65% of organizations believe they have to choose between innovation and security? This stems from the idea that developers need full access to every resource for them to have the freedom to develop. Which brings up a number of questions. Is there a way to make sure the development process retains the resources necessary for agility without sacrificing security? Can this be achieved in today’s mercurial and increasingly complex cloud computing ecosystem? And if so, how is it all managed without causing DevOps massive headaches? The answer may lay in just three words: cloud security management.
Cloud security management is a multi-step process designed to be proactive about possible security vulnerabilities. It needs to span your entire organization’s cloud dependency from meetings, email, and customer management services, to PaaS (platforms as a service) used by the development teams.
The secure management of cloud assets also needs to encompass data encryption, securing the various devices used by employees, and managing user credentials. Most importantly, cloud security management is an ongoing process. As such, it must be updated and maintained regularly to be effective.
It’s easy to assume that cloud security management is the job of InfoSec teams in IT. However, cloud security is everyone’s job. IT security policies can be inadequate for developer needs, especially when it comes to workload balancing dockers and containers. That’s where DevOps, or more accurately, the role of DevSecOps and CloudOps come in.
Organizations tend to push security risk mitigation to the end of the development cycle, thinking an uninterrupted development would be more efficient. However, this can often result in quite the opposite result. As the security assessment at the end of the DevOps cycle alerts issues of non-compliance, dealing with those issues increases the time to market. Even worse, executives will sometimes push to market because the time allotted for development has run out, without the recommended security precautions.
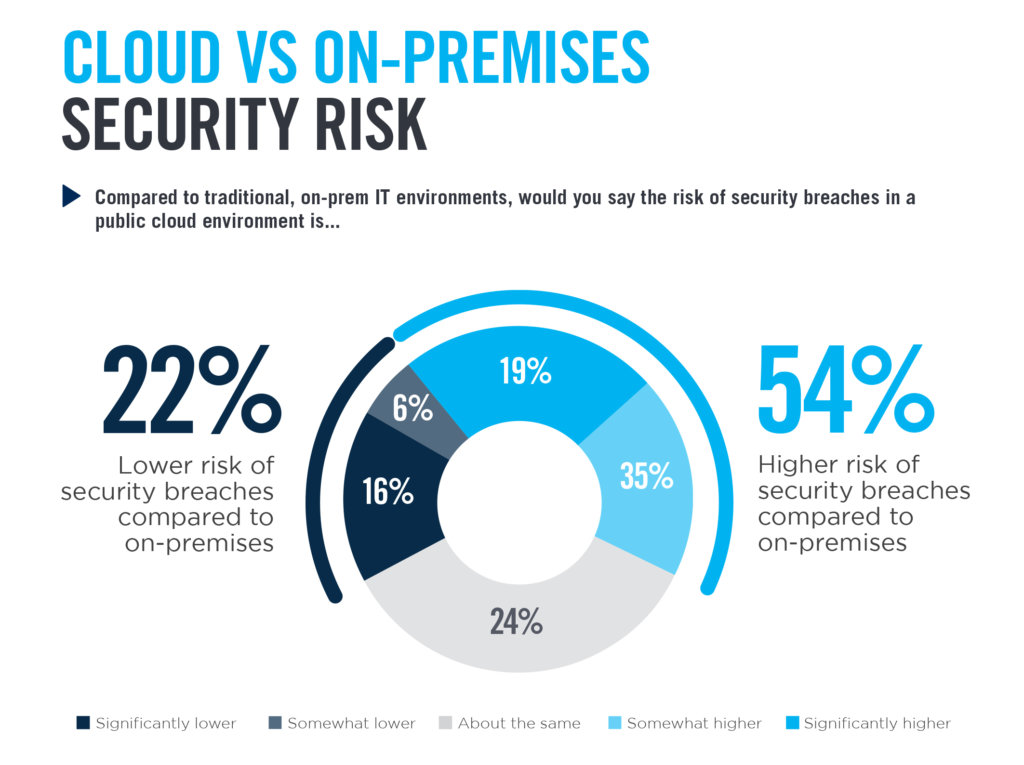
When it comes to cloud security, fewer than 60% of organizations employ clear security policies for developers and only a quarter of those enforce them. Using the cloud has its benefits, but it also opens you up to more vulnerabilities. DevOps must have clear guidelines regarding security during the development cycle for your organization to be proactive about those potential issues.
Unlike traditional computing, the cloud is confusing and messy. It’s a journey toward security and compliance that never really ends. That said, there are some basic things every DevOps professional dealing with cloud tools and environments should know and apply.
The majority of enterprises today employ multi-cloud infrastructure, often using more than one major cloud infrastructure provider. Each platform comes with its own set of native security tools designed to secure the services provided by that specific cloud platform. As the number of cloud providers and solutions employed grows, so does the flood of alerts, notifications and errors in multiple logs. This all means a lot of overhead in determining which risks and threats reported are actually worth following up, and demand the development of a threat modeling approach to each.
The alternative is external, specialized security services that have a vested interest in working with all cloud services, whether they are giants like AWS, Google Cloud, and Microsoft Azure, or small new services.
These services focus on saving you time and effort in managing multiple dashboards and monitoring systems. As such, they aim to integrate with every cloud service and platform out there to reach the widest range of clients. This makes them the ideal solution for centralized cloud security management, even if you’re using a single cloud platform.
It is no secret that misplacing secrets can lead to catastrophic events. Uber had 57 million records compromised due to a security breach, which was likely a result of secrets being uploaded to a code repository.
DevOps and developers concern themselves with speed and efficiency when designing their pipelines. Security is a concern often left to InfoSec teams and IT departments. When developing, your mind is on your product and client security, not the security of your cloud tools. This can lead to cloud credentials being lost, leaked, exposed, and misused.
The most important thing you can do is educate employees regarding the importance of securing credentials. Once awareness is there, teach good security hygiene and enforce it. Rotate keys and passwords, and make sure they are strong and not easily brute-forced. Warn employees about phishing and teach them to recognize phishing attempts.
But don’t rely on education alone. To err is human, and humans will mess up. In fact, Gartner Inc. estimates that up to 95% of cloud breaches occur due to human errors such as configuration mistakes. To protect your cloud secrets from these errors, be sure to have secret scanning integrated into your CI process.
Often brought on by lack of proper training, vulnerable configuration files are akin to storing gas canisters next to open fire. Sooner or later it is going to explode in your face. Who hasn’t configured access privileges to be public “Just while you get it to work” and then forgot about it? Probably not you, but you know someone who has. In fact, nearly half of scanned CloudFormation (AWS Infrastructure as code) configuration files have misconfigurations. Which means that is fairly common practice.
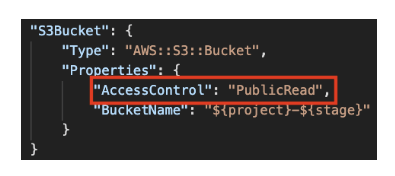
Sometimes you need to set some read access to the public so as to efficiently check if something works correctly. And sometimes, through no fault of yours, you’ll forget about it. Configuration is naturally error-prone, but there are steps you can take to mitigate that. You could scan configuration files manually, but an automated tool is by far the superior approach. Our brain isn’t very well suited to quickly scan documents for errors, but computers are!
The easiest low-effort approach is to give everyone access to everything, and just assume they know what they are doing. But not everyone knows what they are doing, and even if they did, people make mistakes. Employing the least access privilege principle you greatly reduce the areas in which errors can take place.
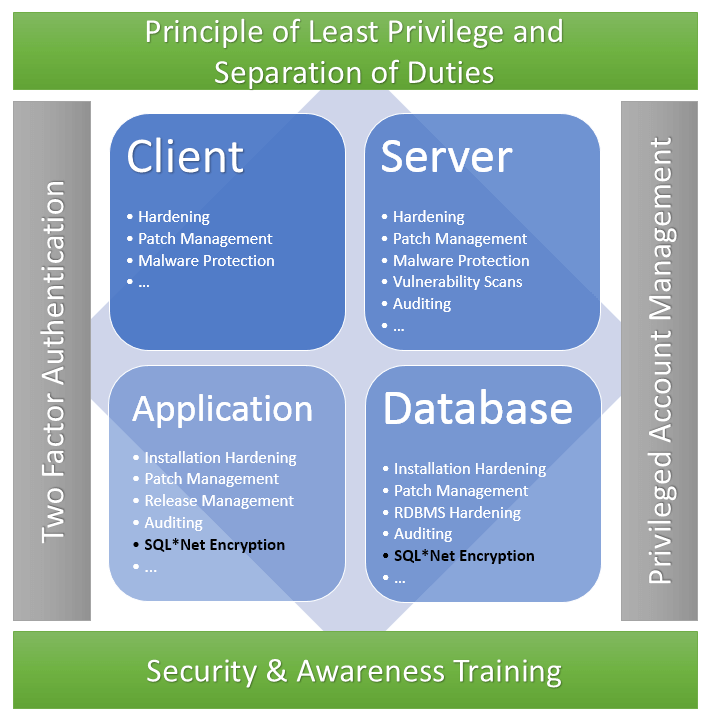
Here is a list of things you could do to reduce access privilege, but it is far from exhaustive and I encourage you to explore more:
Privilege access management solutions can automate a lot of these processes. These include monitoring, auditing, and enforcing compliance over the full lifecycle of privileged sessions. PAM implementations can also allow for easy increase or decrease of access privileges on the go, making sure to maintain the least access privilege model over time.
“Start now, optimize later” is a fine approach when talking about performance, product design, or even code. But when it comes to security, later can be too late. Moving your security protocols sooner rather than later in the CI/CD cycle helps be proactive in maintaining your security. It also dramatically reduces the issues with non-compliance and misconfiguration.
Continuous security is a method by which security is tested throughout the development process, keeping the development process agile and allowing developers to promptly respond to any issues found.
Without implementing both reactive and proactive approaches to security organizations cannot hope to scale on the cloud without compromising security. By shifting compliance and security left organizations can get ahead of the curve and ensure their ability to scale when needed.
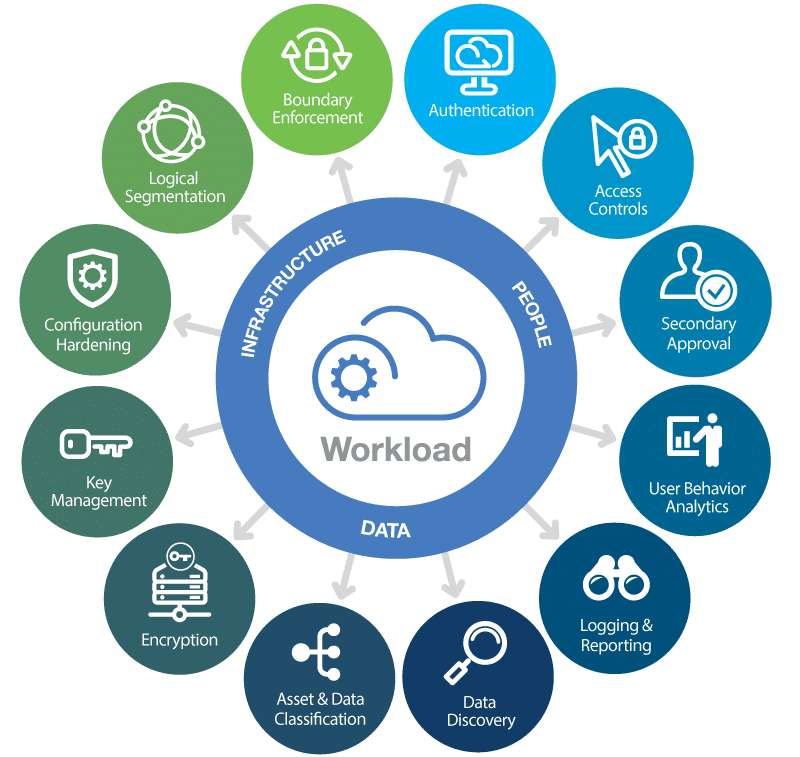
You want to make sure access is granted only to those who need it. Whether that is through revoking access privileges to developers or making sure that configuration files are properly restrictive. Furthermore, as your organization’s cloud usage scales, it will become impossible to keep everything configured probably, and you must employ automation tools such as PAM, secret scanners, and configuration auditors.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions