Protecting secrets throughout the SDLC with SpectralOps
This whitepaper will review the dangers of secret leakage, the challenges in protecting secrets in the SDLC, and strategies for secret leakage mitigation.
Secure your CI/CD using just one line of code in your Travis CI workflow and enjoy mind-blowing scan speeds and maximum security.
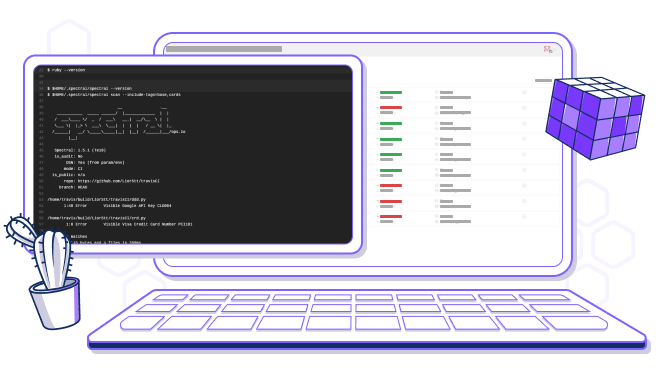

Shift-left your Travis CI security, and integrate Spectral directly into your CI/CD pipeline. Enforce policies and detect security issues in real time.
Enjoy one line of integration that performs a complete scan, controls build status and mitigates vulnerabilities with ever-green updates and no maintenance.
Zero-copy and no data sending from your CI — no special privileges required in order to start.
Mitigate vulnerabilities and Travis CI security with native integration using JUnit reports, JSON, and SpectralOps.
language: ruby
install:
# preflight is a tool that makes sure your CI processes run securely and are safe to use.
# To learn more and install preflight, see here: https://github.com/SpectralOps/preflight
- curl -L "https://get.spectralops.io/latest/x/sh?dsn=$SPECTRAL_DSN" | preflight run
- $HOME/.spectral/spectral --version
script:
- $HOME/.spectral/spectral scan --ok
Spectral allows you to discover, classify, and protect your codebases, logs, and other assets with ease.
Leverage hundreds of custom detectors and proprietary machine learning models to detect and mitigate security vulnerabilities in code, configuration, and data.
Build your own custom detectors, custom workflows using the full power of the Spectral engine, seamlessly in your CI/CD pipelines.
Enjoy faster feedback times in your CI which provides better experience and contributes to lower costs, while connecting with SpectralOps for alerting, and security orchestration.

This whitepaper will review the dangers of secret leakage, the challenges in protecting secrets in the SDLC, and strategies for secret leakage mitigation.

The company’s leadership felt confident in their existing security tools and measures taken. They believed the company had adequate defenses in place to protect the company’s IP (intellectual property) and private information against external attacks.

How safe are your passwords? How secure are your API keys? Are you sure your CI pipeline is configured using the best security practices? One of


Contact us to get your questions answered. You’ll get a free account, and code protected.